E3 Engine: Engine Microservice That Evaluates, Explores and Enriches Vulnerabilities
- Apr 12, 2019
- Michelangelo Sidagni
When it comes to vulnerabilities, I always say: “not all vulnerabilities are created equal”. Some are more important than others, for some of the following reasons:
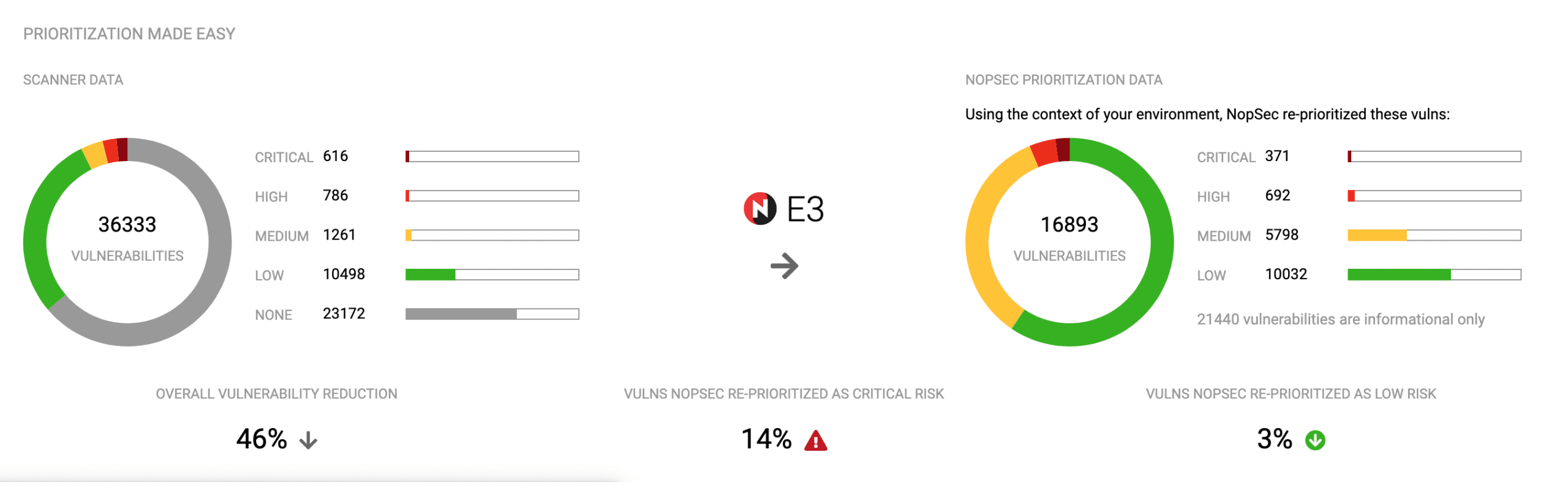
As part of Unified VRM, we have a separate engine microservice that helps make all the above mentioned decisions about vulnerabilities. And more. We call this comprehensive engine the E3 engine, which stands for “Evaluate, Explore and Enrich”. The E3 engine legerages a Machine-Learning algorithm to calculate our proprietary NopSec Risk Score based on the “features” and criteria described above. In calculating this risk score it also evaluates the value of each asset and it leverages that knowledge to refine the calculation.
Additional functions the E3 engine performs are:

Fig 1: Vulnerabilities in and out of the E3 engine
The imported and prioritized vulnerabilities are evaluated automatically for their real-world exploitability and their ability to kick-off a lateral movement chain across their organization’s internal network. So, prioritized vulnerabilities are matched with existing public exploits in order to exploit them.
These exploits are executed in very specific and controlled conditions and – when possible – reverse shells obtained. After a reverse shell is obtained the following lateral movement chain is initiated:
In this case the process starts with the vulnerabilities’ exploitation. The process is aimed at proving that starting with vulnerabilities an attacker can move laterally throughout the network laterally bypassing a series of security controls until arriving at the total Domain compromise.
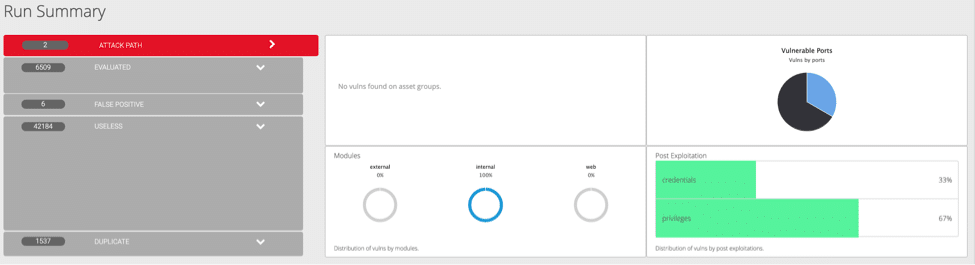
Fig. 2: Various categories of vulnerabilities and Attack Path
NopSec UVRM uses Data Science and Machine Learning Techniques to evaluate the probability that a certain vulnerability could be used in malware, exploits and targeted attacks at any given point in time.
At the same time, the E3 engine practically evaluates how those same vulnerabilities could be exploited and privileges escalated to move laterally to “conquer” more important targets in the network. This could be used for vulnerability prioritization, for security control validation and for breach / attack simulation. The objective is the same though: demonstrate practically how important is to fix vulnerabilities promptly and how easily an attacker leverage foothold on a host system to compromise highly valued network and application assets.
In this sense, NopSec’s new Unified VRM is both a vulnerability risk management platform and a breach and adversarial simulation platform.

Fig. 3: Graphical journey from imported vulnerabilities to lateral movement actions