Vulnerability Management FAQ
- Apr 15, 2021
- Michael Tucker
Vulnerability management lifecycle —Discovery, Detection, Prioritization, Remediation, Validation and Program Intelligence.
An asset is any hardware or software within your organization’s IT Environment. It includes but is not limited to servers, networks, desktops, smartphones, tablets, laptops, virtual machines, cloud-hosted technologies & services, web applications and IoT devices.
An Attack Surface is the total number of points/vectors through which an attacker could try to enter your IT environment.
Unified VRM (Unified Vulnerability Risk Management) is an award winning SaaS product that provides a complete end-to-end vulnerability risk management platform from Machine Learning-based prioritization, to remediation automation and orchestration. Unified VRM utilizes passive analysis, active validation and contextual enrichment to enable security teams to visually forecast threat risk, and dramatically reduce the time to remediation for critical security vulnerabilities across infrastructure, endpoints, and applications, as well as providing program metrics to executive stakeholders.
Unified VRM Program Intelligence Module allows customers to strategically align their vulnerability management program with their business goals — i.e. digital transformation, cost reduction, operational excellence, and growth. Unified VRM Program Intelligence Module provides holistic visibility into the real risks posed to organizations and measures the efficiency of their technology, people, and processes. The Program Intelligence Module simplifies communicating the overall vulnerability risk management program’s health to executives, board members, and other non-technical audiences. This module makes it possible to instantly answer executives’ ad hoc emergency vulnerability management questions and to provide them with customized metrics and benchmarking.
Unified VRM is powered by automation and machine learning. The solution dramatically reduces the turnaround time from identifying critical vulnerabilities to remediation and helps organizations avoid attacks and costly data breaches.
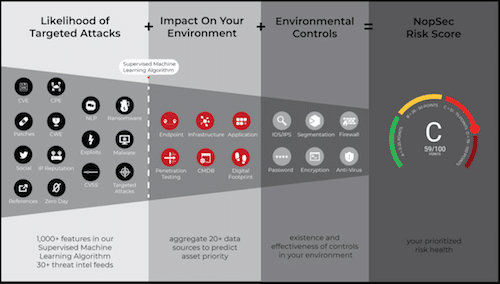
Our technology gathers historical data about vulnerabilities and leverages up-to-date threat intelligence in our ML algorithms to find vulnerabilities that are most likely to be used in malware or targeted attacks.
The NopSec vulnerability risk is derived from hundreds of features and 30+ threat intel feeds such as: Malware, Ransomware, Threat Actors or Campaigns, Public Exploit databases and social media feeds.
Unified VRM ingests data about your environment to give context to each vulnerability.
From that, we re-prioritize the vulnerabilities found in your environment according to their risk and criticality of the assets. We then put controls around the assets.