Malware Analysis: Moving Beyond the CVSS Score
- May 17, 2016
- Guest Author
Note: This article was updated in June 2022.
Here at NopSec, we are all about risk — our number one goal as a company to help organizations evaluate and reduce their risk. However, the term “risk” can be highly subjective, making it difficult for organizations to determine the riskiest vulnerabilities. One quantitative measure NopSec employs to help an organization evaluate the risk of a vulnerability is through malware correlation. If a vulnerability has malware correlated with it, it represents elevated risk. NopSec keeps an updated database of malware information, but in order to stay one step ahead of attackers, we also want to predict the future.
Today’s blog post will focus on how to evaluate risk, including what is the CVSS (Common Vulnerability Scoring System) and other factors that help predict whether or not a vulnerability has malware associated with it, and how to analyze these malware factors today for better remediation prioritization tomorrow.
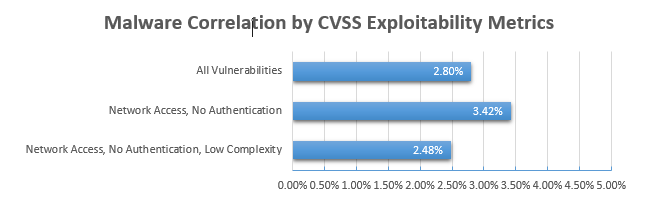
To evaluate which factors correlate the most with exploitation by malware, we examined our dataset of 12,700 vulnerabilities discovered between 2010 and 2015. We then incorporated our malware data, which consisted of 358 vulnerabilities (again, from 2010-2015) that are or have been associated with active malware. This leads to an overall malware exploit rate of about 2.8%. The question we want to investigate in this post is: Which factors lead to increased risk of malware exploitation?
The Common Vulnerability Scoring System (CVSS) measures how easy it would be for a hacker to exploit this vulnerability and access the data. Many of these vulnerabilities can be found in the National Vulnerability Database (NVD).
The CVSS is updated regularly to include the latest vulnerability information. The CVSS v2 was updated to the v3 several years ago to account for the changing security requirements, with the CVSS v3.1 being the latest version.
The CVSS is not the same as the Common Vulnerabilities and Exposures (CVE), which is a list of publicly disclosed vulnerabilities and what is known about them. The CVSS scores these vulnerabilities based on the hacker’s ability to wage an attack.
Incident response and security teams use this information to identify potential weak points and prioritize their remediation resources based on the likelihood of an attack.
The CVE is a large database of known vulnerabilities. However, it also includes a description, dates of known attacks, and comments about the problem.
CVSS base scores are divided into three categories, each with three labels:
Based on these base metrics, the CVSS security vulnerability score seems like a good place to start. It makes sense that an attacker would look for the vulnerabilities that are easiest for them to exploit. There’s just one problem…
With only about 3% of vulnerabilities having active malware associated with them, that means that relying on CVSS exploitability alone will give you a lot of false positives. Even worse, the malware correlation rate is almost exactly the same for vulnerabilities with the highest exploitability scores.
Just because a vulnerability has a high score on the CVSS, the chances of the hacker successfully exploiting the system may be low. The opposite may also be true. The threat may have a low CVSS score, but it may pose an even greater danger to your organization.
So, the CVSS Exploitability scores clearly don’t help you prioritize, but that doesn’t mean the theory behind them is wrong. Our research shows that attackers tend to take the path of least resistance when creating an attack vector and attempting to compromise a system. So, what tools make an attacker’s job easier, and how can we use them to improve vulnerability management?
The Exploit Database and Metasploit are two collections of the most widely used sources of public exploit code. Our analysis shows a high correlation between a vulnerability being present in one (or both) of these databases and it having malware associated with it.
While exploitability is clearly an important piece of the puzzle, it still can’t entirely explain which vulnerabilities attackers choose to target. This is because attackers think in terms of Return on Investment, not just how easy a vulnerability is to exploit. As an example, let’s look at two vulnerabilities: CVE-2011-4858 and CVE-2014-1776.
CVE-2011-4858 is in the Exploit Database, has a Metasploit module, and has a CVSS exploitability score of 10.0. It should be easy to exploit — and yet, it has no active malware associated with it. CVE-2014-1776, on the other hand, is not present in the Exploit Database and doesn’t have a Metasploit module. It requires a fairly complicated exploit — and yet, it is exploited by multiple malware kits. Why? In order to answer this question, we need to look at another part of CVSS: the impact sub-score.
The CVSS impact sub-score evaluates whether there would be a complete, partial, or no loss in each of three categories:
CVE-2011-4858 is a resource management error that can result in a partial loss of information availability and no loss of confidentiality or integrity. CVE-2014-1776, on the other hand, can allow attackers to execute arbitrary code, resulting in the complete loss of confidentiality, integrity, and availability.
Nearly all vulnerabilities could result in some data loss, but there is a special group of vulnerabilities that can result in a complete loss of confidentiality, integrity, and availability. These “triple threat” vulnerabilities account for less than one-third of vulnerabilities since 2010 in our database but make up nearly 90% of vulnerabilities with active malware. In other words, when evaluating the likelihood of exploitation, it is important to look at the impact in addition to ease of exploitation.
While the features discussed so far are certainly important in predicting whether or not a vulnerability has malware correlated with it, these predictors still are not enough to effectively differentiate between vulnerabilities with malware and those without malware. To fill in the gaps, we introduce one more feature: Twitter mentions. Recent research indicates that social media in general, and Twitter, in particular, is quickly becoming the go-to way for hackers to share information about exploitable vulnerabilities. NopSec collects Twitter data for all vulnerabilities in our database and uses this information to help organizations narrow in on the most dangerous ones.
The vast majority of vulnerabilities have 0 or 1 mention on Twitter. This means that vulnerabilities with a high number of tweets are “special” in some way – could it mean that vulnerabilities with high Twitter mentions are more likely to be correlated with malware? The median number of tweets for vulnerabilities associated with malware is 18, indicating that there may be some correlation between a high number of tweets and malware.
Now let’s focus on only the most talked about vulnerabilities — those with more than 100 tweets. Are these vulnerabilities more likely to have malware associated with them? Yes, just over half of vulnerabilities with more than 100 tweets have active malware in our database. Adding in the other features we have discussed (public exploits and complete loss of data), we find that the malware correlation rate is even higher: 92.75%.
So, what do these statistics tell us, and how can we use them to inform vulnerability prioritization better? Because organizations have limited time and resources, remediating every vulnerability is often not possible. Instead, organizations must prioritize the most dangerous vulnerabilities to maximize the impact of remediation. Our research indicates that if an organization were to choose a vulnerability at random to remediate, they would have a less than 3% chance of choosing a vulnerability with malware correlation. Focusing on vulnerabilities with the maximum CVSS Exploitability score would yield similar results. However, if an organization focused on vulnerabilities with a public exploit, a Metasploit module, a potential complete loss of data, and greater than 100 mentions on Twitter, they would have a 93% chance of remediating a vulnerability with malware. These features help an organization use its limited resources in a more efficient way, choosing the most dangerous vulnerabilities to focus on.
NopSec’s Unified VRM incorporates all of these factors (and more!) into its Business Risk Score, automating vulnerability prioritization and helping organizations reduce their risk as efficiently as possible.