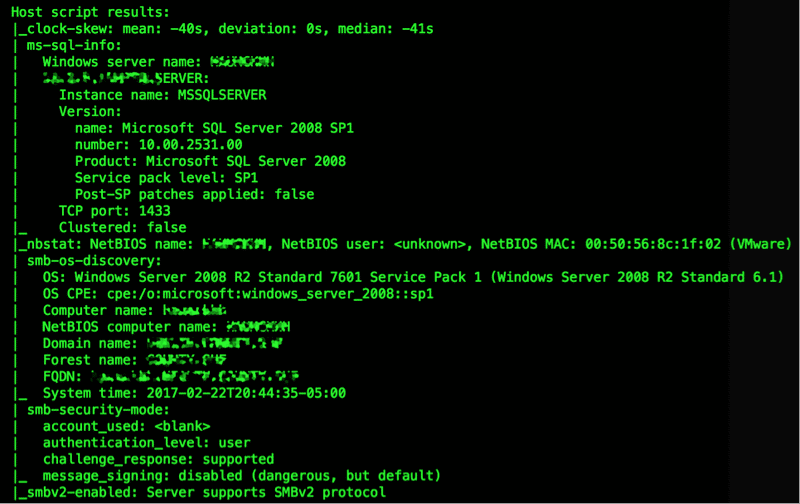
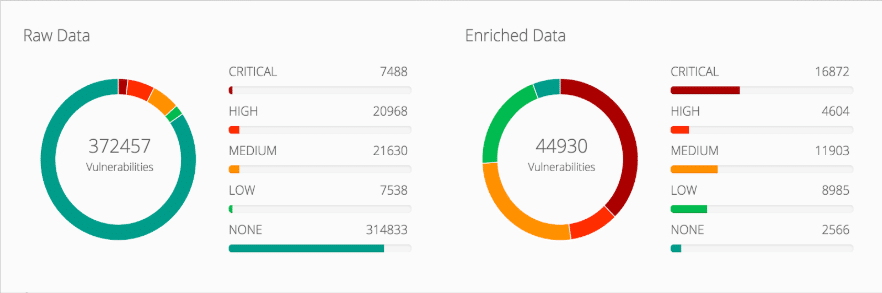
Threat and Exposure Research
Buyer’s Guide for Evaluating Cyber Threat Exposure Management (CTEM) Tools
The Problem with Vulnerability Assessment Scanners If you’re reading this post, chances are you’re looking to take the next step…
All Threat and Exposure Research articles
-
Peer-Reviewed Proof: Exposure Management Saves Lives
A ransomware attack hits a hospital. Systems go dark. Lab results can’t be processed. Pharmacy requests stall. CT scans become…
-
You Asked. We’re Building. What’s Coming to NopSec in 2026
Your feedback shapes our roadmap. Here’s how we’re solving the problems you’ve told us about most. I’ve lost count of…
-
What We Shipped in 2025: A Year of Fixing Less and Securing More
“We have 200,000 critical vulnerabilities. Where do we even start?” That question drove everything we built this year. In November,…
-
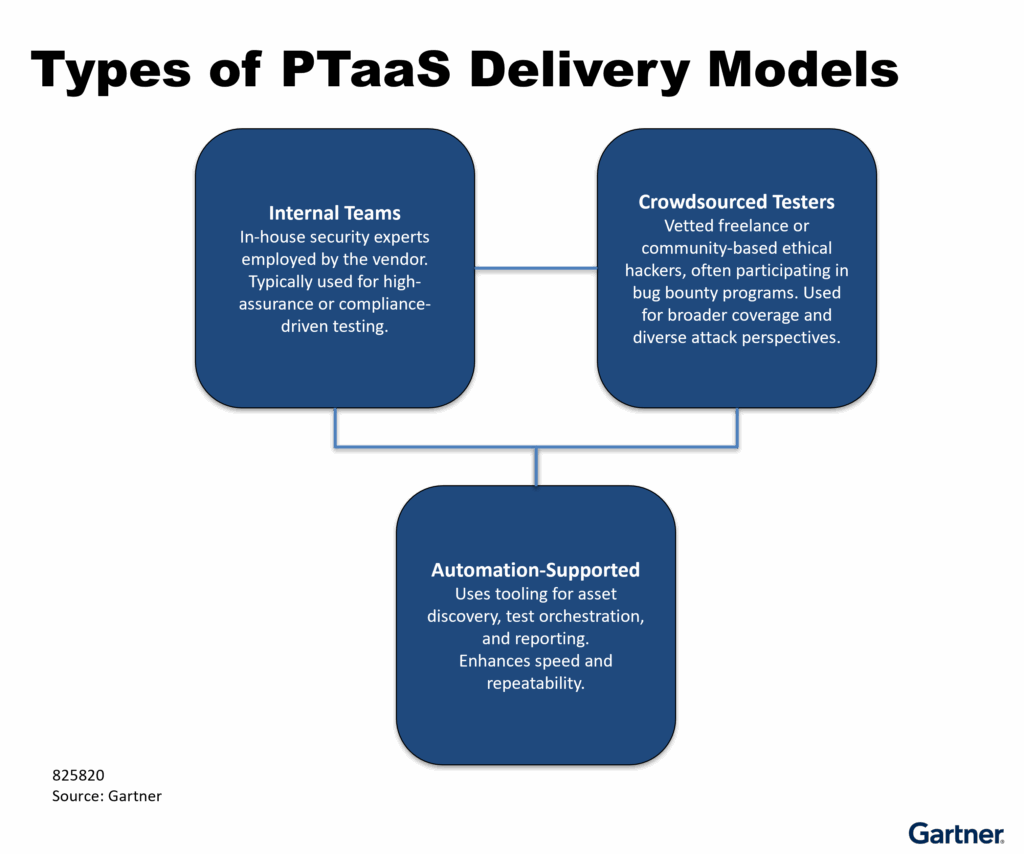
The Manual Annual Pen Test Is Dead. Long Live Continuous Automated Adversarial Emulation.
For decades, the cybersecurity industry has relied on a comforting ritual: the Annual Penetration Test. It goes something like this:…
-
CTEM: The First Proactive Security Innovation in 20 Years
Note: This article was originally published on LinkedIn on February 14, 2024. SUMMER 2021 It was in the summer of…
-
How Pentesting Fits Into a 2026 Security Game Plan
Turn end-of-year testing into next-year strategy with CTEM and continuous validation. Year-End, Not Year-Over As 2025 winds down, many security…
-
Speed Is Security: How Financial Firms Limit Exposure with Rapid Remediation
In financial services, trust is currency. Customers expect their institutions to protect sensitive information and maintain uninterrupted service. But when…
-
How Mid-Sized Banks Can Turn Cybersecurity Into a Growth Enabler
Using Continuous Threat and Exposure Management (CTEM) to Protect Digital Transformation Without Slowing Innovation Imagine launching a major update to…
-
From Alert Fatigue to Strategic Impact: A Conversation with Lisa Xu, CEO of NopSec
Vulnerability management is a crucial practice for maintaining your organization’s security. But many organizations are overwhelmed by the operational burden…
-
What’s the Return on Investment of a Managed Vulnerability Management Service?
From Cost to Confidence: Rethinking ROI in Vulnerability Management Maintaining a robust vulnerability management program is essential for protecting your…
-
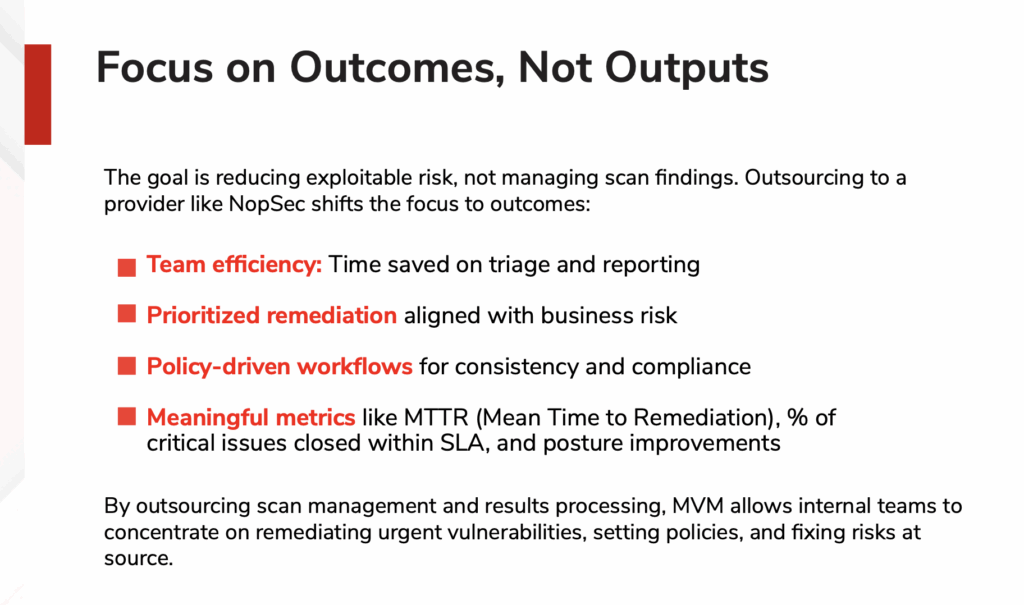
Security Outcomes, Not Operations: Prioritize Risk Reduction
Security Teams Are Under Pressure from All Sides The modern security landscape is relentless. Threats are increasing in sophistication, cloud…
-
Say Hello to WappSnap
From time to time we find ourselves in a situation where the tools we rely on fail to serve our…
-
URGENT ALERT: SharePoint Zero-Day CVE-2025-53770 Demands Immediate Action for On-Prem Servers
The clock is ticking for federal agencies, and a critical vulnerability in Microsoft SharePoint Servers, dubbed “ToolShell,” is actively being…
-
The CVE Wake-Up Call: Why It’s Time for a Decentralized Future in Vulnerability Intelligence
The MITRE CVE Crisis: A Near Miss with Major Implications A couple of weeks ago, the cybersecurity world came dangerously…
-
Beyond vulnerability-based attacks: Identity-based attack path management (APM)
As many as you know, I have been involved in penetration testing since the beginning of my career. It is…
-
Attack Path Mapping: The Future of Vulnerability Management
In today’s dynamic threat landscape, relying solely on Common Vulnerabilities and Exposures (CVEs) to assess the exposure and the likelihood…
-
Top Trending CVEs of May 2024
It’s May, baseball is in full swing and schools are nearly out for summer vacation. This month we take a…
-
Top Trending CVEs of April 2024
April is here, spring has arrived and everyone in the lower 48 of the United States got to witness a…
-
Top Trending CVEs of March 2024
March may be absolute madness for the NCAA and people in bunny suits, but it was a fairly quiet month…
-
Top Trending CVEs of February 2024
February 2024 is off to a ripping start for security research. This month we’re focusing on a piece of open…
-
Volt Typhoon’s Chinese-State Sponsored Attack on U.S. Critical Infrastructure
The U.S. government this week said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some…
-
Top Trending CVEs of January 2024
Happy New Year! We open up 2024 with an interesting mix of vulnerabilities, some of which have been patched for…
-
Top Trending CVEs of December 2023
Happy Holidays! As we close out 2023 we do it with a bit of deja vu (depending on how sharp…
-
Top Trending CVEs of November 2023
The holiday season has officially arrived, but that hasn’t slowed down security research. November featured some seriously cool exploits and…
-
Top Trending CVEs of September 2023
September was an exciting month for NopSec as we hosted our Customer Advisory Board meetings in New York City. Thanks…
-
Top Trending CVEs of August 2023
Summer is slowly cooking everyone into air conditioned spaces as vacations wind down and school winds up. August featured some…
-
Top Trending CVEs of July 2023
July was a busy month for vulnerability research. We had the opportunity to be picky about our curated selection of…
-
Top Trending CVEs of June 2023
It’s finally summer! That means kids are out of school and vacations are in full swing, that includes Security Researchers….
-
Top Trending CVEs of May 2023
May was a rather quiet month for security research, but an excellent write up filtered to the masses from the…
-
Top Trending CVEs of April 2023
April was a busy month for Microsoft. Patch Tuesday introduced critical Windows fixes to address a pair of remote command…
-
Top Trending CVEs of March 2023
In March 2023, security researchers identified a number of critical vulnerabilities that could be exploited by attackers to gain access…
-
Top Trending CVEs of February 2023
In this month’s trending CVEs we have a number of patches released by Microsoft to address critical vulnerabilities identified in…
-
Top Trending CVEs of January 2023
Happy New Year! In this month’s trending CVEs ManageEngine takes the top spot with yet another unauthenticated remote command execution…
-
Top Trending CVEs of December 2022
Happy holiday season! December was off the chains, literally. Microsoft released a security update to address a remote command execution…
-
The Case for a ‘Vulnerability Management Token’: A new way to reward vulnerability remediation
November 2022 has not been a boring month indeed! One of the most prominent and powerful cryptocurrency exchange – FTX…
-
Top Trending CVEs of November 2022
Happy Thanksgiving! November was a surprisingly slow month. It’ll be perfect for some light reading over a thanksgiving break. In…
-
Top Trending CVEs of October 2022
Happy Halloween! The October trending CVEs feature another out of bound write of vulnerability being exploited in the wild that…
-
Top Trending CVEs of September 2022
In this month’s edition of trending CVEs, we feature a blast from the past that provides an excellent example of…
-
Top Trending CVEs of August 2022
This month we have five CVEs on the radar. The August 2022 Patch Now Award* this month goes to ManageEngine,…
-
Creating a Vulnerability Management Program – Vulnerability Remediation: More Complex than You Might Imagine
In prior blogs, we’ve spelled out how an organization finds its vulnerabilities and how security teams consider threat intelligence to…
-
Creating a Vulnerability Management Program – Cybersecurity Risk: Why You Need Both Vulnerability and Threat Assessments
In this blog, we’ll add to our cybersecurity considerations the concept of threats and threat intelligence. So far, we’ve looked…
-
Creating a Vulnerability Management Program – Penetration Testing: Valuable and Complicated
Once you’ve started a vulnerability scanning system, you may want to take the next step in identifying vulnerabilities: penetration testing,…
-
Creating a Vulnerability Management Program – Vulnerability Scanners: How They Help Cybersecurity Readiness
Learn how to identify the right vulnerability scanner(s) for your organization’s needs. So far in this series, we have laid…
-
Creating a Vulnerability Management Program – Patching: Take the Panic out of Patching by Managing CVE Threat Overload
Imagine a company that started in early 2012 with a half dozen employees — all working in one office —…
-
Understanding the Difference Between Vulnerabilities and Exposures
The cybersecurity world talks a lot about “common vulnerabilities and exposures” (CVEs) and compiles ongoing lists of them with a…
-
New Security Vulnerabilities: How Should You Respond?
Cybercrime has exploded in growth over the past several years to levels that are stunning to contemplate. To put it…
-
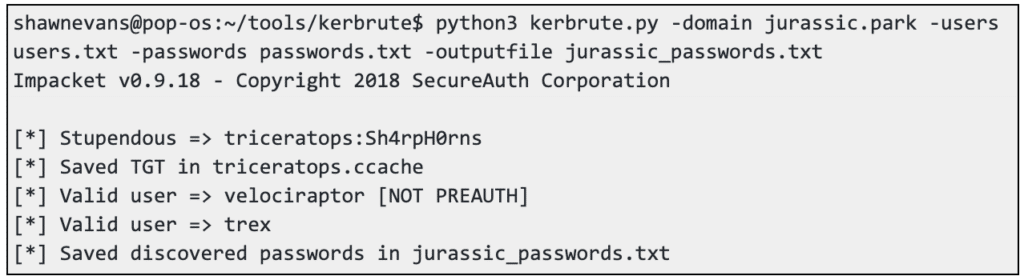
Exploiting Kerberos for Lateral Movement and Privilege Escalation
Introduction Within most enterprise environments, authentication is handled by a central system known as the domain controller. The domain controller,…
-
Why IAM Technology is Critical to Your Vulnerability Management Program
In previous blogs, we discussed Attack Surface Management (ASM) and explained how ASM is critical to your overall Vulnerability Management…
-
Attack Surface Management: Why Your Attack Surface is Critical to Your Vulnerability Management Program
In our last blog, we discussed what Attack Surface Management (ASM) is. Now we will explore the importance of how…
-
5 Reasons Why Attack Surface Management MUST Be Part of Your VA Program
Back in 2019, when I was a research analyst at Gartner, I started to see a monumental shift in how…
-
Vulnerability Management FAQ
What is Vulnerability Management lifecycle? Vulnerability management lifecycle —Discovery, Detection, Prioritization, Remediation, Validation and Program Intelligence. What is an asset? …
-
NopSec – CrowdStrike Joint Solution Brief
NopSec and CrowdStrike are pleased to announce that the two companies have entered into a global technology partnership, integrating NopSec’s leading enterprise Vulnerability…
-
Webinar – Analysis of Verizon 2020 DBIR Report: Vulnerability Management Implications
Analysis of Verizon 2020 DBIR Report: Vulnerability Management Implications Webinar presented by Michelangelo Sidagni. THIS WEBINAR COVERED… • Asset management…
-
Verizon DBIR: Analysis of Verizon DBIR Report
It is that time of the year again! The Verizon 2020 DBIR report is out again – https://enterprise.verizon.com/resources/reports/dbir/ – and…
-
Special Offer – COVID-19
Due to COVID-19, NopSec is empowering remote workforces with a much needed relief for businesses. Take Advantage of NopSec’s Amazing…
-
Vulnerability Management in the time of a Pandemic
As an average person I had to refer to the book I read and to the movie I watch to…
-
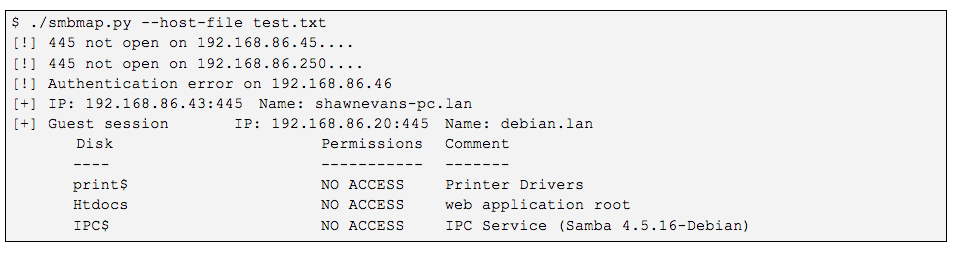
SMBMap: Wield it like the Creator
The tool “SMBMap” was created nearly seven years ago. Originally based on a Python library called PySMB, it has since…
-
International Women’s Day 2020 – NopSec & Mastercard Partnership
In celebration of International Women’s Day 2020, NopSec and Mastercard partner to commemorate women in tech, diversity and product leadership…
-
NopSec Attended Fal.Con Unite 2019 Event
NopSec, a leader in vulnerability and cyber threat management, attended Fal.Con UNITE 2019, CrowdStrike Cybersecurity Conference. We have gathered on…
-
Pentest Findings & Mitigating Controls
What Enables the Kill Chains for Total System Compromise At NopSec my red teaming service team never stops amazing me…
-
Asset Value
Security risk professionals need to assess asset values to add business context to vulnerability management prioritization. NopSec understands that it…
-
Penetration Testing With Shellcode: Hiding Shellcode Inside Neural Networks
NopSec commonly needs to bypass anti-virus / anti-malware software detection during our penetration testing engagements, which leads us to spend…
-
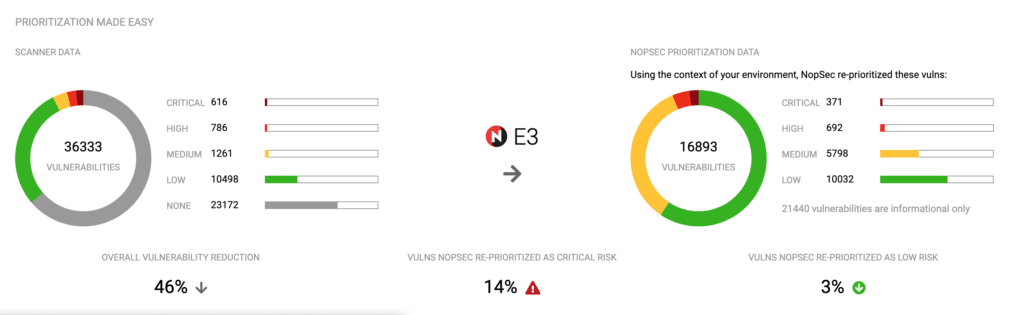
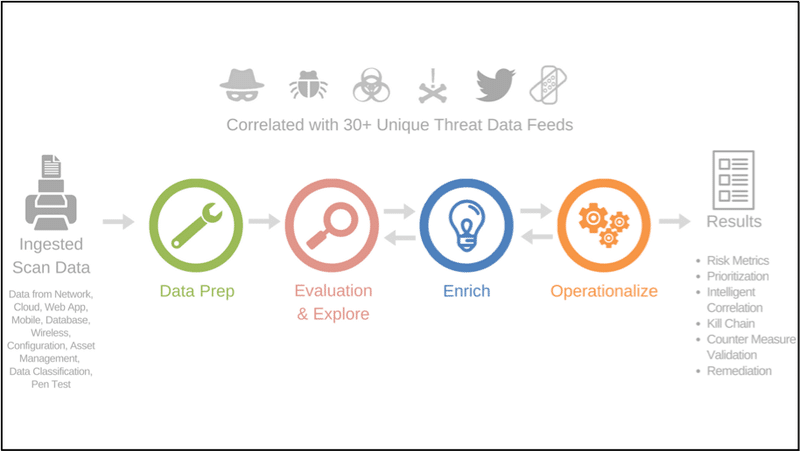
E3 Engine: Engine Microservice That Evaluates, Explores and Enriches Vulnerabilities
Three times the vulnerability prioritization When it comes to vulnerabilities, I always say: “not all vulnerabilities are created equal”. Some…
-
Security Product vs Service Company
The Lines Are Blurring NopSec started as a penetration testing service delivery company at my kitchen table. The company then…
-
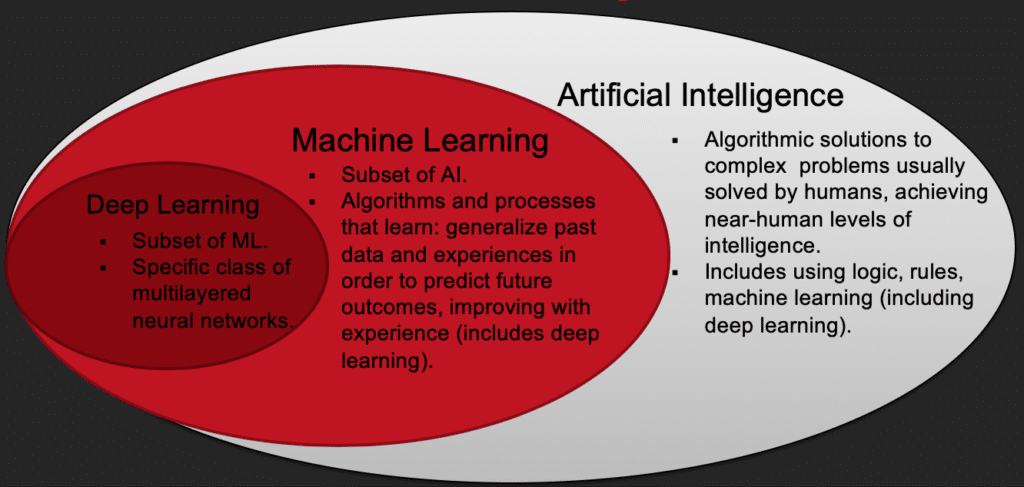
Machine Learning in Cybersecurity Course – Part 2: Specific Applications and Challenges
Spam detection, facial recognition, market segmentation, social network analysis, personalized product recommendations, self-driving cars – applications of machine learning (ML)…
-
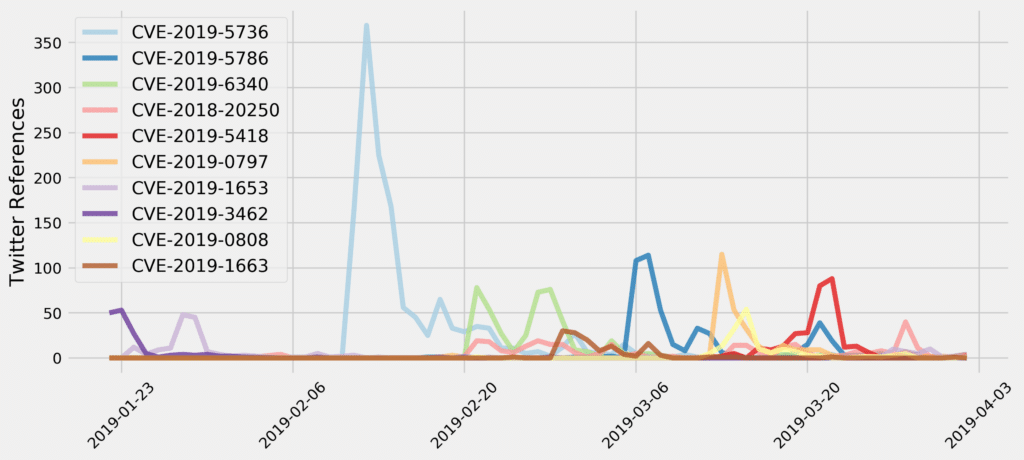
2019 Q1 Social Media Trends
Back in February, we talked about a malicious container ‘break out’ vulnerability in runc (CVE-2019-5736), a universal command-line interface tool…
-
Machine Learning in Cybersecurity Course – Part 1: Core Concepts and Examples
Spam detection, facial recognition, market segmentation, social network analysis, personalized product recommendations, self-driving cars – applications of machine learning (ML)…
-
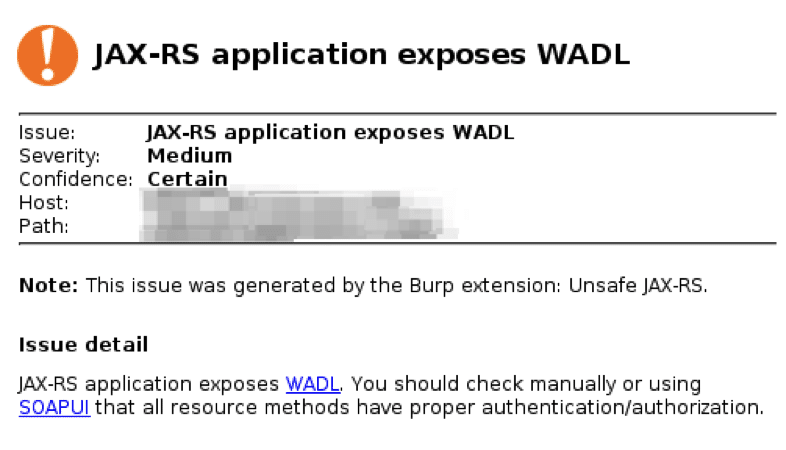
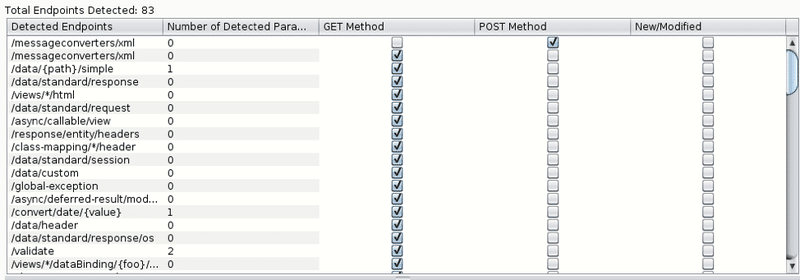
Leveraging Exposed WADL XML in Burp Suite
Recently on a customer engagement, I discovered an application that exposed its Web Application Description Language (WADL) XML that describes…
-
NopSec Accelerates Enterprise Growth And Appoints Three Industry Veterans To The Board Of Advisors
NopSec Inc, a leader in vulnerability prioritization, remediation workflow automation and breach prediction announces the appointments of three new Board…
-
How we mitigated CVE-2019-5736 for Unified VRM – Docker Runc Vulnerability
tl;dr CVE-2019-5736 is a runc vulnerability that allows attackers to obtain root access of any host running a docker container….
-
Saving Time in Vulnerability Management
2019 is here and it’s back to the workday routine. As a dad with a Jersey bus commute, mornings are…
-
VRM Wishlist for 2019
At this time of the year, like any other year, the security industry goes back to reflect on itself and…
-
NIST Teams up with IBM Watson AI System to Score Vulnerabilities
The Great News It has been recently reported that NIST, the agency hosting the National Vulnerability Database (NVD), plans to replace its…
-
Threat Exposure Management: The Hacker’s Approach to Vulnerability Risk Management
IT Security Teams spend most of their time putting out fires, and just plain dreading and waiting for the next…
-
Another Year, Another Critical Struts Flaw (CVE-2018-11776)
Will We Learn the Right Lesson This Time Around? A little over a year ago, Equifax announced a huge breach…
-
Musings on the OSCP
I’d like to diverge from our typical blog topics today to discuss the Offensive Security Certified Professional (OSCP) certification, and…
-
Pen Testing Toolkit: White Hat Tools to Improve Web Application Penetration Testing
Many of our clients at NopSec have mature web application security programs with their own internal white hat penetration testing…
-
2018 Top Cybersecurity Threats
It’s a cliché now to declare any year the year of the _____-breach. It’s especially difficult to see around corners…
-
Black Swan Theory: Black Swan Risk Management for Vulnerabilities
The black swan theory grew out of a metaphor that referred to something that didn’t exist at one point. When…
-
IANS 2018 New York Information Security Forum
On Monday, March 19th, NopSec’s Co-founder & CTO, Michelangelo Sidagni will be speaking at this year’s IANS New York Information…
-
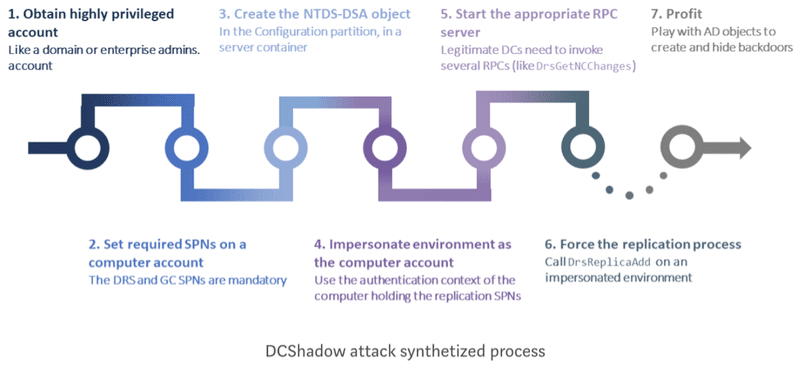
In the DCShadow: How to Become a Domain Controller
I have always been fascinated by lateral movement attacks possible within Windows Active Directory environments. Hosts are compromised; credentials extracted;…
-
Python for Pentesters: 5 Python Libraries Every Pentester Should Be Using
As a penetration tester who uses Python in virtually all engagement, here are the top 5 python libraries that I recommend…
-
Pen Testing Toolkit: Tools & Antivirus Software Evasion Techniques
Antivirus software is one of the oldest and the most ever present security control against malware and various types of…
-
Fighting the War with the Right Weapon: Countering Complexity with Automation
Here at NopSec, we have always been fascinated with automation. It has been a focus of ours since the beginning…
-
CIS 20 Controls: Utilizing CIS 20 Critical Controls for Vulnerability Prioritization
CIS 20 Security Controls represent one of the reference frameworks of the most critical controls an organization can implement to…
-
Knowledge (Data) is Power in Vulnerability Management
Data is power virtually everywhere, and it’s all about how you utilize that information. In business, you can use data…
-
Penetration Testing Tools: Top 6 Testing Tools and Software
Penetration Testers (aka ethical hackers) use a myriad of hacking tools depending on the nature and scope of the projects they’re…
-
The True Cost of A Great Penetration Test
If you asked car salesmen from different dealerships the question, “How much does a great car cost?” you’re guaranteed to…
-
Top 3 Cybersecurity Problems That are Solved with E3 Engine and Unified VRM
We’re proud to build products IT Security Teams actually need and use on a daily basis. We’re a company started…
-
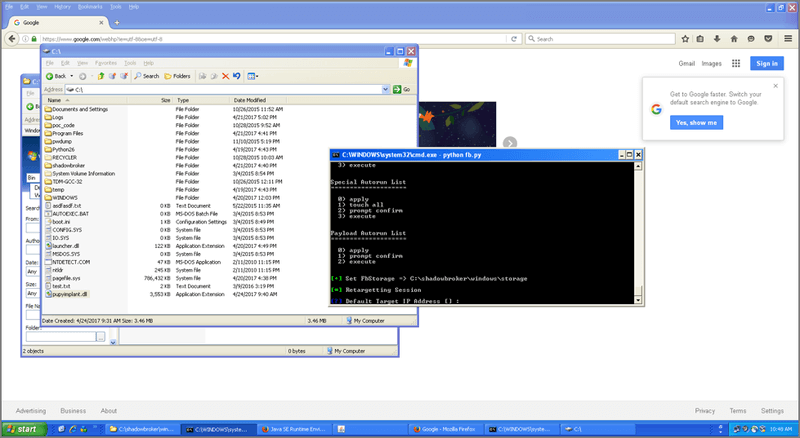
The Shadow Brokers-Leaked Equation Group’s Hacking Tools: A Lab-Demo Analysis
According to the The Register’s article, last week we started assisting to the widespread exploitation of The Shadow Brokers’ leaked Windows…
-
3 Dangerous Myths About DDoS Attacks
Distributed denial of service (DDoS) attacks are a growing but frequently misunderstood threat in the cybersecurity world. Defined generally, a…
-
Doing Diversity Right: Turning Employment Obstacles into Opportunities
Blind assumptions about online security are not the only assumptions that demand attention in the cybersecurity industry today. An article…
-
Top 5 Cybersecurity and Computer Threats of 2017
The year 2016 will be remembered for some big moments in the world of cybersecurity: the largest known distributed denial…
-
2017 Outlook: Remediation Trends
Each year, NopSec conducts a survey of IT and cybersecurity professionals to glean a snapshot of the current state of…
-
Your Money or Your File(s)!
Growing up as a kid in the 80’s ransom used to be a simple thing. A bad person with a…
-
Growing Cyber Threats to the Energy and Industrial Sectors
Remember Shamoon, the malware that disabled some 35,000 computers at one of the world’s largest oil companies in 2012? If…
-
Social Engineering – The Mental Game, Part II.
Now, let’s talk technical. Malicious executable are used to deliver a payload to a victim. These can be very technical…
-
Social Engineering – The Mental Game, Part I.
The first thing that all organizations need to understand is why social engineering works. In many cases organizations, security professionals,…
-
Six Effective Ransomware Risk Reduction Strategies
Businesses, governments, and consumers alike need to be aware of ransomware – a type of malware that can inflict serious…
-
NopSec Report Finds Organizations Use Inadequate Risk Evaluation Scoring System
NopSec released a featured annual report, “2016 State of Vulnerability Risk Management.” The report reveals key security threats by industry,…
-
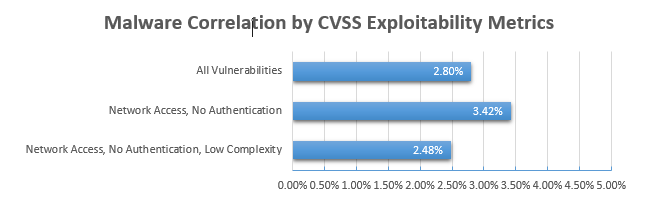
Malware Analysis: Moving Beyond the CVSS Score
Note: This article was updated in June 2022. Here at NopSec, we are all about risk — our number one…
-
Know Thy[self] Environment
Securing an environment is a constant game of cat-and-mouse. Safety measures of all kinds can (and should) be put in…
-
What Matters Most: Remediating Vulnerabilities
Scanning is an important part of a well-established vulnerability risk management program. Vulnerability scanners allow you to identify the threats…
-
Two Key Steps to Stop DROWN…
The information security industry is buzzing about the newest threat, DROWN. According to Drown Attack, “[it] is a serious vulnerability…
-
Vulnerability Management Myths
Automation Strikes Back! There are tons of technologies out there that are trying to “AUTOMATE” every aspect of human life….
-
The Importance of Technology Integration to the Value of an InfoSec product
According to FireEye, a U.S. based provider of next generation threat protection, it takes companies, on average, more than 200 days…
-
Consumers: The Last Best Mile of the Security Perimeter
For consumers and businesses alike, when it comes to keeping private information private your best defense is vigilance; in both…
-
Vulnerability Management and the Road Less Traveled
When I started my career as a penetration tester, the name of the game was all about breaching the external…
-
Healthcare Data is the Next Vulnerable Target for Hackers
Another day, another hack. And not just any old hacking incident, but one involving yet another healthcare provider, only demonstrating how…
-
Help, My Car Got Hacked and the Internet of Things
The recent recall of 1.4 million vehicles by Fiat Chrysler has raised many questions and concerns after researchers discovered a security vulnerability…
-
Vulnerability Risk Management: Making the Move beyond Compliance
Information security professionals have a single core mission: to understand technological risks and take the necessary steps to protect information…
-
Threat Intelligence: one size does not fit all
Literally a flood of lines have already been written about Security Threat Intelligence and its uses, so I would not…
-
Active Directory Authentication and Asset Sync
Enterprise organizations need vulnerability risk management solutions that integrate with the existing authentication and asset management infrastructure. Unified VRM has…
-
DevOpS and Remediation Task Management
Lately a lot of attention has been directed towards the “DevOps” or “SecOps” disciplines and for good reasons. According to…
-
Vagrant Boxes: Private Vagrant Box Hosting With Easy Versioning
At NopSec, we are using vagrant and packer to spin up local dev environments and build our instances across the various hypervisor and cloud…
-
Counting Vulnerabilities. Assessing Threats. Frictionless Remediation
A couple of days ago I read an interesting article in the Tenable Network Security Blog — here — where…
-
State of Insecurity: Challenges to Addressing Discovered Vulnerabilities
Penetration Testing, Red Team Operations, Exploit Development, Vulnerability Management, Brute Forcing, Advanced Persistent Threats and even BEAST, CRIME, Zeus, Code…
-
Linux Ghost Vulnerability: A GHOST in the….Linux….Wires
Our partner Qualys discovered a new vulnerability nick-named “GHOST” (called as such because it can be triggered by the GetHOST…
-
Customer Experience Case Study for Vulnerability Management
If you haven’t read the book or watched the movie Fight Club, you may not understand this reference. “1st RULE: You…
-
Security Doom Scenarios…..OK….name your passwords’ directory “Password”
Usually I am not particularly a big fan of security doom scenarios, but looking at this week’s security news and…
-
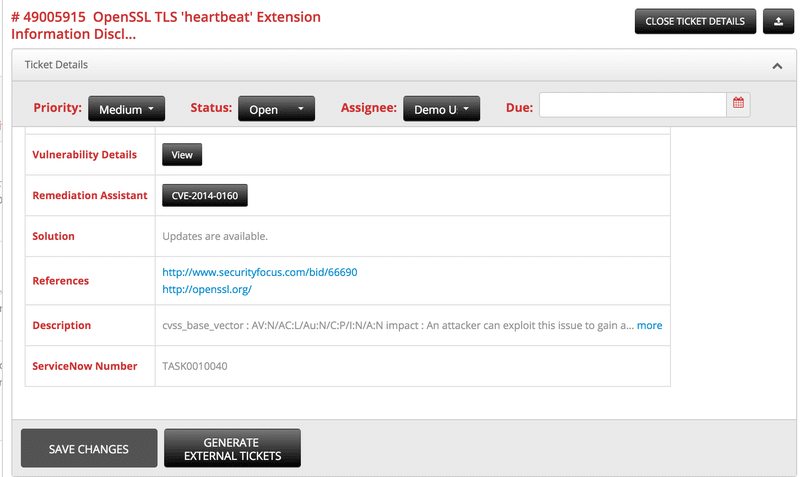
Find the Next Heartbleed-like Vulnerability
Heartbleed (CVE-2014-0160) is a vulnerability with a CVSSv2 base score of only 5.0/10.0. Though its CVSS score is relatively low,…
-
Projecting Your Burp
If you’re a security researcher or penetration tester you’re probably already well aware of the extensive array of tools available…
-
Take Your XSS and POST It
Parameter injection is one of the most common classes of web application vulnerabilities exploited in the wild. This class of…
-
PCI 3, Requirement 11: PCI Penetration Testing and Wireless Security Explained
Understanding and fulfilling PCI 11, Requirement 3 can be daunting, but NopSec is here to help you through it. 11.1…
-
Poodle SSLv3 vulnerability: What it is, how to discover it, how to defend against it
Google security researchers Bodo Moller, Thai Duong and Krzysztof Kotowicz recently uncovered a vulnerability in SSL 3.0 that could allow secure connections to…
-
Continuous Collaboration at Qualys Security Conference
Call it good timing. After all the horrendous cybersecurity news of the past weeks, it feels great about that our…
-
Xen and the Art of Vulnerability Maintenance
It is no secret that hackers have been making the rounds, targeting organizations of all sizes, from national retailers to local financial institutions,…
-
Are the clouds in the sky rebooting?!
If you are like us at NopSec one of the companies that operators on Amazon AWS cloud, this past couple…
-
The Role of Threat Intelligence in Vulnerability Management
Threat intelligence is an increasing popular buzzword in security magazine articles and blogs. It also is becoming more prevalent in…
-
Successful Account Penetration: The Key to a Successful Penetration Test
With the time, effort and resources that companies dedicate to penetration testing, it can be frustrating (at best) to not…
-
Introduction to IT Security Vulnerability Assessments
A vulnerability assessment, also known as vulnerability testing, is the practice of detecting, classifying, prioritizing, and remediating security vulnerabilities in…
-
Lessons Learned from Data Breaches at Universities
No industry is immune to IT security breaches. Recent breaches at Indiana University, Iowa State, the University of Maryland, and…
-
Vulnerability Remediation Process & Management: Why is Remediation so Difficult?
Note: This article was updated in June 2022. Risk Based Vulnerability management is the ongoing practice of detecting, classifying, prioritizing,…
-
The Year Ahead for Vulnerability Management
This is the time of year when companies gaze into their crystal ball and try to discern what lies ahead….
-
The Single Most Important Thing You Can do to Improve Cyber-Security in 2014
According to a reports released by the Information Security Forum and ISACA, cyber-security will continue to be a critical issue for businesses in…
-
The Role of Penetration Testing in Vulnerability Risk Management
Reports in the news make it clear that the sophistication of cyber-attackers continues to evolve. So why do so many…
-
Horizontal Solution or Point Solution for IT Vulnerability Management?
When IBM Security announced availability of its QRadar Vulnerability Manager earlier this year, vulnerability risk management was solidified as an…
-
Penetration Testing in Healthcare
In September the deadline for compliance with changes to the HIPAA rules relating to breaches of unsecured electronic Protected Health Information…
-
Wireless Network Penetration Testing
Cyber forensic investigators report that some of the most complicated and audacious hacks started in two simple ways: either with…
-
Vulnerability Management for Amazon Web Services (AWS)
As the benefits of cloud computing drive increased adoption by businesses, the fastest growing area of public cloud computing appears…
-
Banking and Insurance Regulators Focus on Cyber-Threats
If you are responsible for IT security in the financial services industry, you may have been asked by a regulator…
-
NopSec Recognized as 2013 “Emerging Security Vendor” by CRN Magazine
NopSec was recognized on the CRN Magazine 2013 list of “Emerging Security Vendors” for the second consecutive year. CRN’s Emerging Vendors…
-
Reflection on Black Hat 2013 – a Technical Perspective
As every year the Las Vegas security conferences extravaganza unfolds and then passes leaving a head full of new knowledge…
-
NopSec’s CEO featured in Forbes article about building an Advisory Board
Lisa Xu, Chief Executive Officer at NopSec, knows that an outside perspective is critical to building the company. Lisa recently…
-
Surprise insights from the Black Hat security conference
You may have heard the adage, “The best defense is a good offense.” As Chief Marketing Officer at NopSec, I…
-
The state of IT security at Las Vegas conferences
Wendy Nather is Research Director within 451 Research’s Enterprise Security Program, providing analysis on the current state of security from the…
-
Recommended sessions at Black Hat 2013 Conference
I have been attending the Black Hat Conference in Las Vegas for many years now and I have to admit that the…
-
Embedded Malware: Account Takeovers Multiplying
Robert McGarvey recently covered the topic of account takeover attempts in his regular column in the Credit Union Times. Michelangelo…
-
Vulnerability Management is a Lie
I came across a post by Tony Turner titled, “Vulnerability Management is a Lie” and I could hardly wait to…
-
Achieving SANS top 20 Critical Security Controls with Unified VRM
Recently I got the chance to spend a little more time examining the SANS top 20 Critical Security Controls for…
-
Required Reading for Vulnerability Management Market Insights
Do you ever wish there was a single document that would answer all your burning questions? If you’ve ever moved…
-
Forbes: It’s Not Just Warren Buffett Who Is Bullish On Women
The rationale for this blog post is the Rule of Three and, as noted on Wikipedia, the Latin phrase, “omne trium perfectum”….
-
Is there value in cyber-security degrees?
I came across some news the other day that a local university will start offering a master’s degree in “Cyber-Security…
-
Credibility and Reputation – New Target for Cyber-Attacks
Is there anybody that has not received an email that starts like this, “<Company name> recently experienced a cyber-attack on…
-
VC firms need to find their feminine sides
An industry colleague forwarded me a recent article from Upstart Business Journal titled, “VC firms need to find their feminine…
-
Security Careers: Breaking Barriers
Lisa Xu, CEO of NopSec, was interviewed recently by BankInfoSecurity.com about her career in information security – a male-dominated field…
-
BankInfoSecurity: Overcoming Too Much Data
Last week at the RSA Conference, Lisa Xu and I had an opportunity to sit down with Tracy Kitten, Managing…
-
Credit Union Times: APT Will Get You
In a recent article posted by Robert McGarvey in the Credit Union Times, Threat of the Week: APT Will Get…
-
The importance of implementing security controls
Cyber Security was all over the news recently. Facebook revealed that it was hacked – even though it came out…
-
As big banks and media wise up to cyber threat, New York’s security firms get noticed
Crain’s New York Business, there is an article written by Matthew Flamm that discusses the pervasiveness of cyber attacks and…
-
Executive Order on Cybersecurity
It looks like the Federal Government is getting serious about IT security. “Now our enemies are also seeking the ability…
-
Reduce your odds of needing incident response
It has been hard to keep up with my news alert due to all the IT security headlines. “Hackers in…
-
Reemerging from the Flood
Some of you probably wondered where the NopSec crew and I ended up these days….already tired for blog writing? Not…
-
Another Type of Correlation – Vulnerability Correlation
The other day I was thinking about the concept of “event correlation” embedded into various SIEM products. Security events can…
-
What’s the matter with vulnerability management?
Every day I get tot talk to a lot of infosec professionals and business people regarding vulnerability management. They tell…