Assess Exposure
Remediate Threats
Gain Insight
Identify the vulnerabilities that matter most and expedite the remediation process
Cyber Threat Exposure Management Solutions
Explore the vulnerability management, insight, remediation capabilities of the NopSec platform
Consolidate Your Vulnerability Management Solutions
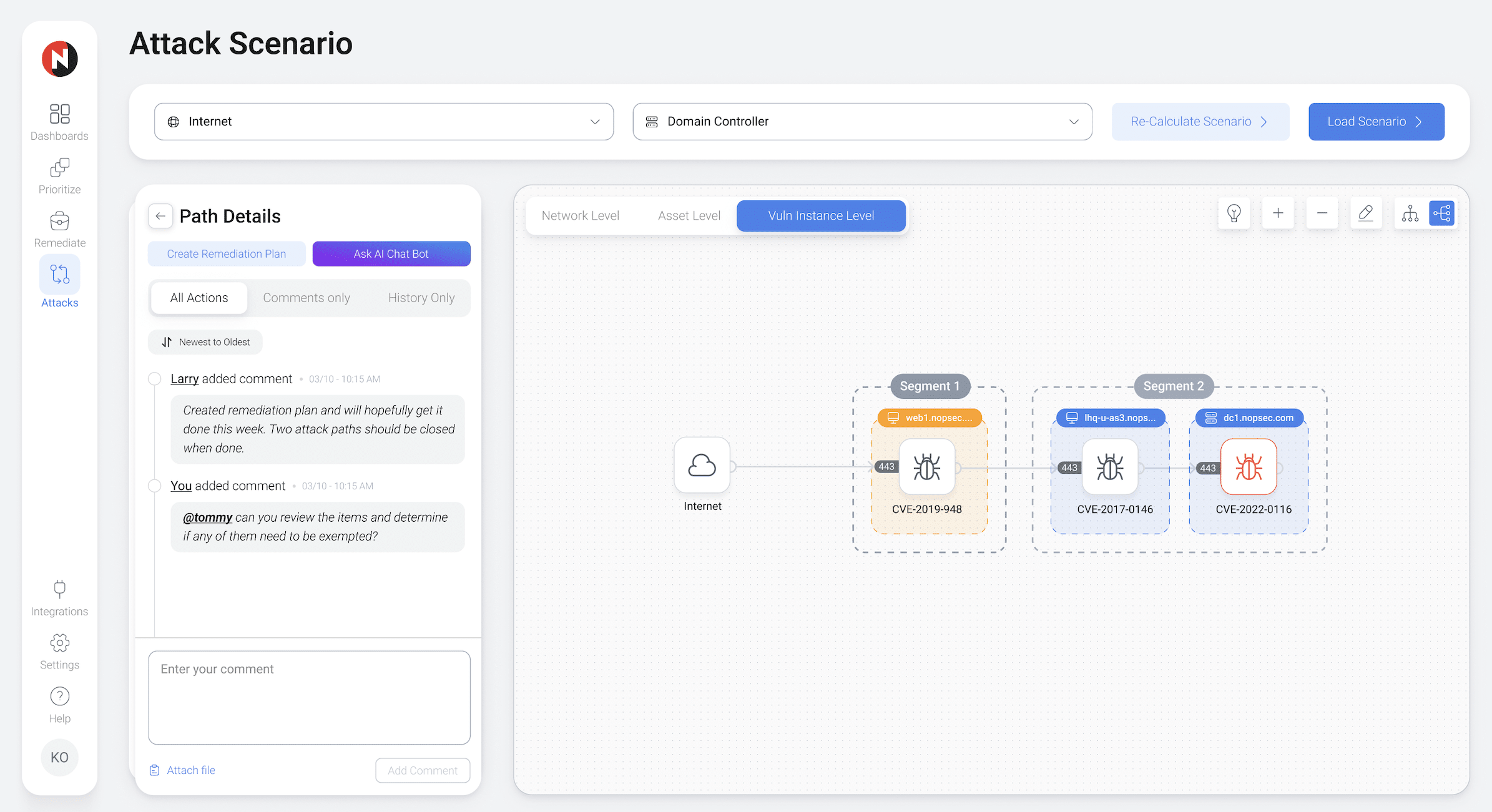
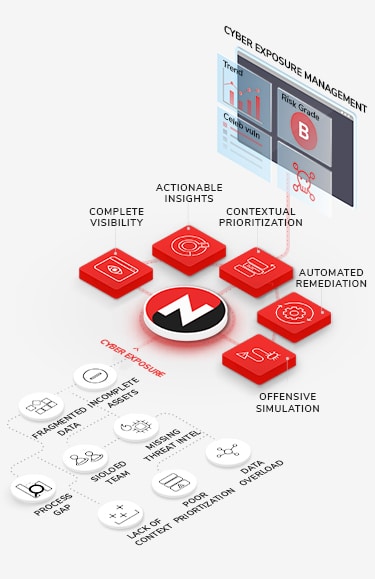
Put an end to disparate workflows and technology. NopSec’s comprehensive platform aggregates vulnerability prioritization, remediation automation, and performance reporting together into one centralized platform. Enable your team to run the entire vulnerability management lifecycle from just one console.
-
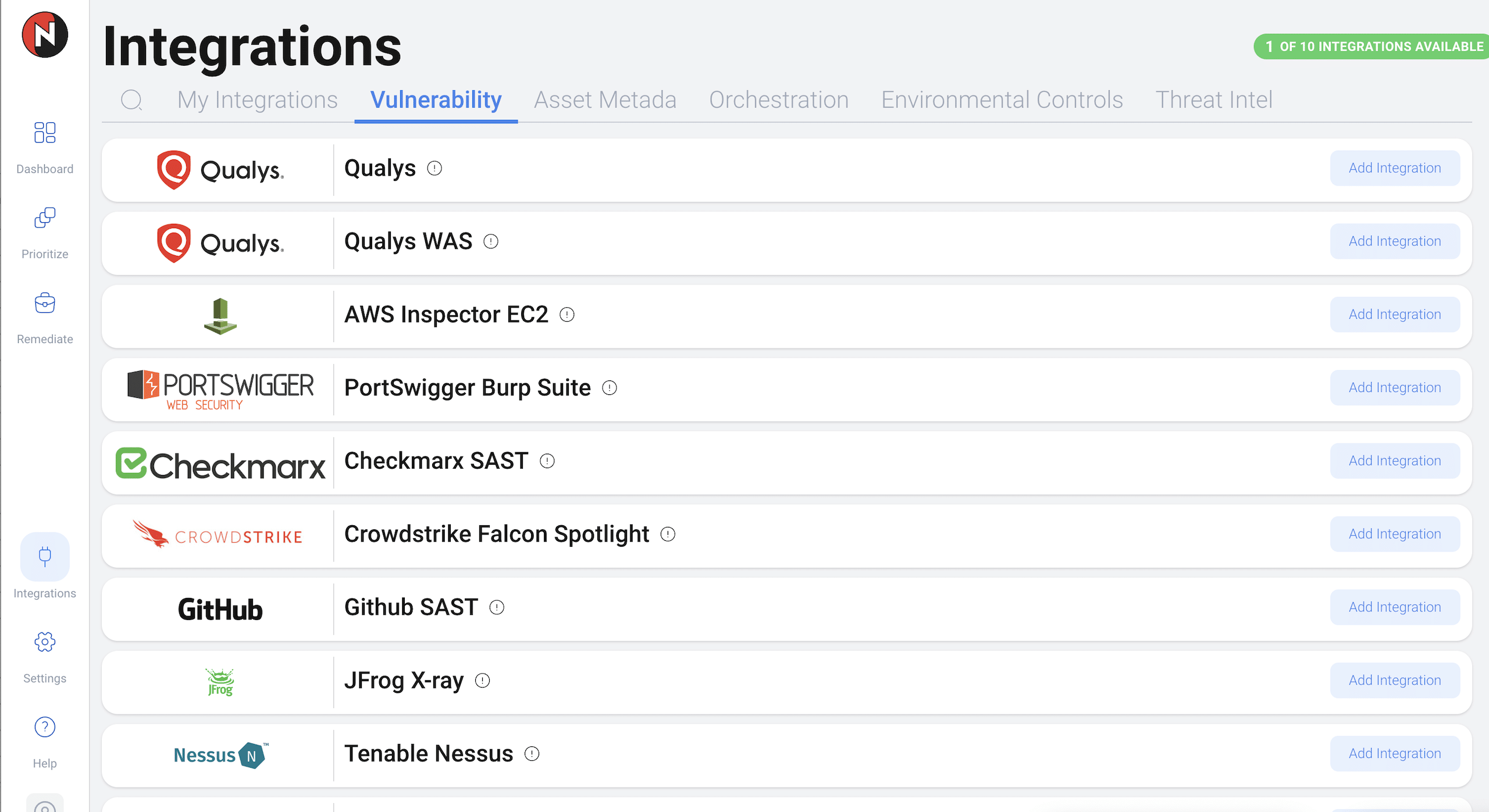
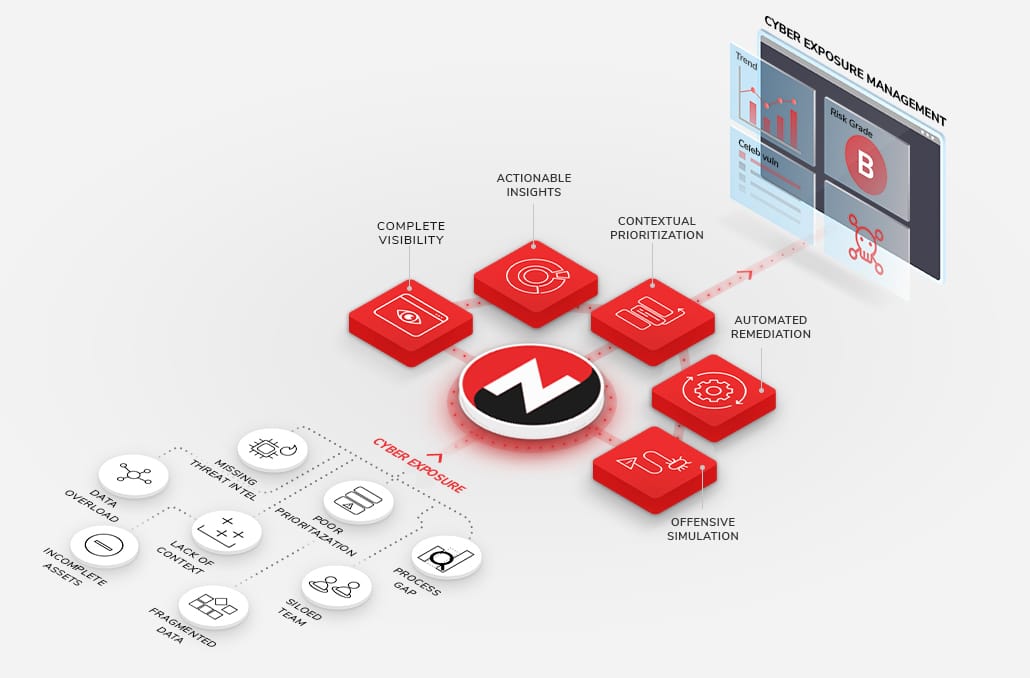
AggregateYou can’t protect an unknown environment. Having complete visibility of your assets and risk in one place is essential to execute a successful Vulnerability Management program. NopSec integrates with leading infrastructure scanners, cloud asset scanners, application scanners (SAST and DAST), and Configuration Management Databases (CMDBs) to provide complete context of your environment.Benefits
- Discover unknown shadow IT assets
- Continuously monitor external attack surfaces
- Break down the silos between IT and cyber asset management
- Detect instances of shadow IT
- Ensure 100% coverage of your VA program
- Prioritize IT assets by business criticality
-
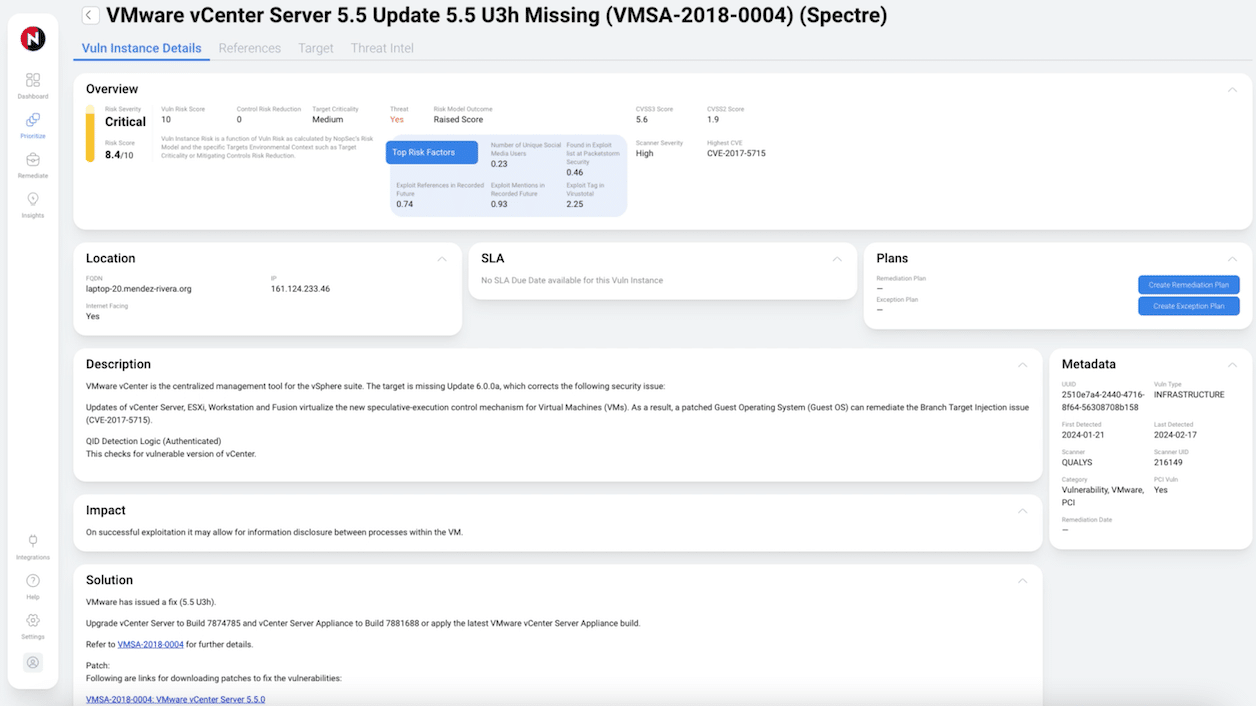
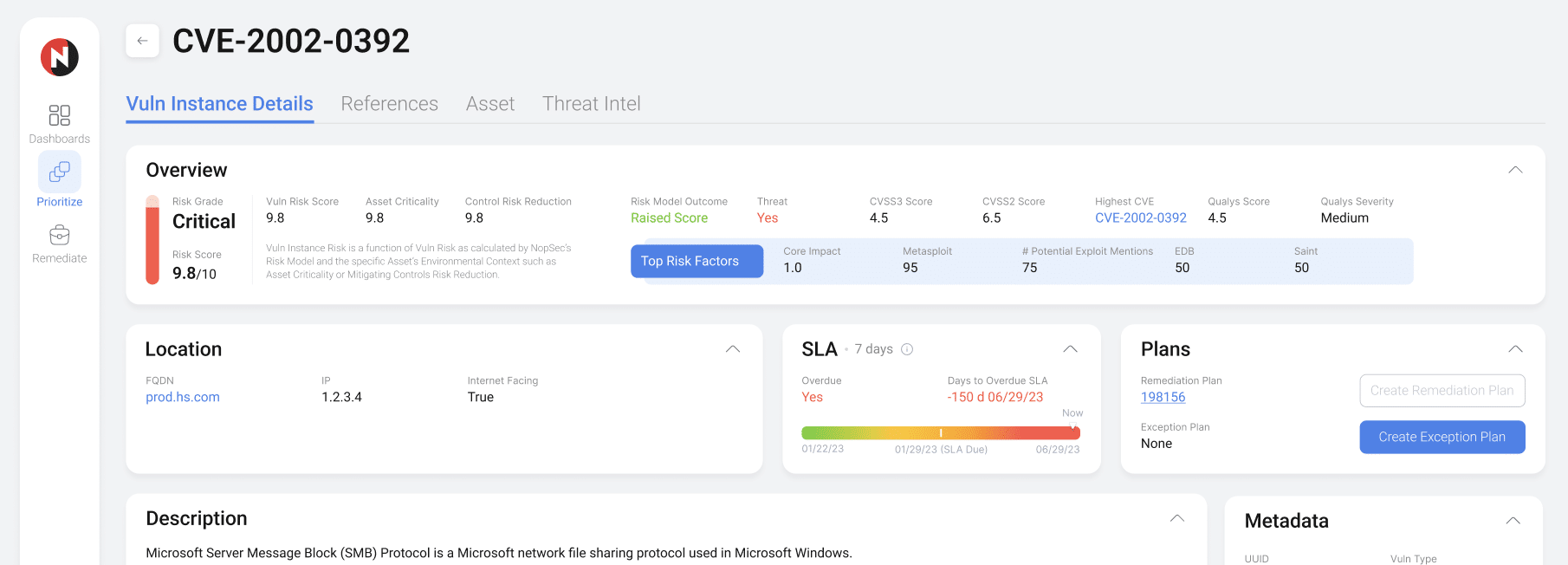
PrioritizeIf every vulnerability is a priority, none of them are. Prioritize vulnerabilities associated with malware and exploit kits, not just vulnerabilities identified with exploits. Focus your remediation efforts with NopSec's patented machine-learning algorithm to surface the highest-risk infrastructure, application, and cloud/container vulnerabilities most likely to be weaponized against you.Benefits
- Liberate yourself and team from tedious data triage in Excel/CSV
- Triage large numbers of vulnerabilities faster
- Cut down time to decision and response
- Align remediation priorities between Security and Ops to reduce MTTR up to 75%
- A single pane of glass for all cyber exposure
- Better align with your IT Operations team
-
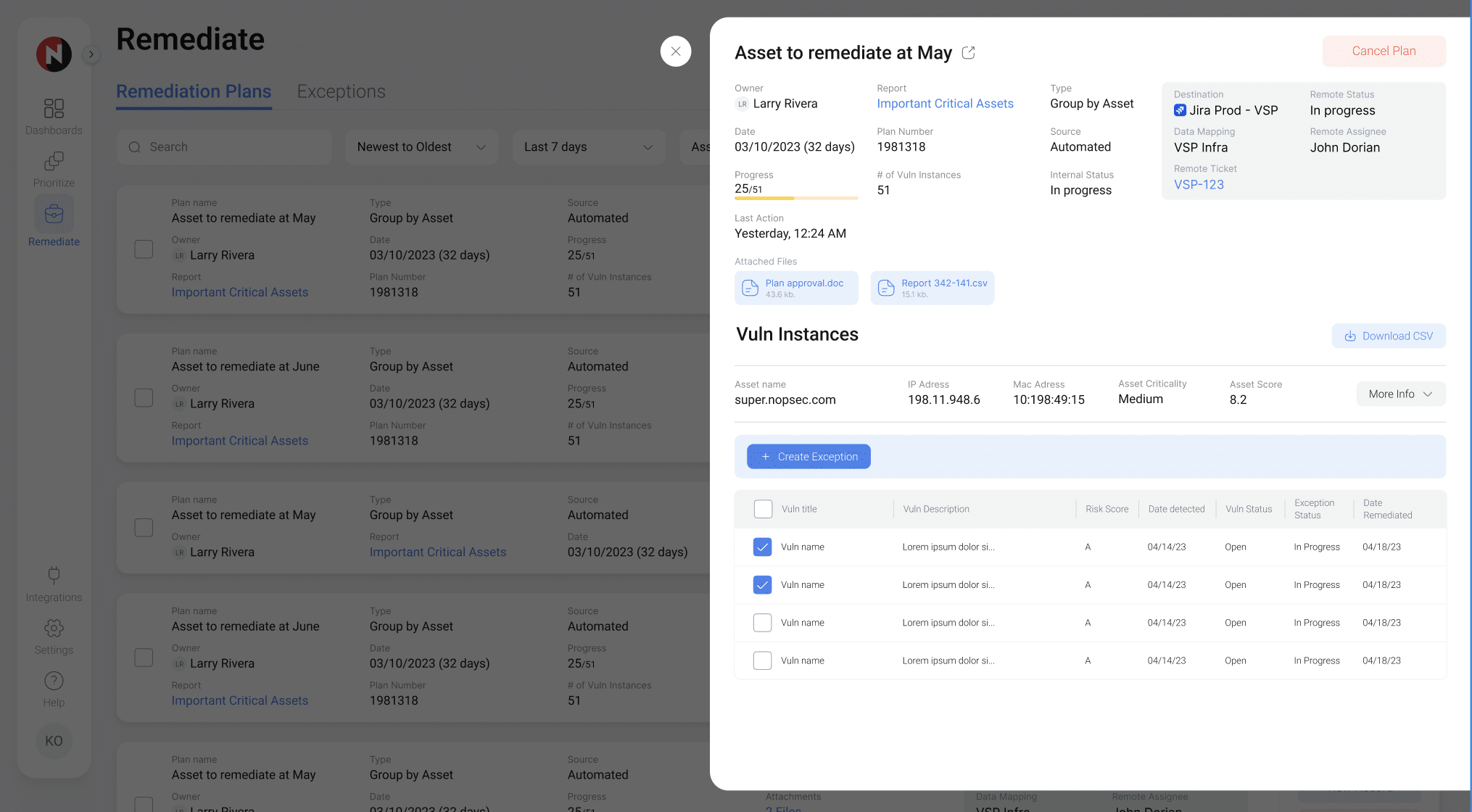
OperationalizeRemediating risks shouldn't be a battle. Siloed processes and lack of alignment kill ITOps throughput. NopSec steamlines Security and ITOps remediation processes with remediation and exception plans, ticket workflow automation, and SLA enforcement. Bi-directional syncing between NopSec and your vulnerability scanners ensures vital security tools report the same status.Benefits
- Help IT streamline patching of vulnerabilities
- Replace manual ticketing with automated creation, assignment, and routing
- Hold teammates accountable to achieve defined SLAs
- Automatically create tickets in your ITSM system of choice
- Support and meet custom SLAs
- Quantify security improvements from remediation
-
ValidateSecurity controls must be validated to know if they work. NopSec's attack path mapping allows Security teams to visually validate the effectiveness of their controls and the effects of their potential remediations on their network. See vulnerabilities, ports, interfaces, and user permissions, along with network connectivity and allowed network paths to prioritize the riskiest attach paths.Benefits
- Quantify impact of security efforts
- Model and quantify the impact of technology changes
- Concentrate efforts on most impactful activities
- Gain a context-sensitive view of risk
- Have greater impact with limited security resources
- Quickly validate prioritized decisions to IT Ops
-
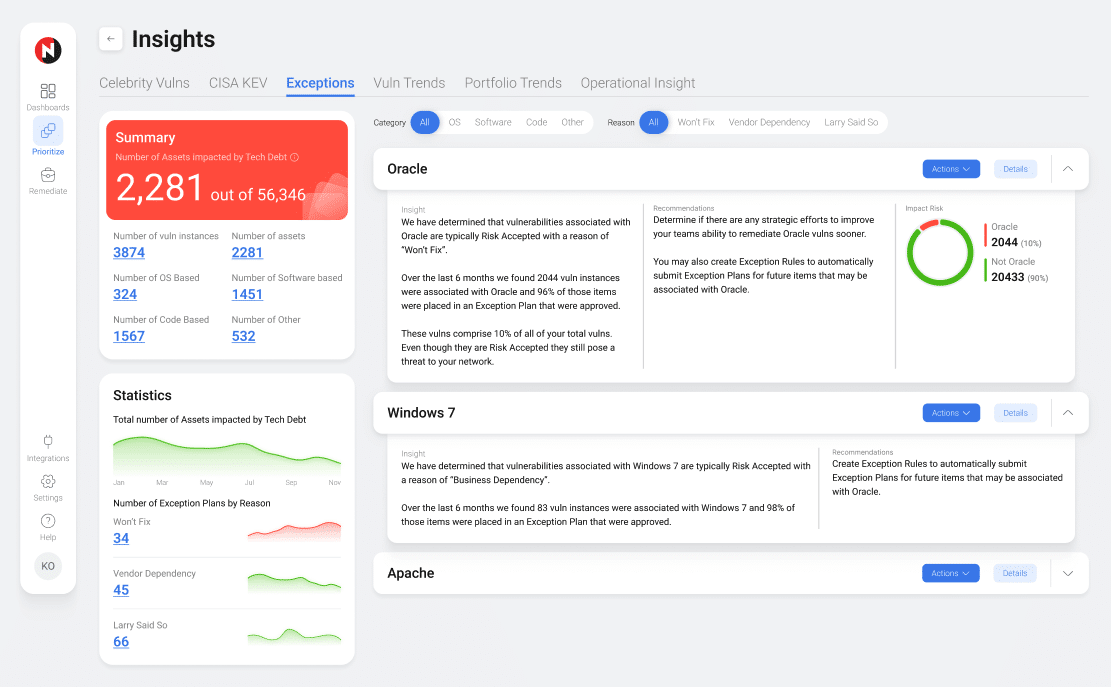
InsightImpact is only as good as your ability to show it. NopSec enables Security teams to benchmark progress, quantify risk remediation, and articulate risk by business line. NopSec provides full-stack reporting that puts your application vulnerabilities next to your infrastructure vulnerabilities. All of this is done in a common language understandable by Analysts and C-Suites alike.Benefits
- View security posture by region, business unit, and more
- Quantify improvements in processes
- Validate security program investment
- Communicate security program status to management and BoD
- Benchmark progress in security posture
- Quickly achieve situational awareness
Awards
Schedule a Product Demo Today!
See how NopSec's security insights and cyber threat exposure management platform can organize your security chaos.