5 Reasons Why Attack Surface Management MUST Be Part of Your VA Program
- Sep 29, 2021
- Guest Author

Back in 2019, when I was a research analyst at Gartner, I started to see a monumental shift in how organizations were looking at identifying and managing their rapidly expanding external perimeter(s). Many organizations were – and still are – going through a significant digital transformation, and it has become a considerable challenge to secure. Many organizations were seeking automated solutions that could expedite the discovery of their downstream relationships and partnerships to understand better which IT infrastructure could potentially be exposed and vulnerable to an attack.
Before this, a web application or online service could be better controlled. Your organization created, developed, and secured it, and every element of the IT infrastructure that supported that service was under your control. Everything migrated to the cloud changed how business applications were hosted, managed, and ultimately accessed by users.
Simultaneously, organizations started to emphasize addressing their vulnerabilities and, more specifically, address zero-day exploits faster than before. This forced cybercriminals to evolve their tactics to go upstream to a much weaker target, the supply chain, where they could infect a single, open-source component that had the potential to be distributed ‘downstream” where it could be strategically and covertly exploited.
In that year, over 300 cybersecurity incidents impacted supply chain entities. After conducting extensive research and analysis into this, I suspected that this was only the “tip of the iceberg. Unfortunately, I was proven to be right not too long after. What soon followed was a tidal wave that resulted in a 430% increase in attacks from May 2019 to May 2020. The peak of this mountain has yet to be seen. After meeting with hundreds of organizations, CISOs, and CIOs who experienced data breaches in 2019, I determined that this needed to be a dedicated approach. This is now termed by Gartner as Attack Surface Management.
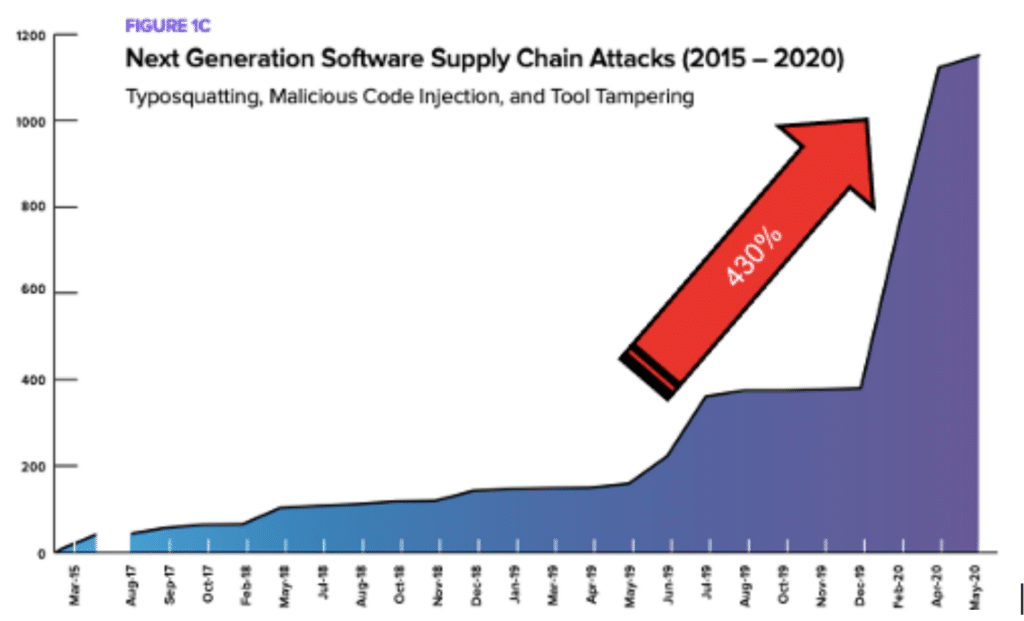
Source: SD Times
So what is an attack surface, and why should we manage it?
An attack surface is the total number of points/vectors through which an attacker could try to enter your IT environment. As defined by Gartner, Attack Surface Management (ASM) “refers to the processes, technology and professional services deployed to discover external-facing enterprise assets and systems that may present vulnerabilities. Examples include servers, credentials, public cloud service misconfigurations, and third-party partner software code vulnerabilities that malicious actors could exploit.”
Not all ASM solutions and approaches are created equal, however. Here are 5 critical capabilities that all ASM solutions must have to be successful.
NopSec can help identify and mitigate your attack surface so you can take action now.
NopSec operates with one mission – to help people make better decisions to reduce security risks. An exciting addition to the NopSec solution is the ability to ingest attack surface data in real-time. This information is part of the NopSec analysis engine determining which vulnerabilities need to be addressed first.
Here are two examples where analyzing your attack surface makes NopSec more effective than other solutions, which have limited to no knowledge of an attack surface:
Are there new and previously unknown systems not being scanned for vulnerabilities or monitored from a security perspective? You cannot protect what you can’t see.
What is the level of criticality an asset has? If a system has a large number of applications running on it, or critical data, NopSec will automatically place a higher priority on remediating any vulnerabilities found on these systems.
The NopSec Team is passionate about building technology to help customers simplify their work, manage exposure risks effectively, and empower them to make more informed decisions. NopSec’s software-as-a-service approach to Cyber Exposure Management offers an intelligent solution to dramatically reduce the turnaround time between identifying critical vulnerabilities and remediation.
Learn how to manage your attack surface and exposure to threats by requesting a demo now.