Security Team Intelligence
Buyer’s Guide for Evaluating Cyber Threat Exposure Management (CTEM) Tools
The Problem with Vulnerability Assessment Scanners If you’re reading this post, chances are you’re looking to take the next step…
All Security Team Intelligence articles
-
CTEM: The First Proactive Security Innovation in 20 Years
Summer 2021 It was in the summer of 2021, in the middle of COVID. Isolation and testing remained in effect,…
-
Three Major Signs You Need a Cyber Threat Exposure Management Tool
Cyber threat exposure management (CTEM) tools are a new technology replacing traditional vulnerability prioritization tools (VPT). They were created to…
-
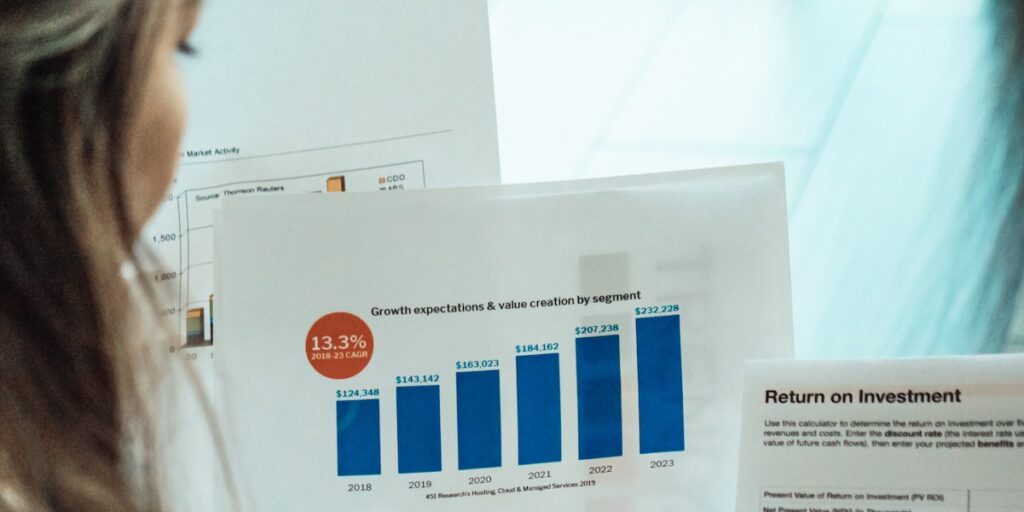
How to ROI a Cyber Threat Exposure Management Tool with Excel Instructions
When evaluating any software solution for purchase, ROI is one of the most crucial parts of that evaluation. Without communicating…
-
Cryptocurrency Security Threat Modeling: Beyond Vulnerabilities
Another day goes by, another latest and greatest security breach affects the cryptocurrency world. The attacks range from phishing campaigns…
-
How Much Does a Vulnerability Prioritization Tool (VPT) Cost
So, you’re looking to take your vulnerability management game to the next level with a vulnerability prioritization tool (VPT). Well,…
-
What’s the Difference Between Vulnerability Assessment Scanners and Vulnerability Prioritization Tools
Under the umbrella of risked-based vulnerability management (RBVM) live a host of tools who’s applications correspond to various stages of…
-
Fix Less, Secure More: Why You Should Put Vulnerability Prioritization First
NopSec has been in the risk-based vulnerability management (RBVM) game for 10 years now. Over the course of this decade…
-
How to Identify Cybersecurity Attack Paths from the Attacker’s Perspective
When it comes to cybersecurity, there are two points of view to always consider – the external and the internal….
-
What is a Vulnerability Prioritization Tool and How Do They Work?
If you’re new to cybersecurity technology or looking to mature your program you’ll quickly come across vulnerability prioritization tools in…
-
Buyer’s Guide for Evaluating Cyber Threat Exposure Management (CTEM) Tools
The Problem with Vulnerability Assessment Scanners If you’re reading this post, chances are you’re looking to take the next step…
-
How to Create Vulnerability Management Reports for Executives
Vulnerability Management programs produce a lot of data about the vulnerabilities and remediation efforts. Due to this, it is very…
-
The Benefits of Full Stack Vulnerability Management
What is Full Stack Vulnerability Management? Full stack vulnerability management utilizes a variety of vulnerability scanner types to identify and…
-
Vulnerability Scanning Best Practices
Vulnerability management’s cornerstone is largely going to revolve around setting up and managing your infrastructure scanner in order to find,…
-
Five Questions to Ask Before Choosing an RBVM Platform
Choosing a risk-based vulnerability management (RBVM) solution can be daunting. Where do you begin? What features are available, and what…
-
Vulnerability Management in Election Security
Vulnerability management is an ongoing, iterative process. Companies with large cybersecurity teams can still struggle with proving the efficacy of…
-
CISA Binding Operational Directive 23-01: A Mandate for Attack Surface and Vulnerability Management in Federal Networks
CISA has recently issued a Binding Operational Directive (BOD) 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks, which…
-
“Future of Vulnerability Management” Podcast Episode 10: How to Reinvigorate the Vulnerability Management Category
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
CVSS vs EPSS: Why Emerging EPSS Outperforms Old CVSS Models
Accurately assessing the risk of software vulnerabilities is critical in order to prioritize remediation efforts given limited remediation resources. For…
-
“Future of Vulnerability Management” Podcast Episode 9: Why it’s Important for Security Practitioners to Understand Business Logic to Prioritize Vulnerabilities
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Mapping CVEs and ATT&CK Framework TTPs: An Empirical Approach
Categorizing and classifying vulnerabilities and attacks is important to understand how a vulnerability is exploited and how a breach unfolds…
-
“Future of Vulnerability Management” Podcast Episode 8: How Organizational Culture Affects Consensus about the Criticality of Assets
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Using Machine Learning in Vulnerability Management for Prioritization
Securing computer systems is the ultimate big data problem. Billions of computers generate roughly 2.5 quintillion bytes of data everyday. …
-
“Future of Vulnerability Management” Podcast Episode 7: How Practitioners Can Use Vulnerability Management to Improve Business Objectives
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Keeping Vulnerability Scanner Data in Sync for Vulnerability Remediation
All Risk-Based Vulnerability Management (RBVM) platforms include integrations to multiple vulnerability assessment products. In addition to vulnerability findings and asset…
-
“Future of Vulnerability Management” Podcast Episode 6: The Role Vulnerability Management Plays in Proper Cyber Hygiene
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Vulnerability Management Prioritization: Defense Wins Championships
Vulnerability Management is one of the less flashy or exciting parts of your cybersecurity department maintenance routine – but is…
-
“Future of Vulnerability Management” Podcast Episode 5: How to Bridge the Gap Between Risk Management and Core Business Outcomes
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Security Priorities 2022: Insights from the State of Vulnerability Management Report
In its most basic form, security is about protecting people and systems from harm. Increasingly, our security depends on our…
-
“Future of Vulnerability Management” Podcast Episode 4: How a 105 year old Ad Agency Tackles Vulnerability Management With Clients
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
Four Interesting Facts from the State of Vulnerability Management Report
The State of Vulnerability Management report, recently released by NopSec, shows that while organizations are making strides in vulnerability management,…
-
“Future of Vulnerability Management” Podcast Episode 3: The Power of Soft Skills in Vulnerability Management
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
“Future of Vulnerability Management” Podcast Episode 2: Weaknesses in the Vulnerability Management Field
The Future of Vulnerability Management podcast is dedicated to helping security professionals tackle real issues in the vulnerability management space. Lisa…
-
CIS 18 Critical Security Controls Version 8
The CIS Security Controls, published by SANS and the Center for Internet Security (SIS) and formerly known as the SANS…
-
Introducing: the “Future of Vulnerability Management” Podcast
Today, we are excited to announce our new podcast — the Future of Vulnerability Management which is dedicated to helping…
-
State of Vulnerability Management: 6 Key Takeaways
Have you ever wondered what security professionals want most from their Vulnerability Management (VM) program? We have. In fact, we…
-
Creating a Vulnerability Management Program – Discovering Your Vulnerabilities: The First Foray
We talked previously about the need to use people, processes, and technology wisely to support your vulnerability risk management. Each element…
-
China is Exploiting Vulnerabilities in Widely Used Home-Office Devices, U.S. Agencies Warn
A new advisory from top federal security and law enforcement agencies warns that state-sponsored cyber actors from the People’s Republic…
-
Risk-Based Vulnerability Management: Efficient + Effective
We described in the previous blog post the difference between vulnerability management and risk management. A quick reminder: vulnerabilities are…
-
Vulnerability Management vs. Risk Management: Defining the Fundamentals
Businesses run fast to keep pace in a market that is ever dynamic, with new entries threatening to oust established…
-
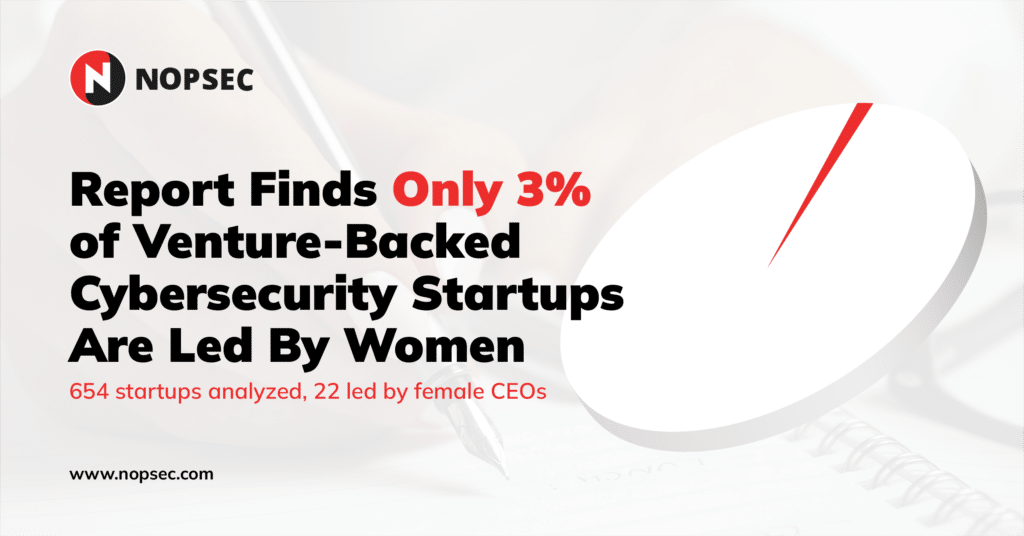
How Many Venture-Backed Cybersecurity Startups Are Led By Women?
Cybersecurity startups have had an incredible past couple of years. In 2020, they raised $8.9 billion and last year, that…
-
Creating a Vulnerability Management Program – The People, Process, and Technology
Continuing our How to Build a VM Program series, this third installment breaks the working components of a program into…
-
Creating a Vulnerability Management Program – What is Vulnerability Management and the VM Lifecycle Stages?
As we said in the introduction to this series, cybercriminals are becoming increasingly sophisticated in their assaults, and the methods…
-
Creating a Vulnerability Management Program – Why You Need a Vulnerability Management Program Starting Now
In the past, cybercriminals relied heavily on phishing to slip into an organization’s IT system to achieve their objectives. Recently,…
-
Implementing and Maintaining Security Program Metrics
Cybersecurity metrics are a pertinent part of measuring the successes and failures of your program and the effectiveness of your…
-
The ROI of ThreatForce
Demonstrating the ROI of security investments has long been a challenge for SecOps teams. If an organization as a whole…
-
Trending CVEs for the Week of October 21st, 2019
Still CVE-2019-14287 – Linux Sodo Vulnerability Linux Sodo Vulnerability, tracked as CVE-2019-14287, has been a nightmare for IT & cyber-security…
-
Trending CVEs for the Week of October 14th, 2019
CVE-2019-14287 – Linux Sodo Vulnerability Description A flaw was found in the way sudo implemented running commands with arbitrary user…
-
Trending CVEs for the Week of October 7th, 2019
CVE-2019-1367 – MICROSOFT ZERO-DAY VULNERABILITY – OUT-OF-BAND PATCH, Again Microsoft zero-day vulnerability is still trending on social media and we…
-
Trending CVEs for the Week of September 30th, 2019
CVE-2019-16759 – vBulletin Remote Code Execution Description vBulletin 5.x through 5.5.4 allows remote command execution via the widgetConfig[code] parameter in…
-
Trending CVEs for the Week of September 23rd, 2019
CVE-2019-1367 – Microsoft Zero-Day Vulnerability – Out-of-band Patch Description A remote code execution vulnerability exists in the way that the…
-
Trending CVEs for the Week of September 16th, 2019
CVE-2019-0708 – BLUEKEEP Exploit Has Been Released The BlueKeep vulnerability, tracked as CVE-2019-0708, has been a nightmare for IT &…
-
Trending CVEs for the Week of September 2nd, 2019
Still CVE-2019-11510 – Pulse Secure VPN CVE-2019-11510 has been a nightmare for IT & cyber-security teams for the past 2…
-
Trending CVEs for the Week of August 26th, 2019
CVE-2019-11510 – Pulse Secure VPN Description In Pulse Secure Pulse Connect Secure (PCS) before 8.1R15.1, 8.2 before 8.2R12.1, 8.3 before…
-
Trending CVEs for the Week of August 19th, 2019
CVE-2019-1181 – Wormable Windows Remote Desktop Flaw Description A remote code execution vulnerability exists in Remote Desktop Services – formerly…
-
Trending CVEs for the Week of August 12th, 2019
CVE-2019-1125 – SWAPGS Vulnerability Description An information disclosure vulnerability exists when certain central processing units (CPU) speculatively access memory. An…
-
Value of Using Trending Metrics in Vulnerability Management
My work as Senior Product Designer here at NopSec has given me a unique view of the industry landscape, as…
-
Trending CVEs for the Week of August 5th, 2019
CVE-2019-13272 – Linux Kernel Privilege Escalation Vulnerability Alert Description In the Linux kernel before 5.1.17, ptrace_link in kernel/ptrace.c mishandles the…
-
Trending CVEs for the Week of July 29th, 2019
CVE-2019-2107 – Android devices could be hacked by playing a video Description This vulnerability could lead to remote code execution…
-
Trending CVEs for the Week of July 22nd, 2019
CVE-2019-6342 – Drupal Core Access Bypass Vulnerability Description According to its self-reported version, in Drupal 8.7.4, when the experimental Workspaces…
-
Trending CVEs for the Week of July 15th, 2019
CVE-2019-1132 – Win32k Elevation of Privilege Vulnerability Description An elevation of privilege vulnerability exists in Windows when the Win32k component…
-
Trending CVEs for the Week of July 8th, 2019
CVE-2017-11774 – Microsoft Outlook Security Feature Bypass Vulnerability Description A security feature bypass vulnerability exists when Microsoft Outlook improperly handles…
-
Trending CVEs for the Week of July 1st, 2019
Again, CVE-2019-0708 – BlueKeep – Wormable RDP Vulnerability The BlueKeep vulnerability, tracked as CVE-2019-0708, has been a nightmare for IT…
-
Trending CVEs for the Week of June 17th, 2019
CVE-2019-11477 – SACK Panic Remote Command Execution Flaw in Exim is still trending on social media and we extensively covered…
-
Trending CVEs for the Week of June 10th, 2019
CVE-2019-10149 – Remote Command Execution Flaw in Exim The BlueKeep vulnerability is still the number one trending vulnerability on social…
-
Trending CVEs for the Week of June 3rd, 2019
CVE-2018-15664 – Docker Vulnerability The BlueKeep vulnerability is still trending on social media and we extensively covered CVE-2019-0708 in May…
-
Clues to identifying IT vulnerability owners
IT Vulnerability Ownership, Part 2: Find early adopters Telling people what to do gets nowhere fast. I even have to…
-
Trending CVEs for the Week of May 27th, 2019
Still CVE-2019-0708 – BlueKeep – Wormable RDP Vulnerability The BlueKeep vulnerability, tracked as CVE-2019-0708, has been a nightmare for IT…
-
Trending CVEs for the Week of May 20th, 2019
CVE-2019-0708 – BlueKeep – Wormable RDP Vulnerability NopSec advises you to apply patches immediately. Description CVE-2019-0708 is a critical remote…
-
Trending CVEs for the Week of May 13th, 2019
CVE-2019-0604 – Microsoft SharePoint Remote Code Execution Vulnerability Description A remote code execution vulnerability exists in Microsoft SharePoint when the…
-
Trending CVEs for the Week of May 6th, 2019
CVE-2019-3396 – Widget Connector Macro in Atlassian Confluence Server Last week, we covered CVE-2019-2725 which was a vulnerability in the…
-
Trending CVEs for the Week of April 29th, 2019
CVE-2019-2725 – Oracle WebLogic Server Zero-Day Vulnerability Description CVE-2019-2725 is a vulnerability in the Oracle WebLogic Server component of Oracle…
-
Trending CVEs for the Week of April 22nd, 2019
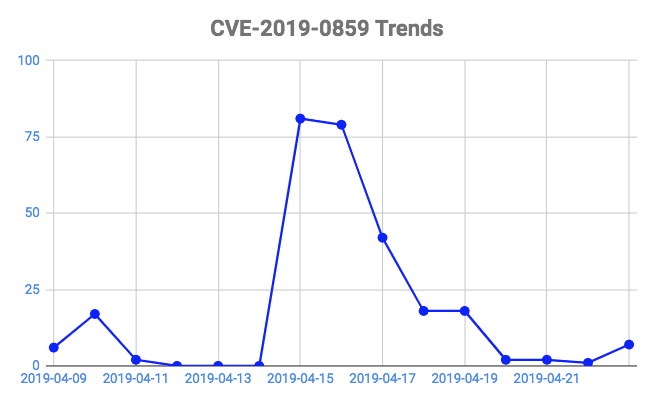
CVE-2019-0859 – Yet Another Windows Zero-Day Vulnerability Last week, we covered an elevation of privilege vulnerability in Win32k component of…
-
Trending CVEs for the Week of April 15th, 2019
CVE-2019-0859 – Yet Another Windows Zero-Day Vulnerability Description This week’s trending vulnerability may sound eerily familiar. CVE-2019-0859 is an elevation…
-
IT Vulnerability Owners: How to Identify Vulnerability Owners (Yes Its’ Hard)
IT Vulnerability Ownership, Part 1: Problem, benefits to solving it, and understand its roots Running a successful vulnerability management program…
-
Trending CVEs for the Week of April 8th, 2019
CVE-2019-0211 – Carpe Diem – Apache Local Privilege Escalation Vulnerability Description This week’s trending vulnerability is CVE-2019-0211, a local privilege…
-
Trending CVEs for the Week of April 1st, 2019
CVE-2019-1002101 – Kubernetes Directory Traversal Description Back in February, we talked about a malicious container ‘break out’ vulnerability in runc…
-
Trending CVEs for the Week of March 25th, 2019
CVE-2019-5418 – Ruby on Rails File Content Disclosure Vulnerability Description This week’s trending vulnerability, CVE-2019-5418, is a file content disclosure…
-
Trending CVEs for the Week of March 18th, 2019
CVE-2019-0797 – Windows Zero-Day Vulnerability Description CVE-2019-0797 is one of the three zero-day vulnerabilities (one in Chrome, the other two…
-
Instant Risk Reduction Recommendations to Align Priorities with IT
Snow flurries were a welcome change in New Jersey from last month’s high gust winds. I often multitask my dog…
-
Trending CVEs for the Week of March 11th, 2019
Google Chrome Zero-Day Vulnerability (CVE-2019-5786) & Two New Actively Exploited Windows Zero-Day Vulnerabilities Description On February 27th, security engineers from…
-
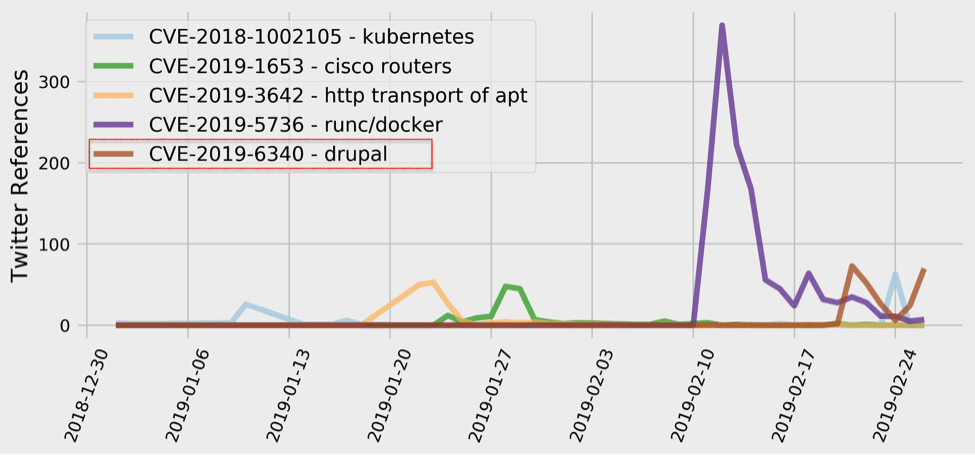
Trending CVEs for the Week of March 4th, 2019
Updates on Drupal (CVE-2019-6340) & A New Improper Input Validation Flaw Leading to RCE in Cisco Routers (CVE-2019-1663) The improper…
-
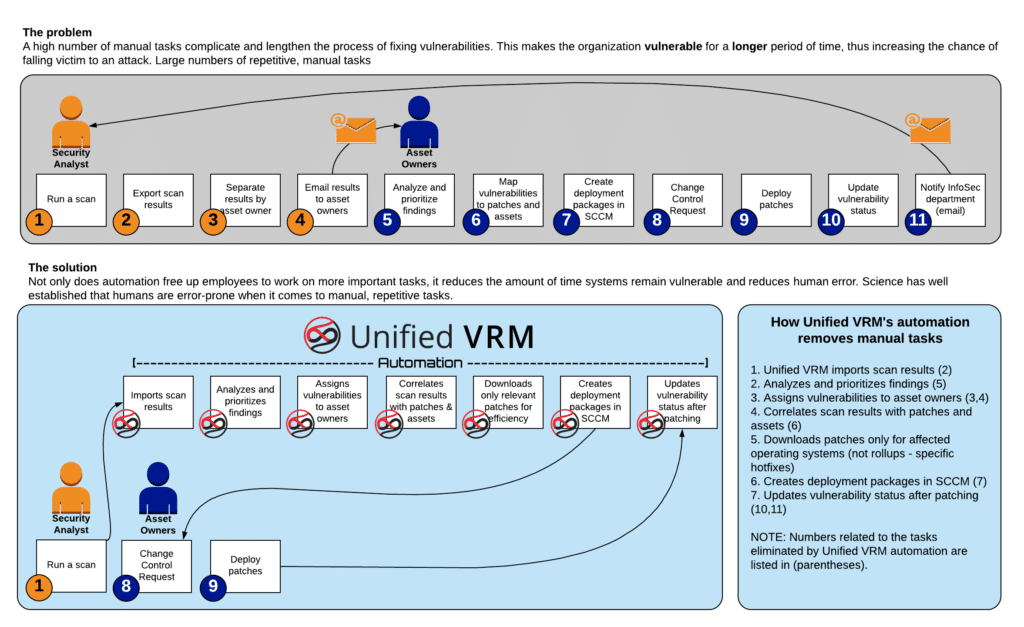
Time is Money Part 6: Calculating ROI of Vulnerability Management Program
This is the final post in this six-part series. You can find the previous posts below. Time is Money, Part…
-
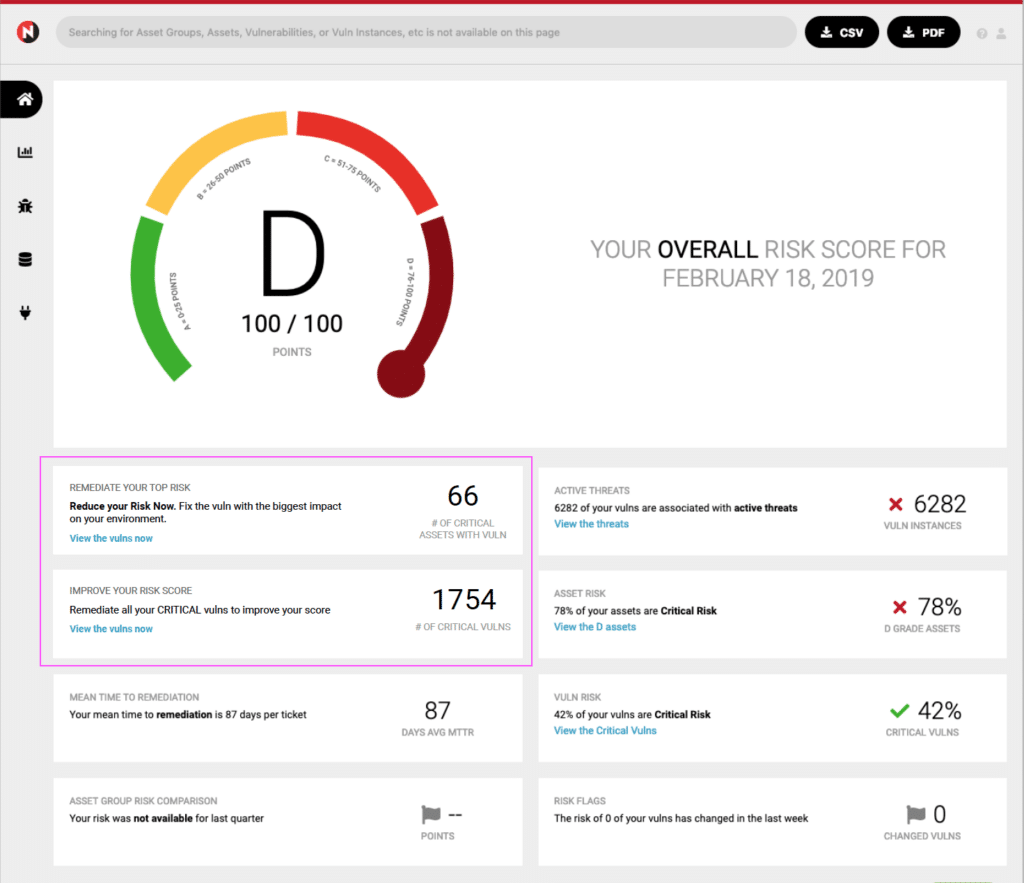
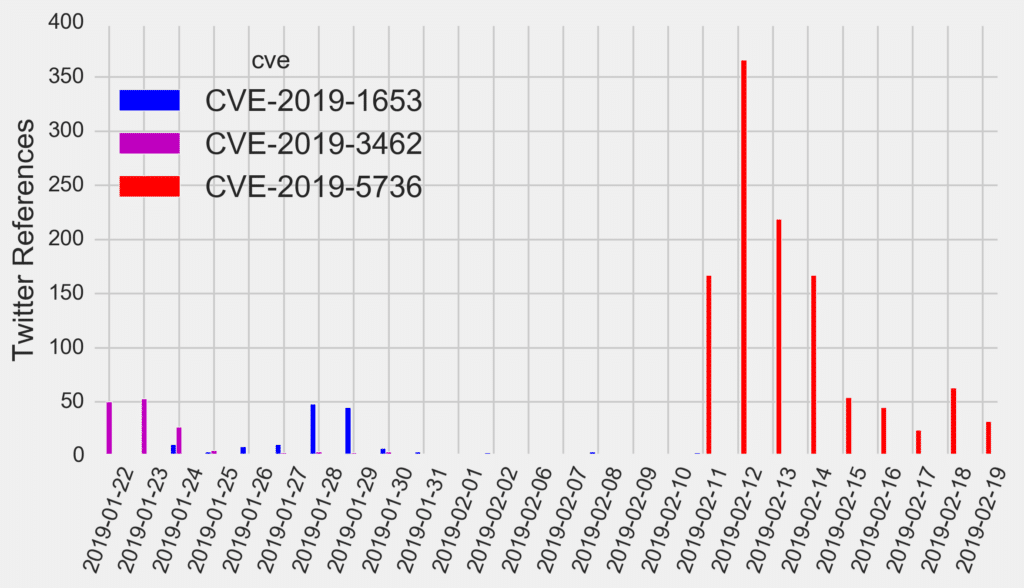
Trending CVEs for the Week of February 25th, 2019
CVE-2019-6340 – Improper Input Validation Leading to Remote Code Execution in Drupal This week’s most tweeted-about vulnerability is a, yet…
-
Trending CVEs for the Week of February 18th, 2019
CVE-2019-5736 – Malicious Container “Break Out” Vulnerability in Runc Last week, we extensively covered a security flaw in runc –…
-
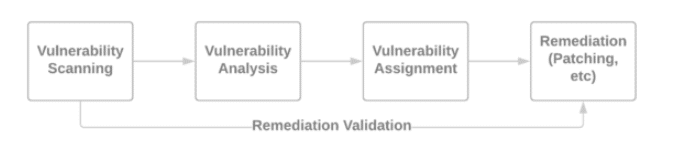
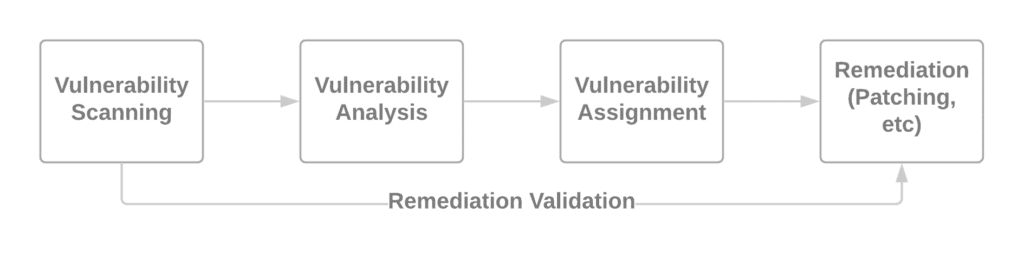
Time is Money, Part 5: Validating the Fix
This is part five in a six-part series. You can find the previous posts below. Time is Money, Part 1:…
-
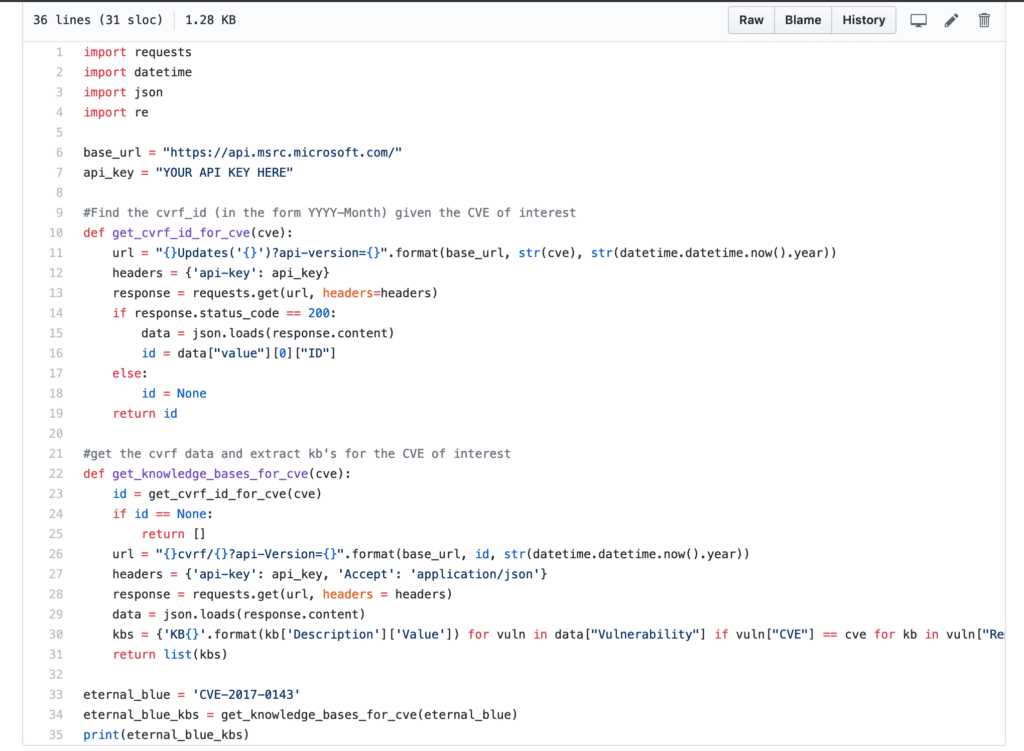
CVE to KB: How to Correlate CVE Vulnerabilities to KB Patches via Automation
Here at NopSec our goal is to provide the most intelligent, automated way of managing cybersecurity risk in enterprise environments….
-
Trending CVEs for the Week of February 11th, 2019
CVE-2019-5736 – malicious container “break out” vulnerability in runc If you follow cybersecurity news at all, you have likely already…
-
Trending CVEs for the Week of February 4th, 2019
CVE-2019-1653 (Cisco Routers information disclosure), CVE-2018-16858 (LibreOffice directory traversal bug) It has been a relatively slow week as we have…
-
Time is Money Part 4: Fix Security Vulnerabilities
This is part four in a six-part series. You can find the previous posts below. Time is Money, Part 1:…
-
Time is Money, Part 3: Vulnerability Assignment
This is part three in a six-part series. You can find the previous posts below. Time is Money, Part 1:…
-
Trending CVEs for the Week of January 28th, 2019
This week’s most talked about vulnerability is CVE-2019-1653. It is an information disclosure vulnerability affecting web-based management interface of Cisco…
-
Trending CVEs for the Week of January 21st, 2019
CVE-2018-15982 is a use after free zero-day vulnerability in Adobe Flash Player (versions up to 31.0.0.153) which can result in…
-
Time is Money, Part 2: Vulnerability Analysis
This is part two in a six-part series. You can find the first in this series here, which lists the…
-
Time is Money, Part 1: Vulnerability Management Maturity Levels
Time is Money is a six-part series we’re going to post throughout the first few months of 2019. We’ll also…
-
Fundamental Steps Organizations Can Take to Minimize Breach Risk
We’re living through the gold rush of information security. The awareness and importance of information (or cyber) security has never…
-
Are You Ready for PCI DSS 3.2?
The updated PCI 3.2 requirements are coming to a head with a deadline this February 1st, 2018. While we’re sure…
-
NYDFS Cybersecurity Regulations: Key Deadlines
The first traditional deadline is coming to a close this month for compliance with the NYDFS Cybersecurity Regulations. Please note that…
-
DevOps Risk Management: Vulnerability Risk Management as DevOps Practice
Silos exist in all levels and all types of organizations. Different teams naturally have different priorities, methodologies, and more, though…
-
How Hackers Exploit Weak Password Vulnerabilities
The “password” is one of those seemingly foolproof ways to protect your online valuables. Like a secret word between you…
-
Password Cracking: Top Tools Hackers Use to Crack Passwords
What’s the quickest way to a hacker’s heart? Make sure your business email password is “Password123.” Or perhaps “Summer2017” if…
-
Key Milestone Dates: NYDFS Cybersecurity Regulations
If you’re in the financial industry (or working as a provider with such organizations), you most likely have already heard…
-
5 Benefits of Retaining a Virtual CISO
Cybersecurity is finally gaining the attention it’s due. From whistleblowers to major data breaches, issues once kept strictly in the…
-
RBAC Implementation: Role Based Access Control Implementation
Organizations seeking to improve their security posture and meet regulatory or audit compliance requirements must consider implementing role based access control (RBAC).
-
Implementing New York DFS Cybersecurity Regulations: Where Are You in the Process?
Here at NopSec, we’ve spoken with a number of financial organizations about where they are in the process of meeting…
-
Application Security Management: Managing Vulnerabilities Throughout Secure SDLC
How can I find security people, how do I deal with budget and time, how should I prioritize, what will…
-
Phishing: What Everyone in Your Organization Needs to Know
Do you feel confident that everyone in your organization could identify a phishing email that contained ransomware? What if the…
-
NYDFS Cybersecurity Regulations: Will You Be Ready?
When new cybersecurity regulations from the New York Department of Financial Services (NYDFS) take effect on March 1, 2017, financial institutions will…
-
3 Ways to Go Beyond HIPAA Compliance
Compliance isn’t enough for healthcare organizations. For years, we have equated compliance with effective vulnerability risk management. This is simply…
-
SMBs: Most Likely To Be Hacked?
Most small and medium business owners believe that cyber criminals only target large businesses and corporations. They couldn’t be more…
-
Improving Business Outcomes With VRM
Time and again, we hear from information security leaders who have invested in vulnerability risk management (VRM) technology and are…
-
Pen Testing Costs: The Business Value of Pen Testing Services
On March 23rd 2016, I had the pleasure to participate in the Inaugural 2016 National Conference of Minority Cybersecurity Professionals…
-
How to Speak Information Security to Executives: A CSO Perspective
According to recent research over 60 percent of survey participants stated their executives are only “somewhat” or “not at all” informed about…
-
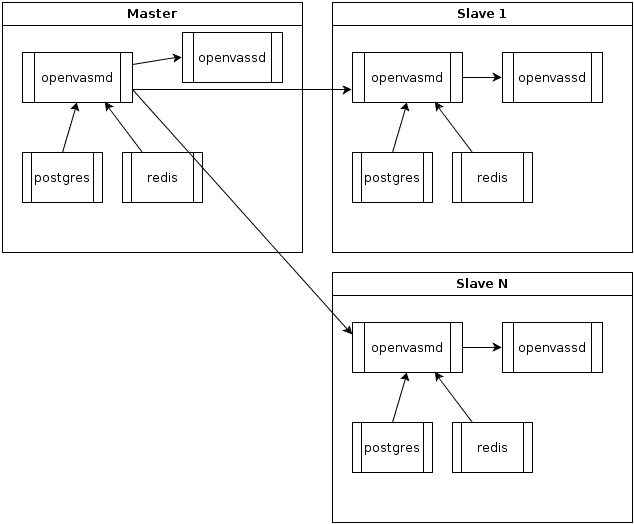
Docker-based OpenVAS Scanning Cluster to Improve Scope Scalability
OpenVAS (Open Vulnerability Assessment Scanner) – is an open source security vulnerability scanner and manager. It is an open source…
-
Vulnerability Management Presentation to CISO – No problem
Most of our customers’ security analysts are called on a monthly basis (or more often) to deliver a presentation of…
-
Mapping Penetration Testing report and vulnerability management CVEs
Penetration tests are point-in-time adversarial tests aimed at testing the intrusion prevention, detection, and incident response capabilities and controls of an…
-
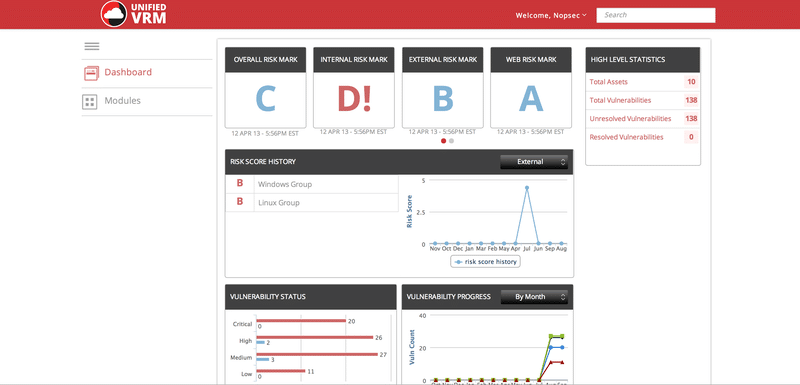
Detecting the GHOST glibc Vulnerability with Unified VRM
In the previous blog post here, we described the GHOST Linux glibc vulnerability in details and its repercussions to the…
-
The First Steps After an Attack
The term “security breach,” and other similar phrases, have become commonplace. This year alone we have seen the data of…
-
The Hidden Costs of an Information Security Breach
No industry is immune to IT security breaches and it seems that retailers have been in the spotlight of late….
-
Avoid this Mistake When Sourcing a Penetration Test
Understanding how to effectively evaluate and select a penetration testing vendor can be a challenging exercise. Frequently the problem comes…
-
4 Things to Consider When Outsourcing Vulnerability Management
Security risks to information systems and sensitive data are expanding at a rate that can outpace an organization’s technical resources…
-
Vulnerability Scanning Best Practices: Where and When to Run Vulnerability Scans
As penetration testers know, spending nights awake to probe networks, servers and applications is common practice. For companies completing vulnerability…
-
Total Cost of Ownership for Vulnerability Management
With any technology investment, budget is a core part of the decision criteria. IT security departments are expected to do…
-
Has Your Company Performed an Annual Penetration Test Yet this Year?
Many federal regulations such as GBLA, HIPAA and PCI require an annual penetration test. Customers often ask for our penetration testing services in…
-
How Much does a Penetration Test Cost?
This is the time of the year that we get a lot of inquiries about performing an annual penetration test….
-
Using Unified VRM to Implement SANS 20 Critical Security Controls
The SANS 20 Critical Security Controls are prioritized mitigation steps to improve cybersecurity. Coordinated through the SANS Institute, many companies with…
-
SANS Critical Control 20: SANS Penetration Testing and Red Team Exercises
As we have reached the end of this blog post series on SANS 20 Critical Controls, this one is definitely…
-
SANS Critical Controls 17, 18 and 19: Data Loss Prevention, Incident Response and Management, Secure Network Engineering
In this installment of our SANS 20 Critical Security Controls, I bundled three controls together simply because they are very…
-
SANS Critical Control 16: Account Monitoring and Control
Have you ever considered what is the venue most attackers use to infiltrate target systems? In terms of percentage, certainly…
-
SANS Critical Controls 14 and 15: Network Audit Logging and Controlled Access
This week we come back with our blog series on SANS 20 Critical Controls and focus on Audit Logs and Controlled…
-
SANS Critical Control 13: Network Boundary Defense
As we are getting ready to descend for a couple of days to Vegas for Black Hat / DefCon /…
-
SANS Critical Control 6: SANS Application Software Security
Another very important area of an organization’s security program is its application security roadmap. We all know that web and…
-
Vulnerability Risk Score: How to Evaluate Vulnerability Severity Scores
There’s a quote attributed to Fabio Massacci, professor of information systems and security at the University of Trento in Italy…
-
SANS Critical Control 12: Controlled Use of Administrative Privileges
In a system there is no privilege that is higher than administrative privileges. In Unix and Linux world, this is…
-
SANS Critical Control 11: Limitation and Control of Network Ports, Protocols, and Services
Exposure level and Risk level are directly proportional to each other! Ports, protocols and services are entry points and mechanisms…
-
SANS Critical Security Controls: Secure Configurations for Network Devices
Why all graphical representations of a network firewall include a wall with flames? Do you have to set a wall…
-
SANS Critical Control 8 and 9: Data Recovery Capability & Security Skill Assessment
On this blog post of the SANS Critical Control series I comment on two critical controls that at the first…
-
SANS Critical Control 7: Wireless Device Control
Wireless networks have always been a “no man’s land” in terms of security and appropriate configuration. Some of the most…
-
SANS Critical Control 4: Continuous Vulnerability Assessment and Remediation
As part of SANS 20 Critical Security Controls mapping with Unified VRM series, today I am going to discuss Critical…
-
SANS Critical Control 5: Malware Defenses
In this latest installment of this blog series, I am going to analyze how to implement the SANS Critical Control…
-
SANS Critical Control 3: Secure Configurations
In the previous two blog posts I have been addressing Control 1 and Control 2 in the SANS Critical Security…
-
SANS Critical Control 2: Inventory of Authorized and Unauthorized Software
Yesterday, I published the first blog post on mapping SANS 20 critical security controls to Unified VRM. The post dealt…
-
How Attackers Choose Which Vulnerabilities To Exploit
I loved the opening paragraph in a recent article titled, “How Attackers Choose Which Vulnerabilities To Exploit” by Michael Cobb,…
-
CVE-2003-0095 – Oracle Database Server Unauthenticated Remote Overflow Metasploit Module
Penetration testing is one of the services that we offer NopSec customers. A vulnerability assessment and penetration test provide an…
-
Mistakes Companies Make When it Comes to Vulnerability Management
We observe a common misconception that companies believe they are doing “vulnerability management” when, more often than not, they are…