Attack Path Mapping for Security Control Validation
Blindly remediating vulnerabilities without understanding their complete attack path diminishes the confidence of your efforts. With NopSec's attack path mapping, you can enable your team to visually see the "if then" effects of your existing controls and potential remediation decisions. Enhance your contextual understanding and remediate cyber exposure with confidence.
Key Features
- Map out and visualize your attack paths
- Validate the existence and effectiveness of security controls
- Prioritize remediation based on your riskiest attack path
- Enrich environmental context of your assets and controls
Vulnerability Validation Product Features
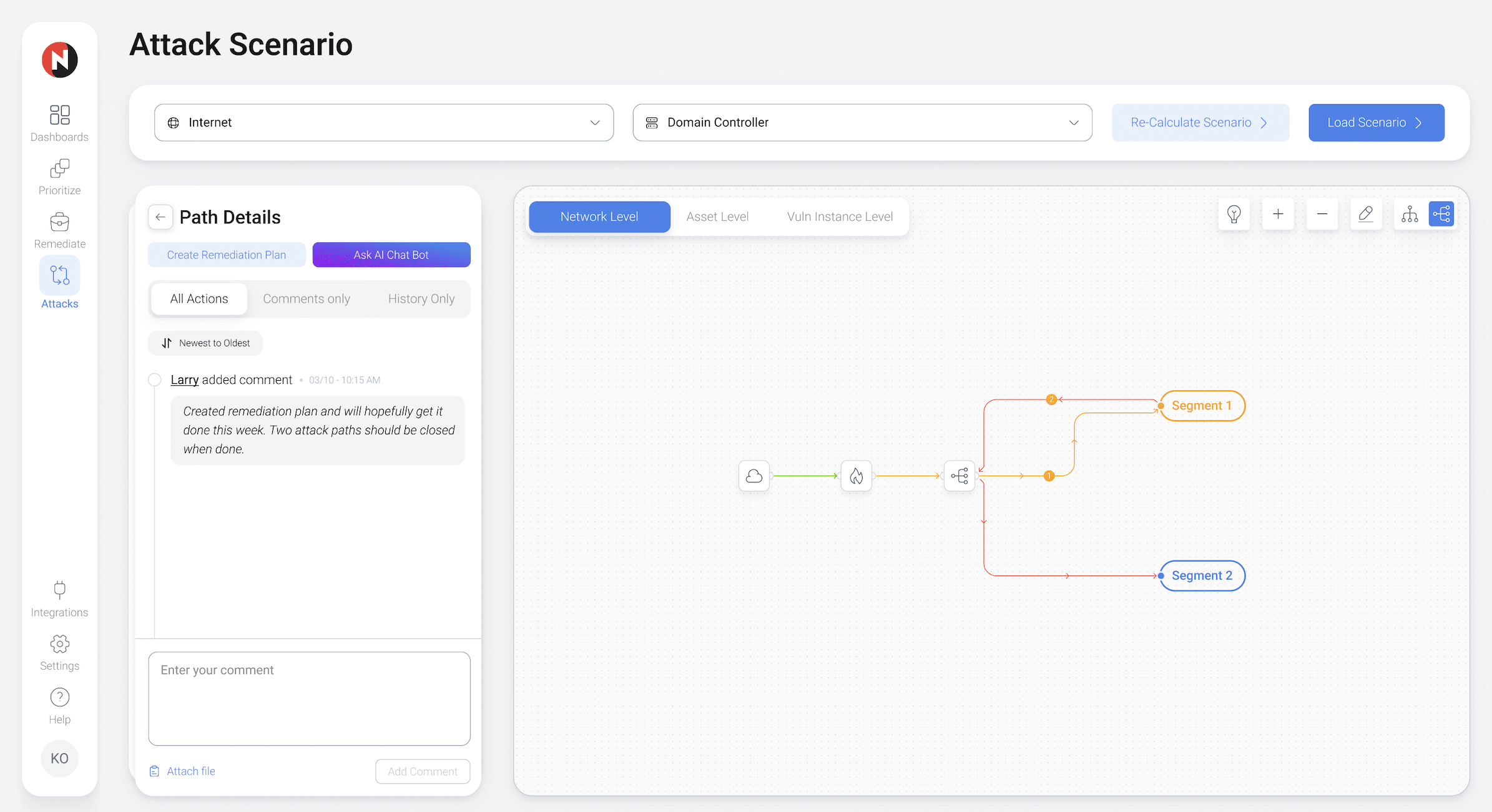
Map Your Attack Paths like an Attacker Would
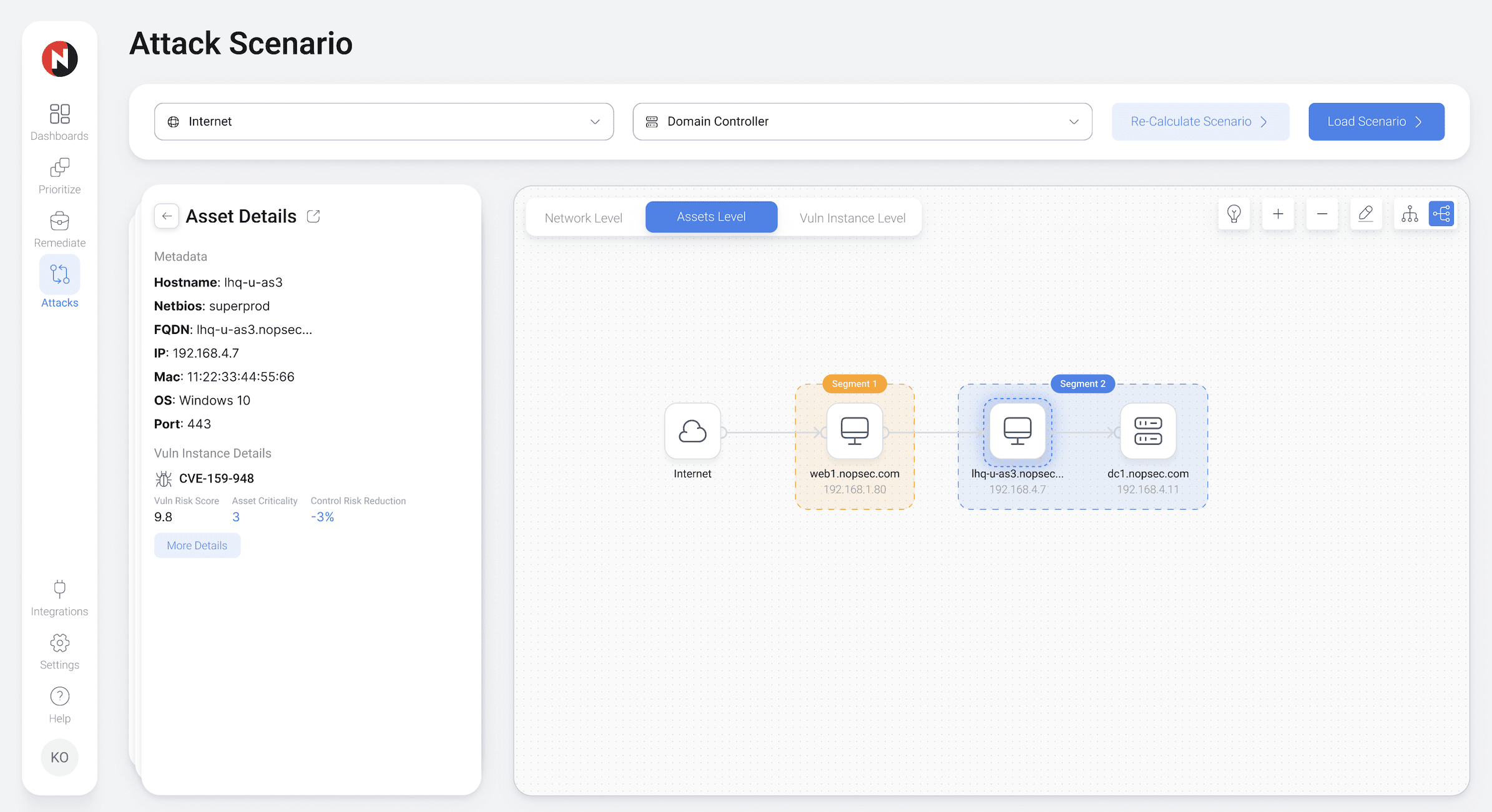
To stop threat actors, your Vulnerability Management team needs to operate with an attacker's perspective. NopSec provides your team with the means to visually map your network's attack paths to gauge the effectiveness of the controls and remediations they are prioritizing.
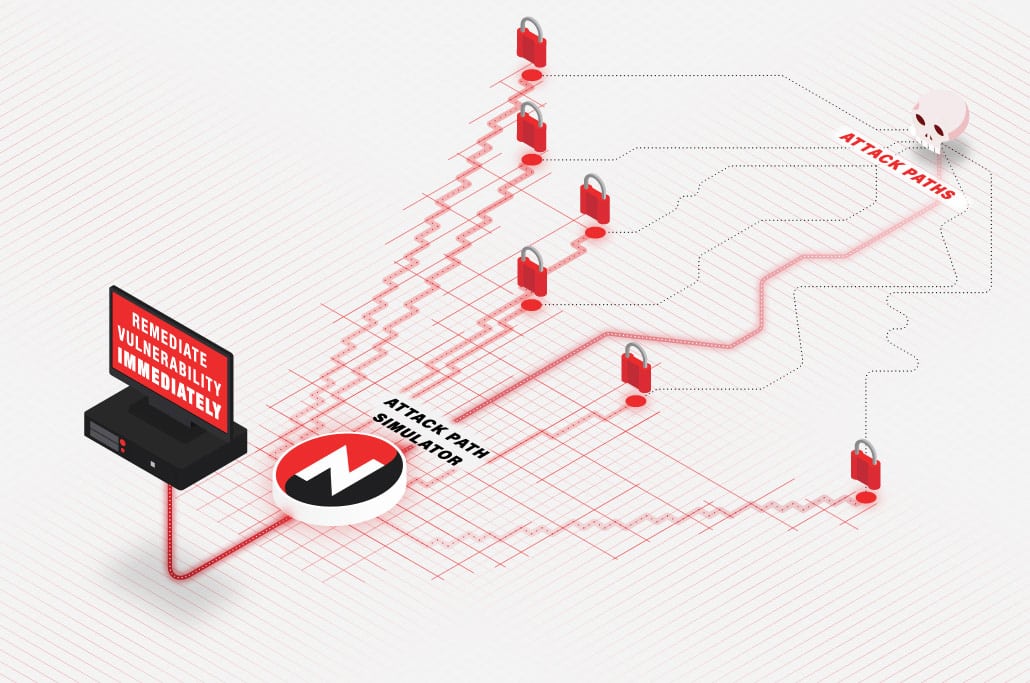
Contextual Visualization of Your Network with NopSec
The conventional approach to risk prioritization requires hours of parsing vulnerability lists to make decisions. This method lacks vital asset context and fails to factor in your environment's unique configuration.
NopSec's attack path graphing technology completes your team's prioritization narrative. Visually map your attack paths and display details on vulnerabilities, asset criticality values, and other mitigating controls. Leverage this information to gain a contextually-based risk score for your attack paths. Maximize your team's impact on reducing risk by validating the effectiveness of their decisions.
Complete Asset Data
Requiring only a few clicks, all relevant asset data is populated into the attack graph database and easily accessible. This includes asset tags, asset values, asset group tagging, subnetting, and switches.
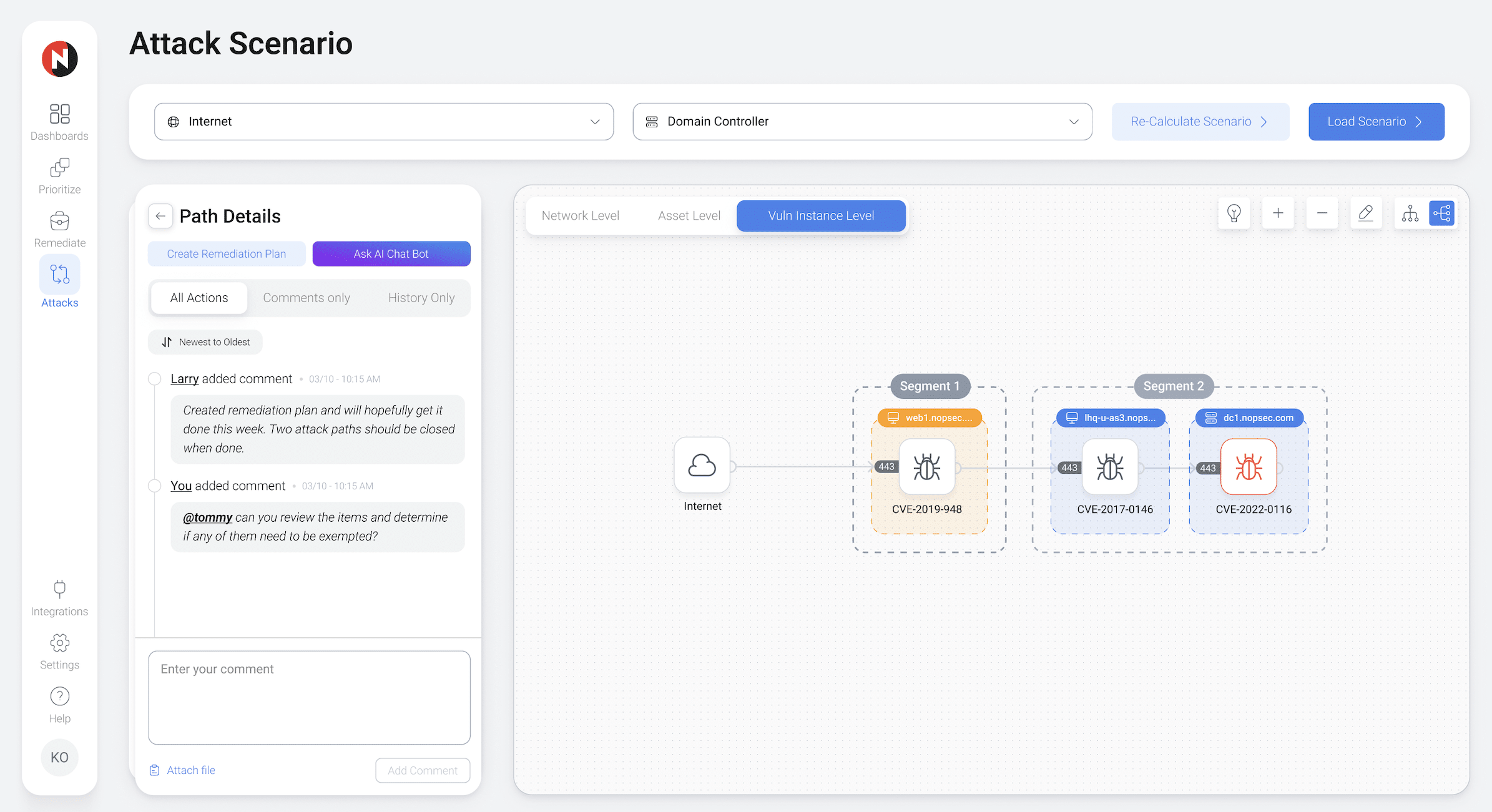
Shortest Attack Path Prioritization
Exploitable attack paths are scored and prioritized via a contextually-based shortest-attack-path algorithm. This risk score can be lowered by applicable mitigating or compensating controls present on the asset, asset group, subnet, or network.
Schedule a Product Demo Today!
See how NopSec's security insights and cyber threat exposure management platform can organize your security chaos.