In January 2022, The World Economic Forum published its initial “Global Cybersecurity Outlook” report, which identified a deep and growing perception gap between business and cyber leaders on the cyber resilience posture in worldwide organizations.
The report identified a need for establishing frameworks and tools to equip cyber and business leaders to understand and communicate prevailing cyber risks and their impact on organizations.
The “Cyber Resilience Index” (CRI) – developed in collaboration with the community of the Centre for Cybersecurity and authored by Accenture – aims to be a reference framework to provide visibility on cyber resilience practices across various industries.
The CRI aims to provide public and private-sector cyber leaders with a common framework for best practices for true cyber resilience and a clear language to communicate value.
We can define “cyber resilience” as the ability of an organization to transcend any stresses, failures, hazards, and threats to its cyber resources within the organization and its ecosystem, such that the organization can confidently pursue its mission, enable its culture, and maintain its desired way of operating. Fundamentally, cyber resilience must be an integral part not only to technical systems – but also teams, the organizational culture, and daily way of working.
The four primary reasons cyber resilience is limited in organizations today are that many of them:
- Have a narrow perspective of cyber resilience, focused mainly on security response and recovery;
- Lack a common understanding as to what a complete cyber resilience capability should include;
- Find it challenging to accurately measure organizational cyber resilience performance or communicate its true value to business leadership;
- Struggle to be transparent within their organization and with their ecosystem partners about shortcomings in their cyber resilience posture and their experiences with disruptive events.
The CRI seeks to address these limitations.
The World Economic Forum defines two components of an organization’s cyber resilience:
- The Cyber Resilience Framework (CRF)
- The Cyber Resilience Index (CRI)
The CRF is a guide to best practices for building holistic cyber resilience in an organization.
It consists of six key principles, associated practices, and their sub-practices with which cyber leaders can clearly define healthy organizational cyber resilience. It serves as a standard, industry-agnostic framework with defined outcomes that can serve as a baseline to all organizations.
Subsequently, the CRI is a tool to help organizations quantitatively measure their cyber resilience using measures of performance against best practices as laid out in the CRF. The CRI provides insights on organizational cyber resilience maturity to participating organizations.
Together, the CRF and CRI deliver a unique cyber resilience blueprint to improve transparency and visibility and enable global trust across digital ecosystems and diverse industries.
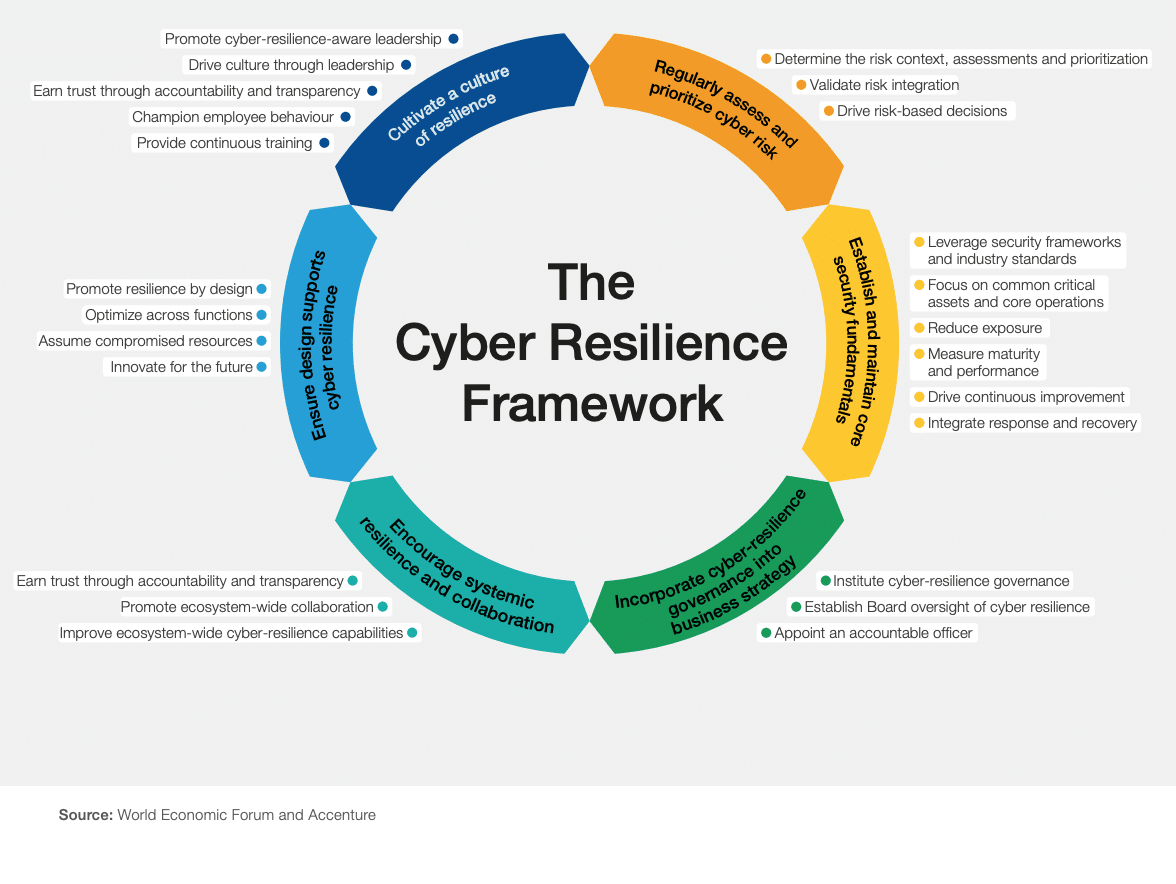
Source: the World Economic Forum and Accenture
Cyber Resilience Framework and Its Principles
As detailed in the chart above, each of the CRF principles is accompanied by a set of practices and sub-practices to further enable cyber leaders to develop and assess their cyber resilience. The following paragraphs describe the principles, practices, and sub-practices that compose the Cyber Resilience Framework.
Principle One of the Cyber Resilience Framework: Regularly Assess and Prioritize Cyber Risk
This principle states that all cybersecurity activities should be linked and informed by cyber risk assessment considerations, whether they be attack surface management, vulnerability management, threat management, identity, and access control management, etc.
Principle One Practices
Practice 1.1: Determine the risk context, assessments, and prioritization.
This practice requires an organization to maintain a map of major ecosystem and supply chain interdependencies. This, in turn, includes an attack surface management exercise. A sub-practice of this is for the organization to report externally on the state of its cyber resilience analysis on at least an annual basis.
With the SEC adding cybersecurity requirements for consideration, including a requirement for companies to report significant cyber incidents within 72 hours of uncovered significance, following this practice places your cybersecurity team in a better position to answer to a board or executive leadership.
Furthermore, one of the most significant aspects for a vulnerability management program is the attack surface and asset inventory management that empowers the “defenders” to know their asset surface at stake prior to putting into action security controls to protect it.
Practice 1.2: Validate risk integration.
The organization conducts a quantifiable assessment of its risk including cyber exposure versus risk tolerance on an annual basis. The organization then feeds the cyber risk assessment into its budgeting and compliance processes.
Budgets are tightening with the potential recession, and companies will need to justify their cybersecurity spend and decide which risks are accepted or can be otherwise mitigated. Adding to the tool stack isn’t necessarily the answer to emerging risks – this practice ensures the tools, people, and processes you have in place cover your attack surface.
Compliance requirements such as SOC2 and PCI all require that all security controls would be informed to sound risk management practices; risk management is a prerequisite practice in a sound cybersecurity program.
Practice 1.3: Drive risk-based decisions.
In this practice, the CRF recommends all employees have open reporting channels to escalate situations that are potentially high-risk. This enables leadership to make the most informed decisions regarding the company’s tolerance thresholds. In addition to these open communication channels, it’s recommended that management conduct after-action reviews on notable cyber resilience decisions from incidents, major breaches, or tabletop exercises to make corrections in order to improve decision-making.
Principle Two of the Cyber Resilience Framework: Establish and Maintain Core Security Fundamentals
The practices that are under the second principle of the Cyber Resilience Framework ensure that core functions and supporting systems are secure and tenable in the face of unexpected attacks. Organizations should follow all of these practices to maintain a strong cybersecurity posture.
Principle Two Practices
Practice 2.1: Leverage frameworks and industry standards.
A wise principle of security suggests not to create and manage policies and processes in a vacuum. All policies and procedures should meet the needs of security performance and compliance standards.
This practice states that companies should stay abreast of the most recent frameworks and measure themselves according to industry standards. To that end, an organization should annually measure its security and compliance posture, based on NIST, ISO 27001, HIPAA, NYDFS Cybersecurity regulations and standards, etc., based on which best fit their individual practice.
Practice 2.2: Focus on common critical assets and core operations.
You can’t secure what you can’t see – that’s why organizations should maintain an accurate standing inventory, preferably within their IT asset management and CMDB (ITSM) platforms, of all their assets and operations. Additionally, this asset inventory should contain the criticality of each piece, classified as “Common,” “Critical,” and/or “Core” to your cyber resilience according to defined criteria.
To this end, the cybersecurity team should always be able to identify what critical assets ensure business continuity. This value is based on the information value at risk and also on the reputational risk that the asset carries, should it be compromised.
Practice 2.3: Reduce exposure.
This practice has organizations committing to and applying principles such as least privilege, network segmentation, and footprint reduction to minimize unnecessary exposure to threats and hazards, which extends to architecture and configuration practices. This is again the practice of attack surface management (ASM). To do this effectively, organizations must have risk mitigation and compensating controls in place. To this end, it is important to factor in its threat modeling asset value, attack surface, vulnerabilities threat and exploits as well as contextual surface, including mitigating controls, network segmentation, security configuration, and identity and access management.
Practice 2.4: Measure maturity and performance.
Going hand-in-hand with the first practice of the CRF’s second principle, the fourth one ensures the organization has a way to report on its cybersecurity progress – or lack thereof. Organizations should define the security maturity and performance metrics for meeting their minimum security standards. Management should periodically report on these defined security metrics to ensure proper security performance monitoring.
This practice delivers the transparency into the organization’s cybersecurity posture that leadership needs and keeps your organization on track to improving its processes and procedures.
Practice 2.5: Drive continuous improvement.
There is no resting on your laurels in the cybersecurity domain. To stay ahead of cyber attacks and other threats, organizations need to formalize and execute action plans for practice and operations improvement based on gaps identified with the cyber resilience framework, which then fuels reporting based on performance against success criteria.
Simpler to say than to do, cybersecurity leaders need to ensure their programs continue to mature in a consistent and traceable manner.
Practice 2.6: Integrate response and recovery.
Response and recovery are crucial components of any cybersecurity program. Organizations should track performance progress for response and recovery actions through metrics. The review of these metrics should in turn trigger action plans. Responding swiftly and recovering safely from a security incident is an important part of an organization’s disaster recovery strategy and integrates directly into its resiliency, security maturity, and status.
Principle Three of the Cyber Resilience Framework: Incorporate Cyber Resilience Governance into Business Strategy
This principle aligns the cyber resilience strategy with the organization’s business goals for holistic integration from the top down.
Principle Three Practices
Practice 3.1: Cyber Resilience Governance Structure.
Leading this principle is the practice of establishing a cyber resilience governance structure, organization charts, operating model, and clearly defined roles as part of a cyber resilience operational structure and governance. To this end, the organization must also have a cohesive cyber resilience strategy.
Practice 3.2: Board of Directors responsibility on cyber resilience goals.
According to the CRF, the Board of Directors should be accountable for the organization’s cyber resilience strategy – including setting resilience risk tolerance levels. Furthermore, the Board of Directors should receive regular briefings on the state of the achievement of cyber resilience goals and strategy goals achievement.
Practice 3.3: CISO appointment.
This practice ensures the organization has established accountability for how cyber resilience efforts progress towards its goals. An accountable officer for cyber resilience management should be formally appointed within the organization. This officer is clearly empowered to implement the organization’s cyber resilience strategy, has a clear communication channel over the Board of Directors, and manages sufficient personnel, financial, and technology resources. This officer should likely be the organization’s CISO.
Principle Four of the Cyber Resilience Framework: Encourage Systemic Resilience and Collaboration
Following this principle demonstrates that the organization is aware of the interdependencies within its environment, how it engages and works with outside organizations, and fulfills its role in managing and maintaining ecosystem security resilience.
Principle Four Practices
Practice 4.1: Cyber resilience communication.
This practice focuses on transparency in earning and maintaining trust with your partner organizations through collaboration and sharing of best practices. The organization should communicate your cyber resilience practices to third parties through their designated resource. Additionally, participation in cyber resilience benchmarking activities and best practices sharing with ecosystem partners strengthens both your relationships and your cybersecurity posture. This activity falls under the third-party risk management practices.
Practice 4.2: Cyber resilience capabilities.
The overall practice’s aim is to improve ecosystem-wide cyber resilience capabilities. Within this practice, the organization works to continuously improve collective cyber resilience capabilities together with other members of the ecosystem (third-party business partners and supply-chain partners) to raise the overall standard of security practice. These capabilities appropriately balance innovation, preparedness, protection, response, and recovery capabilities.
Principle Five of the Cyber Resilience Framework: Ensure Design Supports Cyber Resilience
The design and execution of an organization’s cyber resilience strategy must remain agile and adaptable. To optimize resilience, these practices help your organization improve continuously in line with its ecosystem.
Principle Five Practices
Practice 5.1: Promote resilience by design.
Build systems and software with resilience and scalability in mind. To fulfill this practice, the organization must have clearly defined and documented principles and objectives for the resilient architecture of teams, processes, and technology assets – as well as ensure all of these follow the principle of least exposure to reduce attack surfaces. Existing teams, processes, technologies, and interrelated systems should be reviewed against resilience principles and objectives on an annual basis at a minimum.
Practice 5.2: Optimize across functions.
Don’t fall into the trap of operational silos. This practice recommends reviewing and optimizing security operations for managing cyber resilience across different organizational functions at least annually. Furthermore, organizations following this practice should run resilience scenarios and drills regularly with cross-departmental stakeholder participation to identify process improvement opportunities in the form of security tabletop exercises. This ensures coherence and collaboration across teams regarding your cybersecurity efforts and priorities.
Practice 5.3: Assume compromised resources.
With an average of twenty-two new security vulnerabilities identified each day and cyber attacks continuing to grow in sophistication and frequency, you have to be prepared for the eventuality of a successful breach.
By following this practice, you ensure the organization’s cyber resources are prepared to absorb adverse events as part of normal operations and continue to meet performance and quality requirements. In other words, the organization’s cyber resources should be tenable and resilient. Tracking metrics during disruptive events allows the organization to modify performance and operations to account for such events.
Practice 5.4: Innovate for the future.
Cyber attackers continue to adapt and evolve their approaches in scope, depth and sophistication, and so should the organization. To follow this practice, the organization needs to invest in resources for security research, development, and innovation focused on future resilience. This means these initiatives must be actively managed and budgeted for.
Principle Six of the Cyber Resilience Framework: Cultivate a Culture of Resilience
Your cyber resilience strategy doesn’t end with technology and processes. Social engineering attacks are more sophisticated than ever, and multiple research firms warn that phishing attacks in particular are getting better.
The sixth principle of the CRF addresses how to empower employees across your organization to understand and follow cyber resilient best practices, no matter their role.
Principle Six Practices
Practice 6.1: Promote cyber resilience-aware leadership.
Cyber resilience must start at the top. The organization’s leadership should have performance goals related to cyber resilience as well as include leaders with expertise and training in cyber resilience. The CRF recommends the organization incentivizes its leadership to advance their expertise within the cyber resilience space.
Practice 6.2: Drive culture through leadership.
A cyber resilience-first culture trickles down from the top. Leadership needs to clearly demonstrate the cyber resilience focus to the employees at all levels through their words and personal actions. As part of this, every employee should be measured on cyber resilient behavior, reinforced through regular training with well-documented rewards criteria and corrective measures as necessary.
Practice 6.3: Earn trust through accountability and transparency.
Similar to the first practice under the fourth principle, “Encourage Systemic Resilience and Collaboration: Cyber resilience communication,” the organization should practice accountability and transparency internally. This means the organization should measure and track metrics for assessing the cyber resilience-first culture it is creating and have a communication plan for how the achievement of your cyber resilience goals is shared regularly across the organization.
Practice 6.4: Champion employee behavior.
Under this practice, it is important to give the organization’s employees a sense of ownership for the organization’s cyber resilience with access to cyber resilience training that empowers the employees to identify and communicate threats. Supportive behaviors should be included in the employees’ performance goals. To strengthen this, ensure that the employees feel empowered to practice cyber resilient behaviors in their day-to-day work without fear of reprisal.
Practice 6.5: Provide continuous training.
Many of the practices outlined in the CRF are continuous, especially this practice. Organizations dedicated to a culture of cyber resilience must provide continuous training and/or tabletop exercises to employees to enable them to identify and report threats. Like any good training, these should enable employees to actively engage throughout the exercises.
Building Towards Better Cyber Resilience with the CRF and CRI
Compliance to the principles and practices of the Cyber Resilience Framework is measured by the Cyber Resilience Index. The main goal of the CRI is to provide cyber leaders with a tool and the visibility to understand their organization’s and their ecosystem’s cyber resilience level. In doing so, leaders and executives will learn where their organization needs to improve to reach the next level of resilience.
Consider the picture below depicting a fully expanded Cyber Resilience Framework with its Principles and Practices.
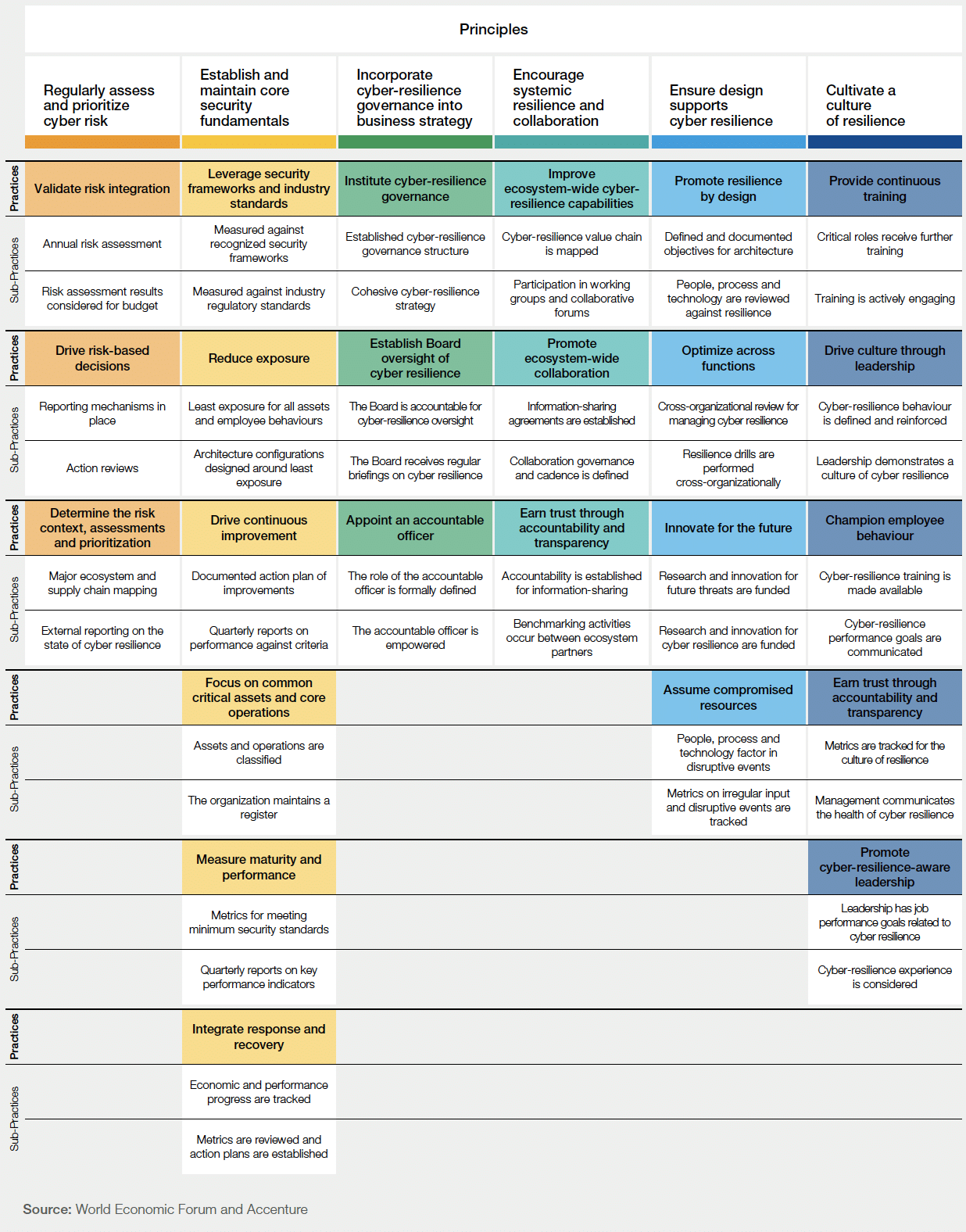
Source: World Economic Forum and Accenture
As you can see, throughout the framework and specifically the principles “Regularly assess and prioritize cyber risk,” “Establish and maintain core security fundamentals,” and “Ensure design supports cyber resilience,” the concept of vulnerability risk prioritization, risk acceptance, attack surface management, and reduction, exposure management and reduction, asset criticality and value management, attack surface maturity, and the concept of cyber exposure/resilience tabletop tests are key and central to the Cyber Resilience Framework. All these practices in turn are part of a strong organizational attack surface, threat, and vulnerability management.
NopSec Unified VRM, with its focus on vulnerability prioritization, attack surface risk management, and asset management, provides an easy-to-deploy vulnerability risk management framework through a SaaS Service that can be used to implement Principles and Practices included within the World Economic Focus Cyber Resilience Framework and Index.




