What is CVE-2021-22005?
CVE-2021-22005 is a vulnerability that allows an unauthenticated remote attacker to take over a server running VMWare vCenter Server. The vulnerability stems from a flaw in the Analytics service due to a lack of sufficient data validation. Successful exploitation would enable an attacker to craft a call to the Analytics service that resulted in attacker-defined content being output to arbitrary locations on disk.
NopSec reviewed the workaround script published by VMWare and found that PoC code was embedded as a cURL command:
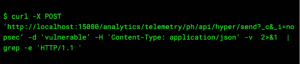
The above cURL command will create the file “nopsec.json” on the remote file system with the contents “vulnerable” as the user “root”. The “_i” parameter of the above request is prone to path traversal attacks, enabling a threat actor to write to arbitrary locations on disk with root/system level privileges, which could result in remote command execution.
How bad is this?
Severity: Critical
- Exploitation does not require authenticated access.
- Active exploitation today with PoC code publicly available.
Who is affected by this?
- Affects most versions of vCenter 6.7 and 7.0.
- vCenter 7.0U2c build 18356314 and 6.7U3o build 18485166 are not vulnerable
How are they exploited?
An unauthenticated, remote attacker could exploit this vulnerability with an unsophisticated exploit harness.
How do I protect myself?
NopSec recommends that customers patch the vulnerable VMWare vCenter deployment or apply the workaround provided by VMWare.




