Resources
Explore our library of resources for Vulnerability Management & professional services, from white papers, to analyst reports, open source tools written by our research team, case studies, infographics, and more.
Filter by
-
Analyst ReportsNopSec Named A Visionary In The 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
-
WebinarsGet Real Results from AI-Powered Risk Scoring
-
WebinarsWhat It Means for Modern Risk Leaders: NopSec Named As A Visionary in the 2025 Gartner® Magic Quadrant™ for Exposure Assessment Platforms
-
WebinarsTurn a Year-End Pentest Into a 2026 Game Plan
-
Data SheetsNopSec Data Integration ServicesOur data integration services are designed to connect your security ecosystem, turning your disparate tools into a unified, proactive defense.
-
WebinarsNopSec + Wiz: Smarter Cloud Vulnerability Management
-
White Papers & eBooksOutcomes Over Operations: Is a managed vulnerability service right for you?
-
WebinarsReduce Risk Faster: Prioritize Remediation with AI
-
WebinarsThe Evolution and Future of Threat & Exposure Management
-
WebinarsHow the Legal Industry Embraces CTEM
-
Just in TimeJust in Time Bulletin: CVE-2025-33073 Reflective Kerberos Relay Attack
-
WebinarsApplication Security for Transformational Product Companies Live Webinar
-
Data SheetsPrioritize Cloud Risks with Wiz and NopSec IntegrationWiz and NopSec combine agentless cloud visibility with risk-based vulnerability scoring to help security teams cut through the noise and focus on the threats that matter most.
-
WebinarsAttack Path Management: Network and Authentication
-
WebinarsHow to Accelerate Vulnerability Management for Regulatory Compliance
-
WebinarsThe Power of Convergence: Uniting Proactive and Reactive Cybersecurity
-
Just in TimeJust in Time Bulletin: CVE-2025-23120 Veeam Backup and Replication RCE
-
White Papers & eBooksExpert Q&A – How to Embrace Modern Vulnerability Management for Compliance
-
White Papers & eBooksThe Definitive Playbook for Fed Horizontal Exam
-
WebinarsNopSec Webinar: Demystify Celebrity Vulnerabilities
-
Just in TimeJust in Time Bulletin: CVE-2024-43468 Microsoft SCCM Unauthenticated SQL Injection
-
Just in TimeJust in Time Bulletin: CVE-2024-0012 and CVE-2024-9474 Palo Alto Unauthenticated Remote Command Execution
-
Case StudiesHearst Technology Services Case StudyLearn how Nopsec’s Solution Streamlined Vulnerability Remediation, Improved Tracking And Reporting While Conserving Resources.
-
WebinarsTufin & NopSec Webinar: Prioritize Vulnerability Remediation with Attack Path Visibility
-
WebinarsNopSec Webinar: Using LLM to Map MITRE ATT&CK Taxonomies to CVEs
-
WebinarsNopSec Webinar: Data Scientist Deep Dive in Exposure Risk Scores
-
WebinarsNopSec Webinar: 2024 State of Exposure Management
-
EventsElevate Your Cybersecurity Leadership
-
White Papers & eBooks2024 State of Exposure Management: Download the Report
-
Just in TimeJust in Time Bulletin: CVE-2024-6387 regreSSHion Unauthenticated Remote Command Execution
-
Case StudiesMedia and Entertainment Customer Case StudyLearn how NopSec met and exceeding the cyber threat exposure management expectations for this media and entertainment giant.
-
Data SheetsOperationalizing for CTEM (Media & Entertainment): Phase 3 – Align for CTEM Data SheetPrepare your team for the implementation of the CTEM framework with the Operationalize for CTEM process - Phase 3: Align for CTEM
-
Data SheetsOperationalizing for CTEM (Media & Entertainment): Phase 2 – Optimize for CTEM Data SheetPrepare your team for the implementation of the CTEM framework with the Operationalize for CTEM process - Phase 2: Optimize for CTEM
-
Data SheetsOperationalizing for CTEM (Media & Entertainment): Phase 1 – Shifting for CTEM Data SheetPrepare your team for the implementation of the CTEM framework with the Operationalize for CTEM process - Phase 1: Shift for CTEM
-
Just in TimeJust in Time Bulletin: CVE-2024-24919 Check Point Security Gateway Information Disclosure
-
WebinarsNopSec Webinar: Security Insights WalkthroughWatch Rob Johnson - Director of Solutions Engineering - as he walks through the new Threat Vector, Velocity, Exceptions, and Team Performance Security Insights
-
Just in TimeJust in Time Bulletin: CVE-2024-3094 XZ/liblzma Backdoor
-
Just in TimeJust in Time Bulletin: CVE-2023-22527 Atlassian Confluence RCE
-
WebinarsNopSec Webinar: Monthly Platform Demo SeriesJoin our Director of Solutions Engineering as they walk you through the features and functionality of NopSec's platform.
-
Just in TimeJust in Time Bulletin: CVE-2023-22518 Atlassian Confluence Authorization Bypass
-
WebinarsNopSec Webinar: New Cyber Threat Exposure Management Platform WalkthroughWatch Rob Johnson - Director of Solutions Engineering - as he walks you through the features and functionality of NopSec's new Cyber Threat Exposure Management platform.
-
Just in TimeJust in Time Bulletin: CVE-2023-20198 Cisco IOS XE Web UI Authentication Bypass and Privilege Escalation
-
Just in TimeJust in Time Bulletin: CVE-2023-22515 Confluence Broken Access and Privilege Escalation
-
Just in TimeJust in Time Bulletin: CVE-2023-24489 Citrix ShareFile RCE
-
Just in TimeJust in Time Bulletin: CVE-2023-3519 Citrix NetScaler Gateway and ADC RCE
-
Just in TimeJust in Time Bulletin: CVE-2022-31199 NetWrix Insecure Object Deserialization RCE
-
Just in TimeJust in Time Bulletin: CVE-2023-34362 SQL Injection in Progress MOVEit Transfer Software
-
PodcastsHussein Syed: Healthcare InfoSec – where we are and where we’re headed
-
PodcastsJason Loomis: Seeing risk from all sides- holistic vulnerability management
-
PodcastsSailaja Kotra-Turner: How ”happy accidents” led to a career in IT
-
PodcastsEd Covert: Reducing risk trumps constant patching
-
PodcastsEd Harris: How to enter and thrive in the infosec industry
-
PodcastsJim Scott: How to make security and vulnerability management a priority
-
PodcastsJason Thelen: How to take a holistic approach to vulnerability management
-
Case StudiesCustomer Interview: Jermaine Blyther, Associate Director at Carrier Corporation
-
Case StudiesCustomer Interview: Matt Sharp, CISO at Logicworks
-
Case StudiesCustomer Interview: David McLeod, VP and CISO at Cox Enterprise
-
Case StudiesCustomer Interview: Luis Arzu, VP of Information Security at Urban One
-
Case StudiesCustomer Interview: Andrew King, Managing Director at OneMain Financial
-
Case StudiesCustomer Interview: Alex Bazay, CISO at Align
-
Data SheetsVulnerability Management Services Data SheetLearn about Vulnerability Management Services from the NopSec cybersecurity experts.
-
PodcastsKyle McNulty: How to reinvigorate the vulnerability management category
-
White Papers & eBooksThe Cyber Resilience Framework and Index: A Blueprint to Improve the Organization’s Cyber Attack DefendabilityUnderstand how, together, the Cyber Resilience Framework and Index deliver a unique cyber resilience blueprint.
-
PodcastsLeslie Forbes: Why it’s important for security practitioners to understand business logic
-
Data SheetsManaged Over-the-Top Testing Data SheetLearn about Managed Over-the-Top (OTT) Testing Services from the NopSec cybersecurity experts.
-
PodcastsTunde Oni-Daniel: How organizational culture affects consensus about the criticality of assets
-
PodcastsYabing Wang: How practitioners can use vulnerability management to improve business objectives
-
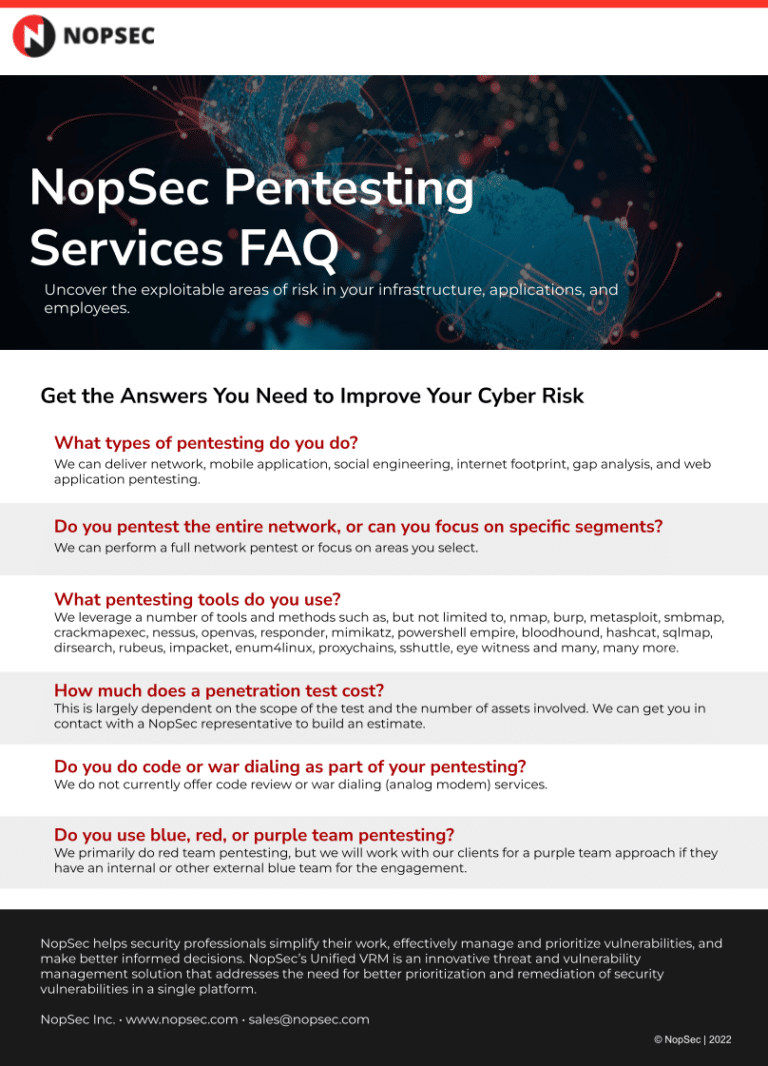
Data SheetsManaged Penetration Testing FAQ Data SheetGet the answers to your questions about Managed Penetration Testing Services from NopSec.
-
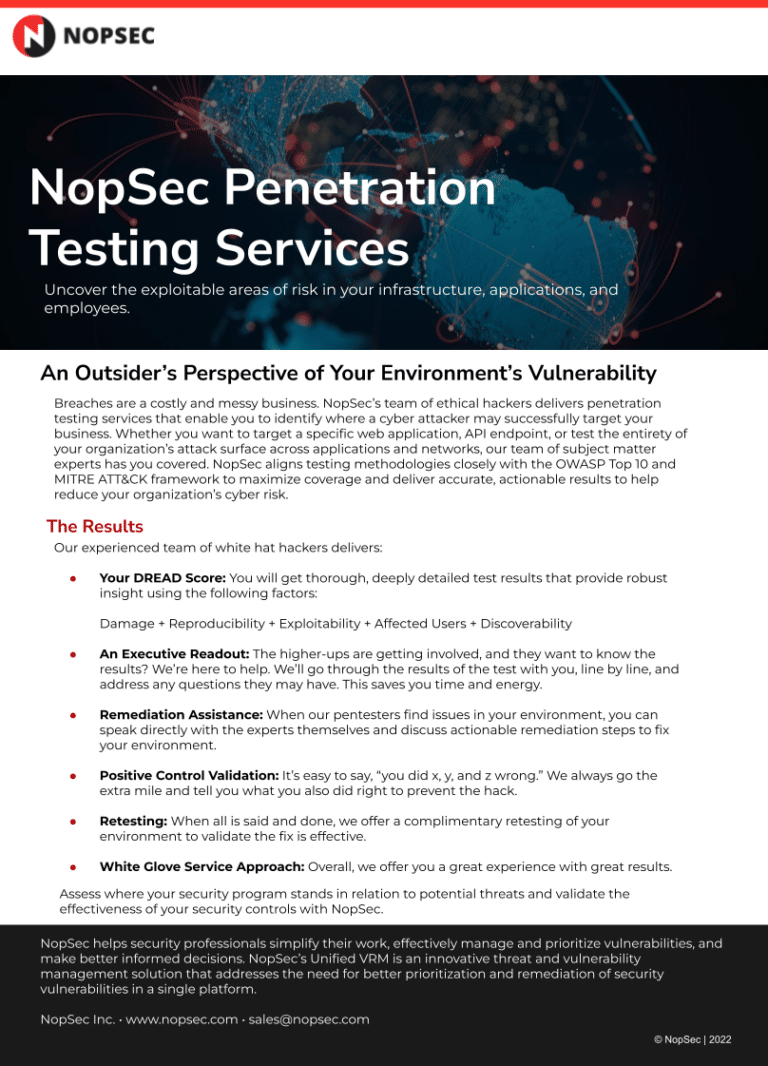
Data SheetsManaged Penetration Testing Services Data SheetLearn about Managed Penetration Testing Services from NopSec.
-
White Papers & eBooksNopSec Vulnerability Risk Management PlaybookGet everything you need to build a Vulnerability Risk Management Program from the experts.
-
PodcastsTim Brown: The role vulnerability management plays in proper cyber hygiene
-
Just in TimeJust in Time Bulletin: CVE-2022-37969 Windows CLFS Driver Privilege Escalation
-
PodcastsMatt Sharp: How to bridge the gap between risk management and core business outcomes
-
PodcastsDavid Kroening: How a 105 year old ad agency tackles vulnerability management with clients
-
PodcastsBetsy Lundsten: Automation and soft skills in vulnerability management
-
PodcastsJermaine Blyther: Weaknesses in the vulnerability management field
-
Just in TimeJust in Time Bulletin: CVE-2022-22972 VMWare Workspace ONE Access Authentication Bypass
-
PodcastsDavid McLeod: The state of vulnerability management
-
White Papers & eBooksCISOs on the Board: The Implications of the SEC’s Proposed Cybersecurity RequirementsSee how the SEC's proposed new cybersecurity requirements could change the state of the boardroom — and the role of the CISO.
-
WebinarsNopSec Webinar: SEC Pushing for CISOs on the BoardJoin NopSec and our panel of cybersecurity experts to discuss the SEC's new proposed requirements to add CISOs to boards of directors.
-
Just in TimeJust in Time Bulletin: CVE-2022-30136 RCE in NFSv4
-
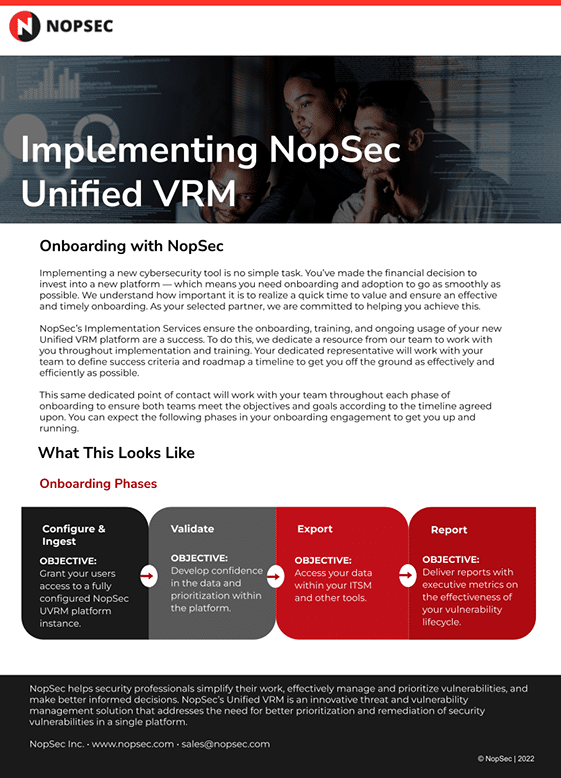
Data SheetsUnified VRM Implementation Services Data SheetLearn about the implementation process for NopSec Unified VRM.
-
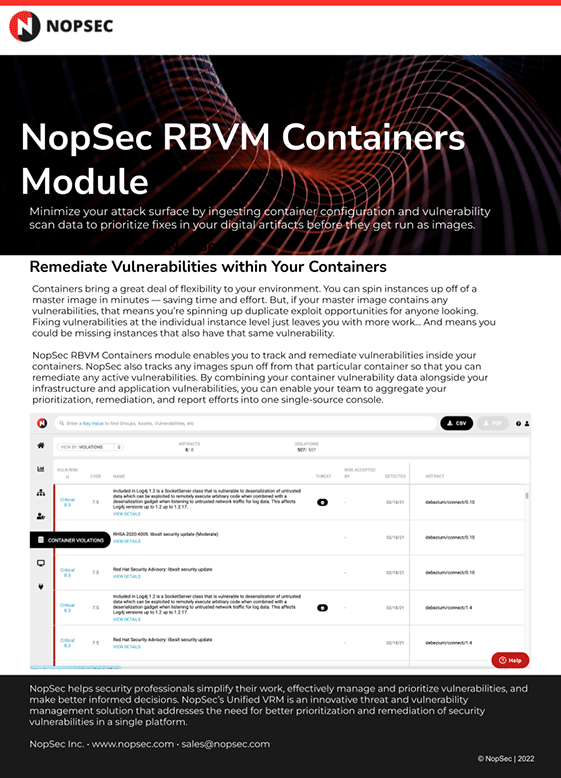
Data SheetsUnified VRM RBVM Containers Module Data SheetLearn about the NopSec Unified VRM RBVM Containers Module.
-
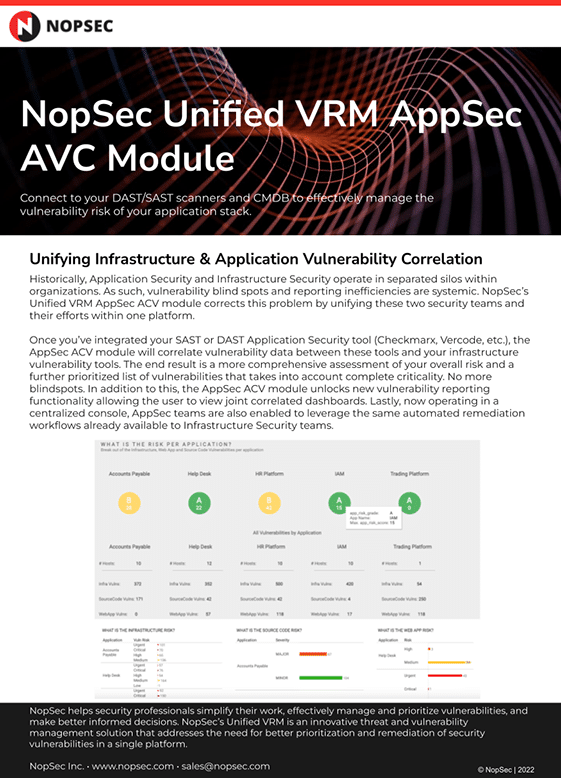
Data SheetsUnified VRM AppSec AVC Module Data SheetLearn about the NopSec Unified VRM AppSec AVC Module add-on.
-
WebinarsNopSec Webinar: Risk Scores in ContextHear from the Vulnerability Management experts about CVSS and putting risk scores in context.
-
White Papers & eBooksState of Vulnerability Management Report 2022NopSec has collected the insights of over 400 cybersecurity professionals to discover and quantify their day-to-day challenges, frustrations, and priorities.
-
Data SheetsUnified VRM Customer Success and StrategyWhen purchasing Unified VRM you'll also receive a dedicated Customer Success team to support and strategically guide your use of the platform.
-
Case StudiesNopSec UVRM Bottomline Outcome AssessmentHighTide Advisors performed a complete bottomline outcome assessment on NopSec's Unified VRM platform to reveal total cost of ownership.
-
Just in TimeJust in Time Bulletin: CVE-2022-30190 Microsoft Windows Support Diagnostic Tool RCE
-
Data SheetsUnified VRM Platform Scalability Data SheetLearn about the scalability capacities of the Unified VRM platform to meet the needs of various enterprise-level organizations.
-
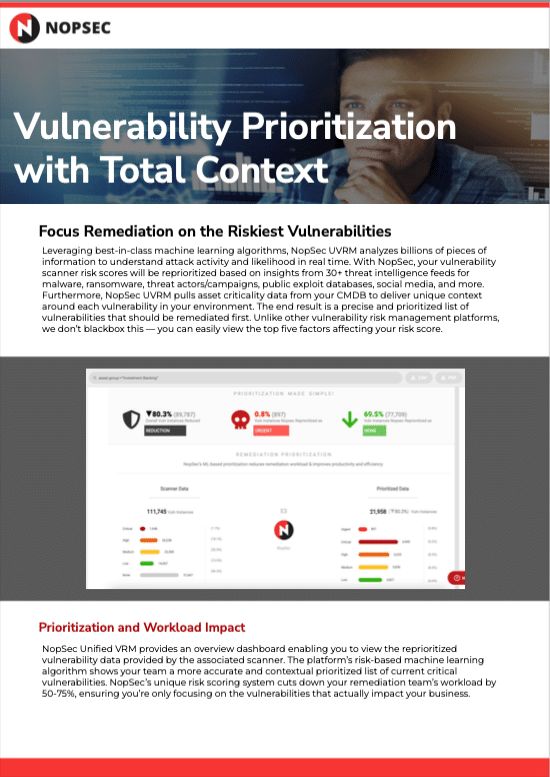
Data SheetsUnified VRM Vulnerability PrioritizationLearn how Unified VRM's machine-learning algorithm can improver your organization's ability to prioritize risk.
-
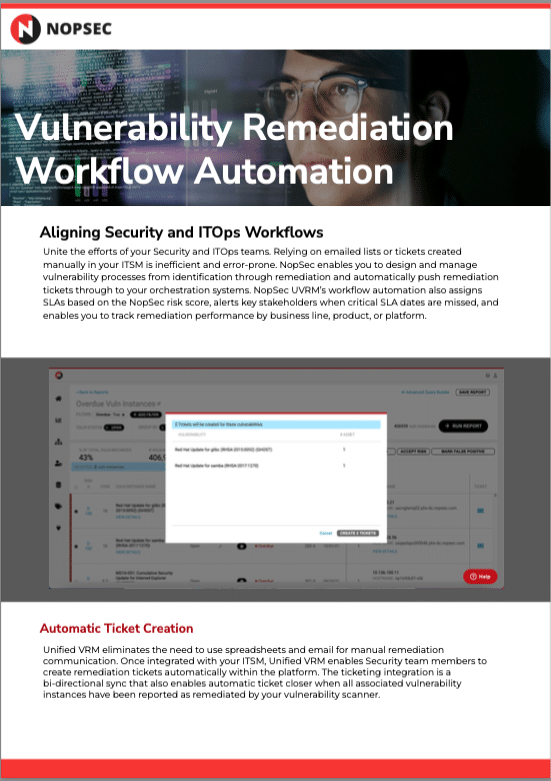
Data SheetsUnified VRM Remediation Workflow AutomationView the different remediation workflow automations Unified VRM can provide your Security team in this data sheet.
-
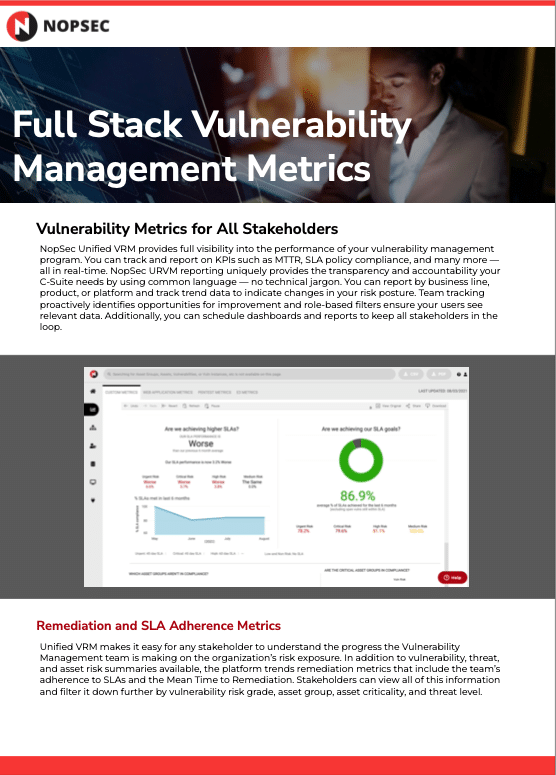
Data SheetsUnified VRM Full Stack Vulnerability Management MetricsTake a deeper look at the full stack vulnerability management metrics the Unified VRM platform offers Security teams.
-
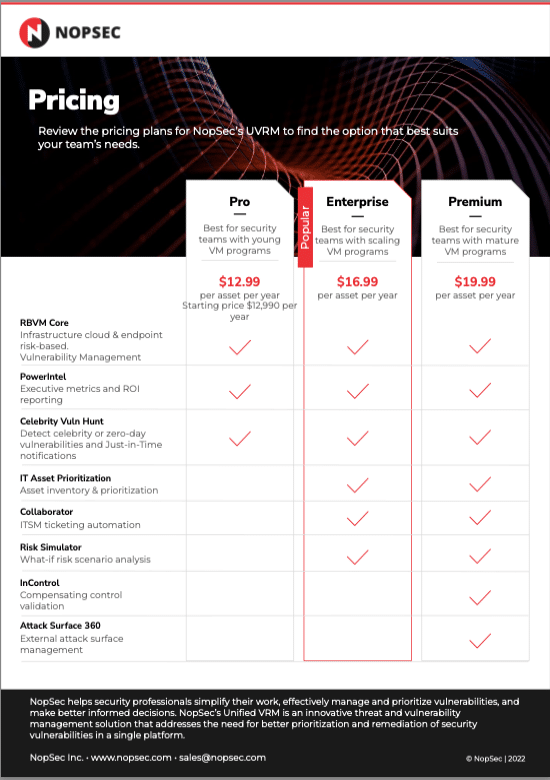
Data SheetsUnified VRM Product Pricing Data SheetSee a comparison of NopSec's Unified VRM feature packages, prices, and additional add-ons.
-
Data SheetsUnified VRM Product Overview Data SheetDiscover the solutions and value of NopSec's Unified VRM platform and how it can benefit your security program today!
-
Data SheetsUnified VRM Technical Support Levels Data SheetLearn how NopSec offers support options designed to deliver both maximum solution value and timely issue resolution depending on your needs.
-
Just in TimeJust in Time Bulletin: CVE-2022-22954 VMWare Workspace ONE RCE
-
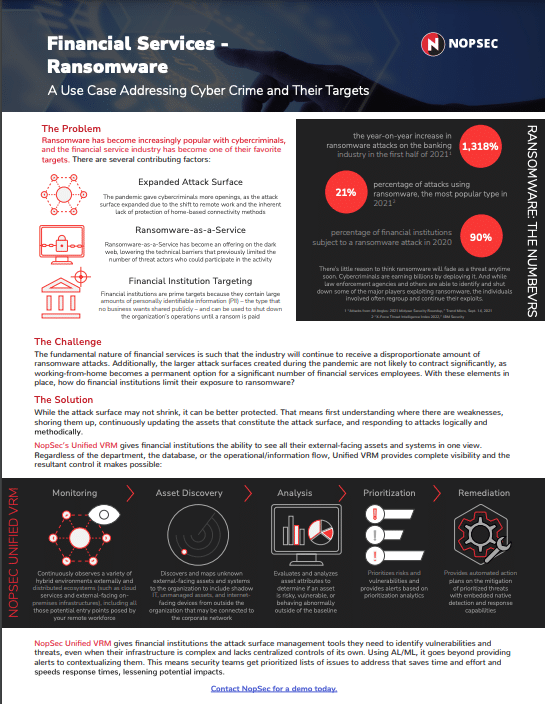
Data SheetsRansomware: Cyber Crime and their Targets in the Financial Services IndustryLearn how NopSec helps combat ransomware, the number one threat to financial services companies is this use-case data sheet.
-
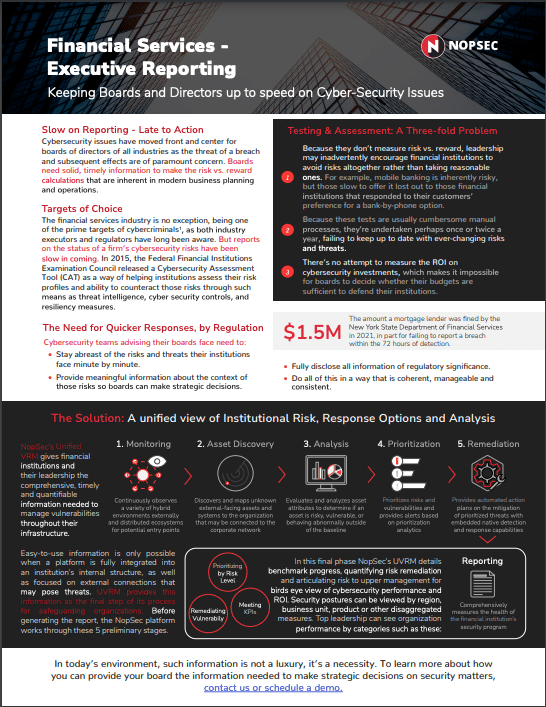
Data SheetsVulnerability Management Reporting for Executives in the Financial Services IndustryLearn how NopSec's industry-leading reporting helps prove security investment ROI for executives in the financial services space.
-
Data SheetsNopSec Managed Scanning ServiceDiscover the benefits of outsourcing your vulnerability management scanning to NopSec's seasoned professionals.
-
Just in TimeJust in Time Bulletin: CVE-2022-22965 Spring4Shell
-
Case StudiesGlobal Manufacturer Centralizes Vulnerability ManagementSee how NopSec's Unified VRM platform solved the security needs of a multinational appliance manufacturing giant.
-
Case StudiesUrban One’s New CISO Drives Efficiency and Risk ReductionSee how NopSec's Unified VRM platform delivered for media giant Urban One to improve their vulnerability management capabilities.
-
Case StudiesBatteries Plus Bulbs Powers Up Its Cybersecurity Effectiveness with NopSecSee how NopSec's Unified VRM platform consolidated security data and drove efficiency the Batteries Plus Bulbs corporation.
-
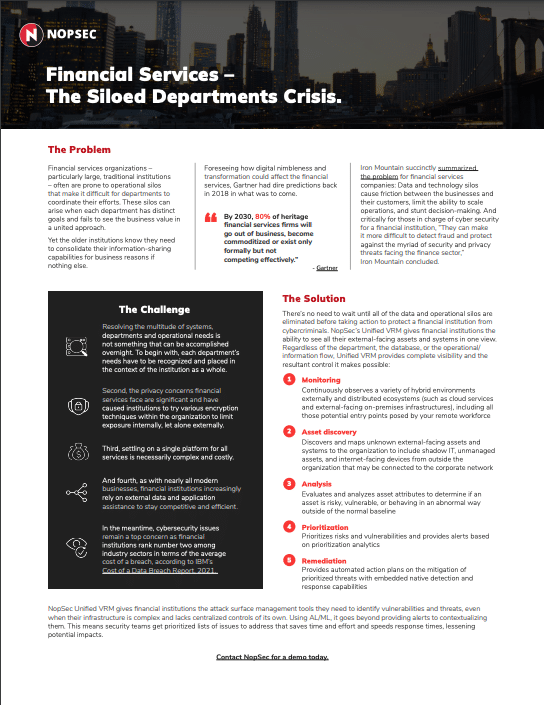
Data SheetsSolving the Siloed Departments Crisis in the Financial Services IndustryLearn how NopSec solves a crisis plaguing large, traditional financial services companies in this use-case data sheet.
-
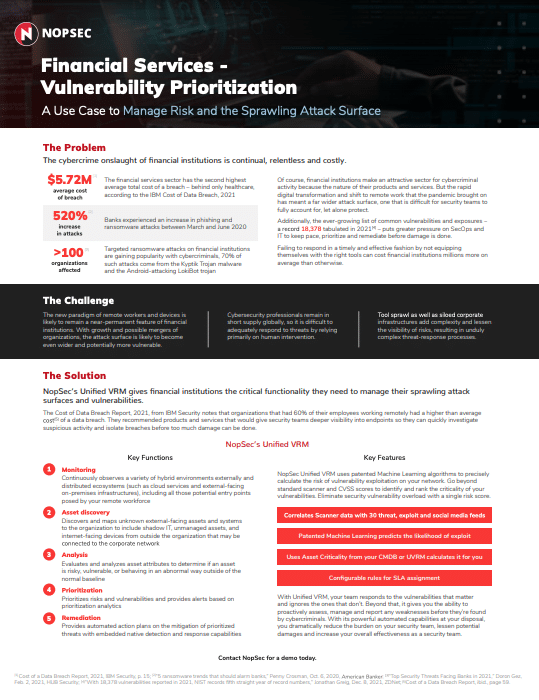
Data SheetsManaging Risk and the Sprawling Attack Surface in the Financial Services IndustryLearn how NopSec specifically helps manage vulnerability risk in the financial services industry in this use-case data sheet.
-
Just in TimeJust in Time Bulletin: CVE-2022-0847 Dirty Pipe
-
Just in TimeJust in Time Bulletin: CVE-2022-21999 SpoolFool
-
Just in TimeJust in Time Bulletin: CVE-2021-4034 PwnKit
-
WebinarsCelebrity Vulnerabilities 201 for Security ExecutivesGet an executives perspective on Celebrity Vulnerabilities and learn how build your security program to handle them efficiently.
-
WebinarsCVE-2021-44228 – Log4j “Log4Shell” Vulnerability – Attack Surface and ExploitationLearn what CVE-2021-44228 aka Log4Shell is, why it is so dangerous, and how you can protect your organization.
-
Just in TimeJust in Time Bulletin: CVE-2021-44228 Log4Shell
-
WebinarsCelebrity Vulnerabilities 101 for Security PractitionersGet a practitioners perspective on Celebrity Vulnerabilities and learn how to handle these unique risks.
-
White Papers & eBooksDon’t Let Celebrity Vulnerabilities Steal Your FocusAre Celebrity Vulnerabilities important or are they more often just shiny objects to divert your attention from what matters most?
-
White Papers & eBooksResources: Cyber Exposure Management WhitepaperLearn about the industry trends that are driving the transition of traditional Vulnerability Management into Cyber Exposure Management.
-
White Papers & eBooks2020 State of Vulnerability Management Report: CVE List, Vulnerability Detection & MoreReview the 2020 trends, phases, and maturity of the main areas of a vulnerability risk management program.
-
WebinarsCyber Exposure Management – The Evolution of Vulnerability ManagementLearn how the security industry is evolving from Vulnerability Management into the Cyber Exposure Management.
-
Data SheetsNopSec Unified VRM ROILearn the return on investment of an effective and successful Vulnerability Management program.
-
Just in TimeJust in Time Bulletin: CVE-2021-22005
-
Case StudiesLogicworks Case StudySee how NopSec provided solutions to meet the challenges of a leading cloud service provider - Logicworks
-
WebinarsBest Practices On Risk Based Vulnerability ManagementThe NopSec team walks you through best practices on risk based vulnerability management.
-
WebinarsManaged RBVMOn this podcast episode, hosted by Dr. Torsten George, you get a break down of managed RBVM.
-
WebinarsCybersecurity Program: Global Cybersecurity Programs in Portfolio ManagementOn this podcast episode the NopSec hosts Marvin Larry to discuss global cybersecurity programs in portfolio management industry.
-
WebinarsUnified VRM Program Intelligence ModuleThe NopSec team walks you through Unified VRM's program intelligence module.
-
WebinarsVulnerability Management in the Defense IndustryOn this podcast episode we host Luis Arzu to give us a look at vulnerability management in the defense industry.
-
WebinarsVulnerability Management in the Investment Management IndustryOn this podcast episode we hosted Bala Rajagopalan to walk us through vulnerability management in the investment management industry.
-
WebinarsVulnerability Management in the Financial Services IndustryOn this podcast episode NopSec hosts Tunde Oni-Daniel to get the inside on vulnerability management in the financial services industry.
-
WebinarsJoint Best Practices Managed Vulnerability ManagementThe NopSec team walks you through the best practices of managed vulnerability management.
-
WebinarsVulnerability Management in the Healthcare IndustryThe NopSec team hosts Russell Burrows to give us the inside on vulnerability management in the healthcare industry.
-
WebinarsBoard Engagement in Cyber Risk ManagementThe NopSec team teachs you how to get board engagement in cyber risk management.
-
WebinarsNovel Application Vulnerabilities You Should Fix Right AwayThe NopSec team breaks down novel application vulnerabilities you should fix right away.
-
WebinarsHow to Easily to Manage Your Vulnerabilities with Unified VRMThe NopSec team walks you through how to easily to manage your vulnerabilities with Unified VRM.
-
WebinarsSMB Tools with Shawn EvansShawn Evans of NopSec walks you through SMB tools to use for vulnerability management.
-
Webinars10 Vulnerabilities That You Should Fix ImmediatelyThe NopSec team walks you through 10 vulnerabilities that you should fix immediately.
-
WebinarsCrowdstrike Vulnerability Management: A Crowdstrike Store How ToUnified VRM is in the CrowdStrike store - learn the holistic approach to Vulnerability Risk Management.
-
WebinarsImportance of Network Contextual InfoThe NopSec team walks you through the importance of network contextual info.
-
WebinarsOffensive Security in Vulnerability ManagementThe NopSec team walks you through offensive security in vulnerability management.
-
WebinarsAsset Prioritization RecommendationThe NopSec team makes asset prioritization recommendations for you to action to improve your workflow.
-
WebinarsDiscovering the Value of Trending MetricsThe NopSec team walks you through discovering the value of trending metrics.
-
WebinarsPassword PlaygroundThe NopSec team walks you through the stats and analysis of passwords.
-
WebinarsNopSec Risk ScoreThe NopSec team walks you through the Unified VRM risk score.
-
WebinarsImportance of Data Deduplication for Vulnerability ManagementThe NopSec team walks you through how to dedupe vulnerabilities.
-
WebinarsHow to Make VM Easy from a UX Perspective VMThe NopSec team walks you through how to make VM easy from a UX perspective.
-
WebinarsMachine Learning in CybersecurityThe NopSec team walks you through machine learning in cybersecurity.
-
WebinarsBest Practices on Vulnerability Management MetricsThe NopSec team walks you through the best practices for vulnerability management metrics.
-
WebinarsTime is Money – Automate CVE to KBThe NopSec team walks you through automating CVE to hotfix KB.
-
WebinarsVulnerability OwnershipThe NopSec team walks you through defining vulnerability ownership.
-
WebinarsUsing Neural Networks to Hide ShellcodeThe NopSec team walks you through using neural networks to hide shellcode.
-
Webinars2019 Vulnerability Management PredictionsThe NopSec team walks you through their 2019 vulnerability management predictions.
-
WebinarsTime is Money – Simplifying Vulnerability Analysis with Machine LearningThe NopSec team explains how to simplify vulnerability analysis with machine learning.
-
WebinarsBash Tricks for PentestersThe NopSec team walks you through Bash tricks for pentesters.
-
WebinarsPentest Tricks: Out with Powershell, In with C#The NopSec team walks you through penetration test tricks replacing Powershell with C#.
-
WebinarsWhat Works in Penetration Testing – Same As It Ever Was?The NopSec team breaks down what works in penetration testing and if it's the same as it ever was.
-
WebinarsIdentify the Attack Surface of a Web ApplicationThe NopSec team walks you through the attack surface detector for better penetration testing.
-
WebinarsIntroducing the NopSec Cloud Security ModuleNopSec introduces the new cloud security module for Unified VRM.
-
WebinarsThink Like a Hacker: Top 10 Biggest Cyber ThreatsThe NopSec team walks you through the top 10 biggest cyber threats.
-
WebinarsVulnerability Management as Devops PracticeThe NopSec team walks you through vulnerability management for Devops practice.
-
WebinarsSelecting the Right Penetration Test ProviderThe NopSec team walks you through selecting the right penetration test provider.
-
Webinars2016 State of Vulnerability Risk Management ReportThe NopSec team walks you through the 2016 state of vulnerability risk management report.
-
WebinarsMaximize Your Role Based Access ControlThe NopSec team walks you through maximizing your role based access controls.
-
WebinarsHIPAA: Beyond IT ComplianceThe NopSec team walks you through HIPAA and going beyond IT compliance.
-
Webinars2016 State of RansomwareThe NopSec team walks you through the 2016 state of ransomware.
-
WebinarsSocial Engineering in Penetration TestingThe NopSec team walks you through social engineering in penetration testing.
-
WebinarsThe NYDFS Proposed Cybersecurity RegulationsThe NopSec team walks you through the NYDFS proposed cybersecurity regulations.
-
WebinarsProduct Demo: NopSec Unified VRMThe NopSec team walks you through a product demo of the Unified VRM.
-
WebinarsCybersecurity Threats to the Energy and Industrial SectorThe NopSec team walks you through cybersecurity threats to the energy and industrial sector.
-
Webinars4 Questions to Ask Your VRM ProviderThe NopSec team breaks down the 4 questions to ask your VRM provider.
-
WebinarsHow Hackers Exploit Weak PasswordsThe NopSec team walks you through how hackers exploit weak passwords.
-
WebinarsPhishing 101: Don’t Take the BaitThe NopSec team walks you through phishing 101 and how to not to take the bait.
-
WebinarsFeature: Unified VRM Time Based ReportingThe NopSec team walks you through Unified VRM's time based reporting feature.
-
Webinars5 Common Tools For Penetration TestersThe NopSec team walks you through 5 common tools for penetration testers.
-
WebinarsCIS 20 Controls: How Unified VRM Can HelpThe NopSec team walks you through CIS 20 controls and how unified VRM can help.
-
WebinarsTop 5 Cybersecurity Threats of 2017The NopSec team walks you through the top 5 cybersecurity threats of 2017.
-
WebinarsNYDFS Cybersecurity Regulations 23 NYCRR 500: Implementation ReviewThe NopSec team reviews the implementation of NYDFS cybersecurity regulations 23 NYCRR part 500.
-
Webinars5 Benefits of Retaining a Virtual CISOThe NopSec team walks you through 5 benefits of retaining a virtual CISO.
-
WebinarsCyber Insurance 101: Top 3 Things You Need to KnowXL Catlin’s Vice President, NopSec’s Chief Product Officer, and Dell Fellow Tim Brown walk you through cyber insurance 101 and the top 3 things you need to know.
-
WebinarsLab Demo Analysis: The Shadow Brokers Leaked Equation Groups Hacking ToolsThe NopSec team walks you through analysis of the latest NSA-linked Equation Group hacking tool.
-
WebinarsWomen in Cybersecurity: Engaging A Diverse WorkforceThe NopSec team walks you through women in cybersecurity and engaging a diverse workforce.
-
WebinarsNYDFS Cybersecurity Regulations Milestone ReviewThe NopSec team reviews NYDFS cybersecurity regulations milestones.
-
WebinarsImplant Extravaganza: Analyzing C2 Attack VectorsThe NopSec team walks you through an implant extravaganza by analyzing C2 attack vectors.
-
WebinarsProtecting Your Crown Jewels: the Data, the People, the ApplicationsThe NopSec team walks you through protecting your crown jewels- the data, the people, and the applications.
-
Data SheetsNopSec Risk Score Data SheetLearn how the NopSec Risk Score improves vulnerability prioritization by leveraging the power of machine learning!
-
Data SheetsNopSec CrowdStrike Joint Solution BriefLearn how NopSec UVRM is the perfect partner for CrowdStrike Falcon Spotlight and empowers security teams to maximize their impact.
-
White Papers & eBooksNopSec Unified VRM Security and GovernanceRead the measures NopSec takes to ensure customer data is secure and complies with regulations.
-
White Papers & eBooksHow to Communicate VM Program Progress: Vulnerability Management MetricsLearn how to effectively track and articulate the progress of a VM program to stakeholders.
-
White Papers & eBooksWhitepaper: Penetration Testing Best Practices GuideRead more to quickly understand the choices you have available for successful penetration testing.
-
White Papers & eBooksDevops Security for AutomationLearn how to leverage dev tools to automate manual procedures and integrate frictionless remediation.
-
White Papers & eBooksChoose the Right VRM TechnologyLearn how the right technology can boost your organization's existing vulnerability management program.
-
White Papers & eBooksBeyond HIPAA Compliance: Preventing Security Breaches in HealthcareLearn how to shift from the “Checklist Mentality” to “Beyond Compliance”.
-
White Papers & eBooksSecure C Suite Buy-in for an Information Security ProgramLearn how to prepare your business case and support it with industry specific use cases.
-
White Papers & eBooks2016 State of Ransomware Report: What is Ransomware & How to Prevent It & Other TopicsDiscover one of the biggest digital security threats to all types of organizations: Ransomware.
-
White Papers & eBooksGrowing Cybersecurity Threats to the Energy Industrial SectorsDiscover damage control strategies that can help reduce the impact of or prevent cyber attacks.
-
White Papers & eBooks2017 State of Vulnerability Risk Management ReportLearn the trends that emerged in 2016 and get insights to improve your cybersecurity program in 2017.
-
White Papers & eBooks2018 Remediation Vulnerability Risk Management ReportNopSec presents top findings from our third annual survey of IT Security and Risk practitioners.
-
White Papers & eBooks2018 Top Cybersecurity Threats: Cryptojacking, Ransomware & More
-
White Papers & eBooks2016 State of Vulnerability Risk Management Report: Security and Vulnerability Management & Other TopicsExplore the 2016 threat landscape and walk away with practical action items.
-
White Papers & eBooks2017 State of Vulnerability Risk Management Report: Remediation Risk Management & Other TopicsExplore the 2017 threat landscape with the latest State of Vulnerability Risk Management Report.
-
White Papers & eBooks2018 State of Vulnerability Risk Management ReportReview the 2018 analysis trends in vulnerability risk management and how you can prepare for next year.
-
Just in TimeJust in Time Bulletin: CVE-2021-1675
-
Just in TimeJust in Time Bulletin: CVE-2021-21985
-
Just in TimeJust in Time Bulletin: CVE-2021-31166
-
Just in TimeJust in Time Bulletin: Zero-Day Flaws in SonicWall Email Security Product Exploited in Attacks
-
Just in TimeJust in Time Bulletin: CVE-2021-28480 Four More Zero-day Vulnerabilities in Microsoft Exchange Server
-
Just in TimeJust in Time Bulletin: Four Zero-day Vulnerabilities in Microsoft Exchange Server
-
Just in TimeJust in Time Bulletin: CVE-2021-21972
-
Just in TimeJust in Time Bulletin: CVE-2021-3156
-
Just in TimeJust in Time Bulletin: What is Sunburst?
-
Just in TimeJust in Time Bulletin: Bad Neighbor
-
Just in TimeJust in Time Bulletin: Zerologon
-
Just in TimeJust in Time Bulletin: SIGRed
-
Just in TimeJust in Time Bulletin: Spectre and Meltdown Vulnerabilities
-
Just in TimeJust in Time Bulletin: Bad Rabbit
-
Webinars2020 DBIR: Analysis of the Verizon 2020 Verizon DBIR ReportMichelangelo Sidagni reviews the Verizon 2020 DBIR report highlights and discusses the importance for vulnerability management.
-
White Papers & eBooksDDoS: The Threats That Won’t Go AwayExplore the methodologies of DDoS attacks and their consequences.
-
WebinarsPen Testing Tool Kit: Tools for Cracking PasswordsShawn Evans shows how hackers prey on weak and default passwords as part of the Pen Testing Took Kit series.
-
WebinarsPen Testing Tools: Common Ethical Hacking ToolsAs part of our pen testing tool kit series, Shawn Evans reviews the common hacking tools he never hacks without.
-
White Papers & eBooksTop Cybersecurity Threats of 2017This report outlines five of the biggest cyber threats that NopSec expects to see in 2017.
-
WebinarsPen Testing Tool Kit: Tools and Techniques Used to Evade Antivirus SoftwareMichelangleo Sidagni discusses the top 5 tools used to evade antivirus software and how to stay protected if your antivirus is bypassed.
-
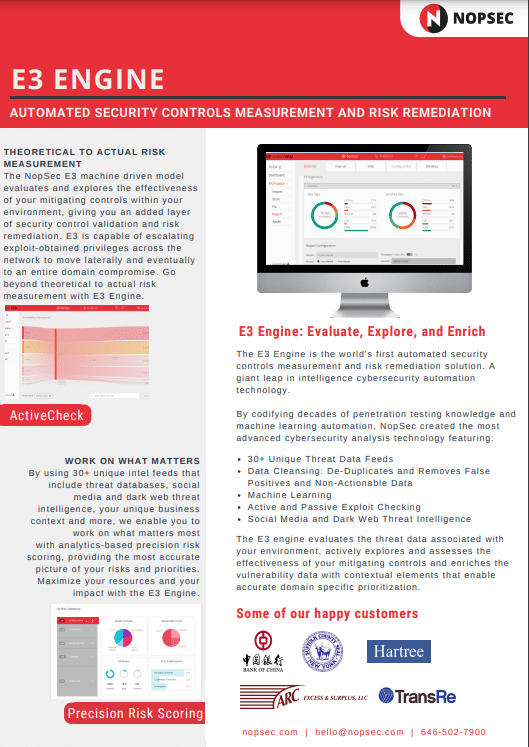
Data SheetsE3 EngineLearn how the E3 machine learning model evaluates your mitigating control's effectiveness within your environment.
-
White Papers & eBooksRemediation 101: How to Remediate VulnerabilitiesExamine common remediation pitfalls and solutions to simplify remediation to keep your business running smoothly and securely.
-
White Papers & eBooksSANS 20 Critical Security ControlsRead to understand SANS 20 Security Controls and how UVRM features map to respective controls.
-
White Papers & eBooksVulnerability Assessments: Best Practices GuideLearn the benefits of Vulnerability Assessments and steps to make your organization more secure.
-
White Papers & eBooksVulnerability Management: Best Practices GuideLearn the benefits of Vulnerability Management and steps to make your organization more secure.
-
White Papers & eBooksCybersecurity for Competitive AdvantageExamines how SaaS providers are using cybersecurity to radically differentiate their offering and transform their business.
-
White Papers & eBooksA New Approach to Security and Compliance for Healthcare: Cybersecurity Threats & ConcernsLearn how smaller healthcare organizations can systematically assess vulnerabilities.
-
Case StudiesEnergy Trading Company Case StudySee how NopSec provided solutions to help an energy trading company secure their global infrastructure.
-
Case StudiesInvestment Firm Case StudySee how NopSec provided solutions to meet the challenges of a leading investment firm.
What Industry Leaders Say About NopSec
Validated by Gartner Peer Insights