Auditor is an IT auditing software used to track assets within an organization. The product’s official website is https://www.netwrix.com/auditor.html. The latest version of the application is 10.5, released on June 6, 2022.
Remote code execution vulnerabilities exist in the Netwrix Auditor User Activity Video Recording component affecting both the Netwrix Auditor server and agents installed on monitored systems. The remote code execution vulnerabilities exist within the underlying protocol used by the component. It can potentially allow an unauthenticated remote attacker to execute arbitrary code as the NT AUTHORITY\SYSTEM user on affected systems, including on systems Netwrix Auditor monitors.
What is CVE-2022-31199?
The Netwrix Auditor application is affected by an insecure object deserialization issue that allows an attacker to execute arbitrary code with the privileges of the affected service. This issue is caused by an unsecured .NET remoting port accessible on TCP port 9004.
How bad is this?
While this CVE came out in 2022, CISA just included it in their Known Exploited Vulnerabilities Catalog. This escalation of priority by CISA has triggered our re-evaluation of this vulnerability and lead us to subsequently publish this security bulletin.
Reference CISA’s BOD 22-01 and Known Exploited Vulnerabilities Catalog for further guidance and requirements.
| CVE | CVSS | CVSSv3 |
| CVE-2022-31199 | No CVSS score published yet | 9.8 |
Severity: Critical
How is it exploited?
A serialized object is sent to TCP 9004 listening service. The object is deserialized in an insecure way and the related payload is executed in the underlying Windows OS.
Since the command was executed with NT AUTHORITY\ system privileges, exploiting this issue would allow an attacker to fully compromise the Netwrix server. Newer versions of Truebot malware allow malicious actors to gain initial access by exploiting a known vulnerability with the Netwrix Auditor application (CVE-2022-31199). As recently as May 2023, cyber threat actors used this common vulnerability and exposure to deliver new Truebot malware variants and to collect and exfiltrate information against organizations in the U.S. and Canada.
How do I protect myself?
Update to version 10.5
| Affected Version |
| All supported versions prior to 10.5 |
NopSec’s Thoughts
The Netwrix Auditor application is affected by an insecure object deserialization issue that allows an attacker to execute arbitrary code with the privileges of the affected service. In a typical real-world scenario, Netwrix Auditor services would be running with a highly privileged account, which could lead to full compromise of the Active Directory environment.
This issue was discovered by performing a TCP port scan of a Netwrix Auditor server using the tool nmap. As the following output demonstrates, the Netwrix server had a .NET remoting service available on TCP port 9004:
FIGURE 1 -Scanning for services on Netwrix server
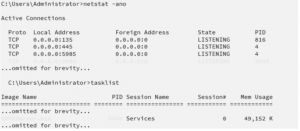
The netstat and tasklist commands were used on the Netwrix server to find out which process was exposing the .NET remoting service:
FIGURE 2 – Identifying the .NET remoting service
Analyzing the .NET remoting service revealed that it could be accessed with the UAVRServer endpoint. The ysoserial.net tool was used to generate a serialized object designed to execute the command whoami on the server under the context of UAVRServer.exe:
FIGURE 3 – Generating a serialized object
The ExploitRemotingService tool was then used to send the serialized object to the UAVRServer service over .NET remoting. The resulting exception was an indicator that the payload was executed successfully:
FIGURE 4 – Sending the malicious object to the UAVRServer service
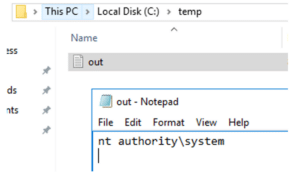
Logging onto the server and inspecting the contents of C:\temp\out.txt showed that the command was executed successfully:
FIGURE 5 – Code executed through the .NET remoting service
Since the command was executed with NT AUTHORITY\ system privileges, exploiting this issue would allow an attacker to fully compromise the Netwrix server.