The Shadow Brokers-Leaked Equation Group’s Hacking Tools: A Lab-Demo Analysis
- Apr 26, 2017
- Michelangelo Sidagni
According to the The Register’s article, last week we started assisting to the widespread exploitation of The Shadow Brokers’ leaked Windows exploits, compromising thousands of vulnerable hosts over the Internet.
This widespread exploitation prompted me to release this blog post that I have been mulling for a while.
As part of the Equation Group’s hacking tools stash, leaked last week by The Shadow Brokers group, this is the latest installment of several leaks featuring network devices vulnerabilities and exploits, Linux and Unix vulnerabilities, and exploits. This hacking tools leak belonging to the Equation Group includes particularly interesting Windows 0-day exploits, implant tools and backdoors used in the widespread exploitation (DoublePulsar), and other 1-day exploits.
This is my analysis and commentary of The Shadow Brokers’ latest leak.
First of all, for the people interested in playing with the tools, these are the two relevant repositories, on GitHub:
These are repositories created with the original tools downloaded from https://yadi.sk/d/NJqzpqo_3GxZA4(Originally posted from #ShadowBrokers)
If you look at the first GitHub repository, it is divided into three directories:
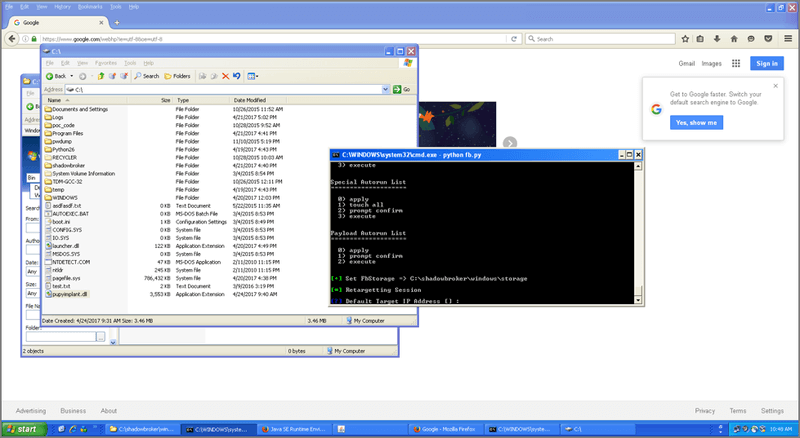
First, I found it very interesting playing with fuzzbunch, which is the Equation Group’s exploitation framework, very similar to the Metasploit framework, but written in python instead of ruby.
I tried to set it up on my lab to play with. I first tried to deploy and execute it on a Kali box, but I realized right away that this was coded to be executed on a Windows 32 bit host. So I decided to launch it in an old Windows XP box, installed Python 2.6 on it and installed the required dependencies (pypiWin32), and then execute it with: python fb.py
After a number of system-related checks, the prompt asks for the default attack box IP and the related callback listener IP.
(Note: IP addresses and other potentially sensitive information in this image and our images in this post have been obfuscated)
Once the checks complete successfully, the terminal ends up on a prompt fb>.
The use of such a terminal is pretty much similar to the use of the Metasploit framework, including the command “use” plus the exploits or implant you would like to configure.
In the “windows” directory there is also an exploits directory that includes some of the most interesting exploits.
The following GitHub repository – https://github.com/misterch0c/shadowbroker – in its README file, describes in detail all the exploits included in the stash. The following is the list of the leaked exploits:
This list includes Windows SMB exploits including the previously undisclosed SMB 0-day labelled “ETERNALBLUE”, which was addressed by Microsoft with the March 2017 patch labelled “MS17-010”.
The combination of ETERNALBLUE exploit and the implant DoublePulsar are currently being used in the wild to compromise Windows host open on the Internet. As always, close your SMB 445 TCP port at the firewall.
The CNC and implant framework “ODDJOB” is also included in the leak under its own directory.
Other resources are worth the mention in terms of the released exploit analysis:
The following is my report on using the ETERNALBLUE MS17-010 SMB exploit on WinXP with a Windows 7 target.
After selecting the exploit to be used with “use Eternalblue”, selecting the target – Win7 / Win2k3 – and selecting the fuzzbunch native stager to be installed, the buffer corruption is triggered and then the implant stager is successfully installed.
After the prompt returns, we invoke the implant installation with “use DoublePulsar” command. DoublePulsar simply allows to ping the installed stager, execute shellcode or upload and execute a custom dll. You can also uninstall the installed implant. In this screenshot, we simply ping the backdoor. You can also install and execute custom DLL implants such as with pupy or Powershell Empire.
DoublePulsar also uses a novel approach to load and execute custom DLL – not reflectively like in many other tools, including Metasploit. Here are some of the blog posts that analyze those techniques:
Another implant and Listening Post present in the hacking tools leak is called “Dander Spiritz”. Using ETERNALBLUE and DoublePulsar you can upload and execute an implant created with “DanderSpiritz”. Dander Spiritz also has a listening post you can launch with “python start_lp.py” in the windows directory. This invokes a “Start.jar” file and requires Java to be installed. Once the implant is executed, it connects back to the Listening Post and it can execute other commands on the implanted OS.
This is the full blog post reporting the use and installation of Dander Spiritz implant and listening post – https://hackernoon.com/a-quick-look-at-the-nsa-exploits-dander-spiritz-trojan-1b5428b0ee65
It was also interesting seeing how using the ETERNALBLUE exploit and DoublePulsar implant, you can install a meterpreter implant created with msf venom.
The community started releasing IDS rules to detect the exploitation attacks described here: YARA IDS rules
Metasploit and other tools have been released to detect systems that have been exploited and implanted with DoublePulsar implants.
The other parts of the leak dump are for a directory named “swift” of references and SQL commands to exploit the SWIFT network. The folder holds SWIFT data that contains SQL scripts that search for SWIFT-specific data inside databases, and text and Excel files hinting the Equation Group had hacked and gained access to several banks across the world, including not only Middle Eastern countries such as Palestine, UAE, Kuwait, Qatar, and Yemen, but also allegedly European Union-based banks.
This folder is by far the most interesting of the three, as it alludes that the Equation Group (NSA) had been infiltrating banks, and secretly keeping an eye on SWIFT transactions. The files included in the dump indicate the Equation Group had targeted and successfully infiltrated the SWIFT Service Bureau of the Middle East (EastNets), one of the several SWIFT departments managing and monitoring SWIFT transactions across Middle Eastern banks.”
The other directory of the dump is “oddjob,” named after a listening post and implant that can be configured via a browser using an “hta” file and targets Windows operating systems.
ODDJOB appears to be both a specially crafted Command and Control (C&C) system as well as an implant for the Microsoft Windows operating system. The implant can remotely collect information from targeted systems by instructing systems to “beacon” out to “Listening Posts” (C&C servers).
ODDJOB disguises its implants and its network traffic as legitimate Windows updates. It transfers data outbound by making requests to what looks like legitimate Windows Update “cab” files. This way of communication (transport) makes the implant particularly stealthy because it communicates via cab file transfers and a protocol used by Microsoft for its Windows update service.
Security researchers are currently working on identifying ways to detect ODDJOB implants via network detection and endpoint security solutions.
In terms of recommendations, It is important to note the following:
As such, organizations running older Windows Operating Systems or those that have not applied the latest patches to their newer Windows Operating Systems may still be at risk from these vulnerabilities.
We would therefore recommend that organizations take the following immediate actions:
We would also recommend the following, mid to long term actions:
(Note: Post Peer-Reviewed by Shawn Evans, Ethical Hacker and Head of Security Engineering, NopSec)