SMBMap: Wield it like the Creator
- Mar 06, 2020
- Shawn Evans
The tool “SMBMap” was created nearly seven years ago. Originally based on a Python library called PySMB, it has since migrated to Impacket and evolved from a half-baked idea to a more mature tool worthy of inclusion in distros such as Kali Linux, among others. While its feature set has grown, the core functionality that inspired its creation and ultimate utility has remained unchanged and is just as relevant today as it was seven years ago.
You can access Gibhub version from here.
SMBMap is at its core an SMB client. SMB or server message block is a network communications protocol used to share resources such files, drives, and printers and interprocess communications called named pipes. SMB protocol was invented around 1985 by engineers at IBM, but not widely adopted until the early 90s when Microsoft pushed the protocol into their server and consumer operating systems.
The SMB protocol was initially underpinned by NetBIOS to provide an easy means for nodes to identify SMB services on the network. While this solution was functional, NetBIOS is a broadcast protocol, which causes significant network congestion, particularly in large environments. NetBIOS was eventually superseded by Dynamic DNS, and performance further increased with changes to the protocol in SMB v2.0 and v3.0.
The protocol provides an inter-process communication mechanism, which facilitates functions such as remote administration and authentication. For authentication, SMB protocol initially relied on LAN Man and NTLM, and was later enhanced to support NTLMv2 and Kerberos authentication. In an over simplified context NTLM is analogous to local authentication where Kerberos is associated with active directory server authentication. While this isn’t technically accurate, it helps conceptualize how SMB handles authentication. For our purposes, SMBMap only leverages NTLM authentication. When a client authenticates to an SMB resource, the domain specified in the request instructs if the credentials are to be compared against a local SAM hive or passed to a domain controller for verification and validation. The primary difference between NTLM and Kerberos is that NTLM only authenticates the client, whereas Kerberos validates the client and server via a ticketing service.
SMBMap is a handy SMB enumeration utility used in penetration testing! While core OS utilities exist that provide the ability to query SMB servers for lists of shared resources, these tools lack the ability to enumerate privileges. SMBMap was developed to address this gap. The tool was created with penetration testing in mind. SMB shares within large corporate network environments represent a substantial attack surface. It’s something of a rabbit hole or the wild west, and the larger the size of a network the more difficult securing these resources becomes.
As penetration testers, it is our duty to evaluate and exploit risk. The confluence of complex networks and limited time necessitates the ability to quickly and efficiently identify critical resources (domain controllers, database servers, web servers, etc) and discover means through which they could be targeted in attacks that could hopefully result in remote command execution. The notions of complexity and finite time introduces compromise. There’s never enough time to exhaustively evaluate everything, but sufficient time to identify the most critical areas of risk. SMBMap can be integrated into a testing methodology that facilitates the mass evaluation of SMB shared resources in a relatively quick and efficient manner, commensurate with the constraints of an engagement. This is why SMBMap exists, and the reason why after seven years I still use it on every single internal network assessment. It’s an enormous blind spot in most organizations, and prior to SMBMap it remained difficult to know the true risk lurking in the data being shared via SMB.
First, keep in mind that SMBMap fills a fairly niche gap within a larger penetration testing methodology. SMB is a protocol ripe for exploitation, exemplified by the abundance of incredible tools available to the pen testing community. Many of these tools have functional overlaps. After all, they all in some way shape or form communicate via SMB. But, they all fulfill a different need, and I’d like to briefly cover general use cases for other SMB tools.
Enum4Linux is an older tool, but it still checks out. It’s a Perl script, but really it’s a well thought out wrapper for smbclient, nmblookup, and rpcclient. The primary benefit of Enum4Linux is the ability to quickly dump data from servers with a NULL session enabled. On your vanilla workstation this typically means you have limited access to shared data. However, on a domain controller you can hit the ground running in your assessment and dump the user accounts, groups, group memberships, and in some instances password policy information. There’s nothing quite as nice as getting a complete list of domain usernames just five minutes into an engagement.
Metasploit is a framework of tools, not a single tool, and it is packed with modules dedicated to interacting with SMB servers. While the functionality is deep, I most often use MSF for the “smb_login” and “smb_enumusers_domain” modules. The “smb_login” module is well suited for password spraying attacks to exploit weak password vulnerabilities. For example, identifying accounts protected by a weak password such as “Password1”. Once you’ve achieved remote command execution on a number of systems, the “smb_enumusers_domain” module provides a great way to quickly enumerate what users are logged into a system. This is very helpful in identifying systems that have a privileged account (such as a domain admin) logged in, which aids in prioritizing systems for compromise.
Responder is a clever man-in-the-middle tool that takes advantage of broadcast protocols, such as LLMNR and NetBIOS, to poison name resolution responses. Although modern versions of the SMB protocol no longer rely on NetBIOS for name resolution, it is backwards compatible with NetBIOS. Responder provides a great means through which NetNTLMv2 hashes can be intercepted in transit as a result of the poisoned name requests. As hashes are intercepted, it’s then possible to use “ntlmrelayx.py” (included in the wonderful Impacket library) to relay these hashes to hosts that lack the protection of SMB signing. If you’re lucky you intercept and relay the hash of an administrator and do things like remotely execute arbitrary commands. Who doesn’t love that?
So, how can SMBMap be used in an offensive security engagement? The obvious answer is that it can enumerate shares, but there’s more tactful ways to evaluate and exploit risk with SMBMap. Let’s review some use cases for common attacks.
Identifying a NULL session on a system can grant unauthorized access to a wide variety of resources, up to and including remote command execution (though rare). This is a nice way to shoot for low hanging misconfigurations across multiple hosts. The idea is simple – use no username, no password, and get a session anyways. The syntax is simple:
$ ./smbmap.py –host-file smb-hosts.txt

SMB services represent a substantial attack surface within most large corporate network environments. Each SMB server can potentially host hundreds of gigabytes of data. Storing massive volumes of data is relatively cheap. As pen testers we’re faced with the challenge of finding specific needles in a pile of simil-looking other needles. SMBMap has features designed specifically to address this challenge. SMBMap can recursively (-R) or non-recursively (-r) enumerate files on a share drive, and automatically download any files that match a user defined regular expression pattern (-A ‘pattern’). When performing a recursive search SMBMap accepts arguments that can limit the traversal depth to increase performance (–depth). Furthermore, SMBMap can exclude certain shares (–exclude), such as IPC$ or ADMIN$, to eliminate time wasted traversering shares that rarely (if ever?) contain sensitive files.
$ ./smbmap.py –host-file smb-hosts.txt u ‘jsmith’ -p ‘Spring!2020’ -q -R –depth 2 –exclude ADMIN$ IPC$ -A ‘passw’
–host-file: file containing a list of hosts, one host/IP per line.
-u: account to authenticate with
-p: password for account
-q: quiet the verbosity of the output, excludes shares with “no access” or listing drive contents when performing a search
-R: perform a recursive search
–depth: recursive traversal depth, avoid the rabbit holes
–exclude: exclude specific shares that rarely contain interesting files
-A: auto download flag that uses a regular expression pattern to match against filenames
Using SMBMap I’ve had the opportunity to evaluate thousands of SMB shared resources. One of the surprisingly common resources I’ve found shared in corporate network environments is the root directory of web applications hosted within the internal network environment. Even more surprising is the frequency with which these resources are deployed with read and write permissions assigned to basic domain user accounts. The ability to write files to the web root of an application server introduces the possibility of server compromise and of remote code execution leveraging a web shell to execute arbitrary commands. The methodology is fairly straightforward, but the trick is isolating web servers vulnerable to this confluence of misconfigurations. Thankfully, SMBMap makes this process easy.
Web application servers all have a few things in common. They all host application source code and they (generally) host an application configuration file. The predictable nature of these constants make it fairly easy to craft a regular expression that captures these conditions across a large number of possible targets, as highlighted in the example below.
$ ./smbmap.py –host-file smb-hosts.txt -u ‘jsmith’ -p ‘Spring!2020’ -d ‘ACME’ -q -R –depth 3 –exclude ADMIN$ IPC$ -A ‘(web|server|global|index|login|logout|auth|httpd|config).(xml|config|conf|asax|aspx|php|asp|jsp|html)’
–host-file: file containing a list of hosts, one host/IP per line
-u: account to authenticate with
-p: password for account
-d: domain to authenticate against
-q: quiet the verbosity of the output, excludes shares with “no access” or listing drive contents when performing a search
-R: perform a recursive search
–depth: recursive traversal depth, avoid the rabbit hole of nested directories
–exclude: exclude specific shares that rarely contain interesting files
-A: auto download flag that uses a regular expression pattern to match against filenames
Useful tip: When files are downloaded the filename will always reflect the source host and path where the file was located, formatted: “<ip.address>-<share>_<path1>_<path2>_<pathN>.<extension>”. This makes it easy to zero on targets for continued attacks. The files listed below correlate with the files downloaded in the above sample command:
The above SMBMap command recursively scans SMB share drives for the presence of web application configuration and source code files, and auto downloads any files that match the specified pattern. Assuming the scan results in a few hits, the data gathered provides pen testers with a number of data points to plan additional attacks. Source code can be analyzed for the presence of credentials, SQL injection, encryption methods, and other areas of risk. Web application configuration files often contain clear-text database credentials, which could provide an attacker with direct access to the application database. These conditions alone introduce unnecessary risk, but it’s possible that the servers that hosted the files had write permissions granted to unauthorized users. In these instances, SMBMap can be leveraged to upload a web shell to the web root of the vulnerable application server.
One of the most basic uses and primary differentiators of SMBMap is to enumerate permissions across SMB share drives. This method of analysis allows a pen tester to quickly identify systems hosting a dense concentration of shared data, as well as systems deployed with misconfigured permissions.
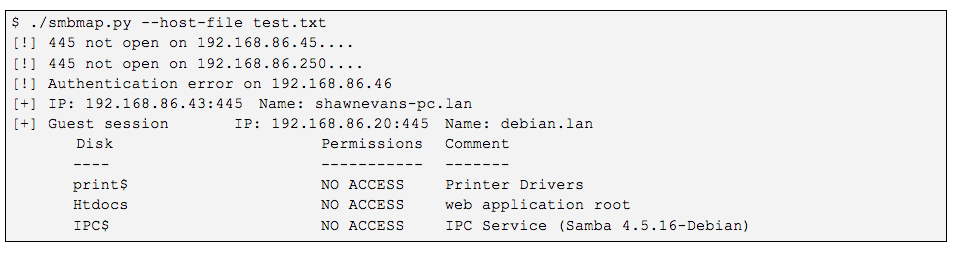
$ ./smbmap.py –host-file test.txt -u administrator -p asdf1234 -q
–host-file: file containing a list of hosts, one host/IP per line
-u: account to authenticate with
-p: password for account
-q: quiet the verbosity of the output, excludes shares with “no access” or listing drive contents when performing a search
The above command output indicates that READ and WRITE permissions were granted on the “htdocs” share hosted at IP address “192.168.86.20”. The ability to write to the web root is a strong indicator that remote command execution is achievable on the victim host.
Once the proper alignment of favorable attack conditions has been identified within an environment, it’s possible to compromise the web server by uploading a webshell to the misconfigured web application root directory. The command syntax is fairly simple
$ ./smbmap.py -H 192.168.86.20 -u ‘administrator’ -p ‘asdf1234’ -upload websell.php ‘htdocs\nopsec.php’
-H: IP address of target host
-u: account to authenticate with
-p: password for account
-d: domain to authenticate against
–upload: specify the local source and remote destination of the file being uploaded
Once uploaded it’s then possible to access the malicious webshell in a browser, and execute remote commands against the victim server, which can be leveraged in privilege escalation and intelligence gathering attacks, as demonstrated in the figure below.
SMBMap also supports the ability to start a PowerShell subprocess on a victim host and spider a local drive (such as C:\Users) for instances of a user defined regular expression within a file, kind of like a remote Grep. This method of identifying potentially sensitive files requires administrative rights on a system and the target host must operate on a version of Windows with PowerShell enabled. Assuming these conditions are satisfied, it’s possible to run this search across hundreds of hosts in tandem. It should be noted that this can cause a CPU spike on the victim host and take a significant amount of time to complete. Finally, this scan type requires that SMBMap be executed as ‘root’, because an SMB server is started on TCP port 445.
$ sudo ./smbmap.py –host-file test.txt -u administrator -p asdf1234 -F password
–host-file: file containing a list of hosts, one host/IP per line.
-u: account to authenticate with
-p: password for account
-F: regular expression pattern to search for in files
Note: This feature hasn’t been as thoroughly tested as it needs to be, and there are known bugs. The SMB server throws an exception in the threading library. Everything still works with the SMB server, however the error is annoying. There’s also the nagging issue that it lacks a graceful cleanup for the file content search. If SMBMap hits an exception before the jobs finish up, then those jobs will run until they are finished and any output files will remain in the %TEMP% directory.
SMBMap has additional features not thoroughly documented in this article, but they are relatively straightforward to use. Without going into much detail, please see the command references below.
-v: Return the OS version of the remote system
Sample output:
-g: Output drive listings in a Grep friendly format
Sample output:
-L: List all local and mapped drives on a target host
Sample output:
–admin: Only list hosts where you can execute commands
Sample output:
I hope this article provided some insights into how SMBMap can be used to make the job of finding needles in a stack of needles a more approachable challenge in a time boxed engagement. If you’d like to learn more about SMBMap, you can watch our SMBMap webinar.
In case you were curious – SMBMap is constantly being noodled with and updated. Here are some features currently in development: