Trending CVEs for the Week of February 18th, 2019
- Feb 20, 2019
- Shawn Evans
Last week, we extensively covered a security flaw in runc – a universal command-line interface tool used to support Docker and Linux container engines – CVE-2019-5736. This vulnerability could be exploited by an attacker by either persuading a user to create a new container using an attacker-controlled image or by using the docker exec command to attach into an existing container that the attacker previously had write access to. A successful exploit could allow the attacker to escape the container and execute arbitrary commands with root privileges on the host system.
For details about the vulnerability and references to advisories, please see our original post here https://nopsec.com/trending-cves-for-the-week-of-feb-11-2019/. If curious to know how we patched it in Unified VRM, please refer to https://nopsec.com/how-we-mitigated-cve-2019-5736-for-unified-vrm/.
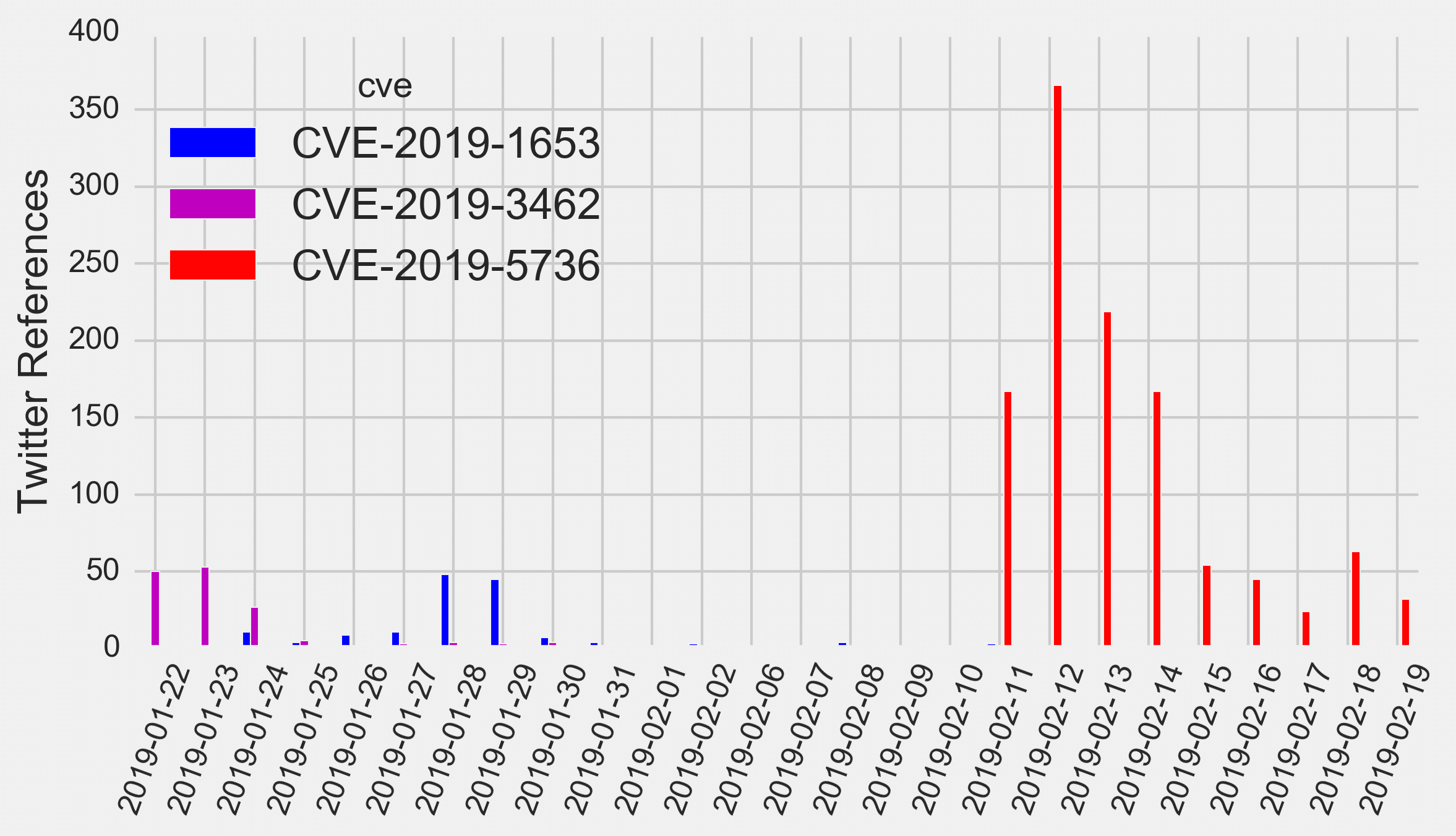
While the references to this vulnerability in social media have been on a decline, it remains the most talked about vulnerability for this week as well. This is not surprising considering the popularity of Docker containers and ubiquity of cloud computing services such as AWS. In fact, this is now the most talked about vulnerability for this year so far – and it’s not even a close race. Figure below shows daily count of Twitter mentions over time for the top three CVEs of 2019 (as of February 19th).
Since our last week’s posts, researches who originally discovered the vulnerability have posted a detailed account of how they did it, an exploit has been published in Github , and the NVD entry has been updated with CVSS scores. Interestingly, while the Attack Vector has been marked as Local for CVSS v3, its CVSS v2 analog Access Vector was labeled Network, resulting in vastly different exploitability score under the two versions of CVSS (1.8 in CVSS v3 and 8.6 in CVSS v2).
Share your thoughts in our community!