Time is Money Part 6: Calculating ROI of Vulnerability Management Program
- Mar 06, 2019
- Guest Author
This is the final post in this six-part series. You can find the previous posts below.
Time is Money, Part 1: Vulnerability Management Maturity Levels
Time is Money, Part 2: Vulnerability Analysis
Time is Money, Part 3: Vulnerability Assignment
Time is Money, Part 4: Fixing Vulnerabilities
Time is Money, Part 5: Validating the Fix
The whole series comes together in this final post, where we explore how we can actually save time and therefore, money through prioritization and automation. While most enterprises typically don’t think of employee time as an expense, it can help to adopt a consulting firm’s perspective in analyzing time saved. This can easily be calculated by taking an employee’s salary and dividing it by 2000 hours to get an ‘hourly rate’. For example, an analyst earning $100,000 per year would be earning $50/hr.
This rate gives us a rough idea of what each employee’s time is worth to the organization and allows us to put together somewhat realistic returns-on-investment (ROI) figures.
In part 1 of this series, we defined some maturity levels for vulnerability management programs. Those that make it to level 3 will see significant time savings, but really, the difference between levels 1, 2 and 3 is whether or not vulnerabilities are addressed at all. The real time savings occur on the path from maturity level 3 (mandated) to level 4 (defined, managed, efficient).
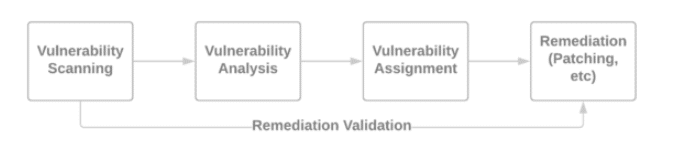
Parts 2, 3, 4 and 5 of this series covered this journey, to this final, ideal level of maturity where all that remains are smaller, iterative, more nuanced refinements in process. Each of these parts detailed the importance of each step in the vulnerability management process (diagram below). Each part also detailed the challenges presented in each stage and opportunities for streamlining and saving time. What about quantifying the time and money saved? What’s the actual ROI?

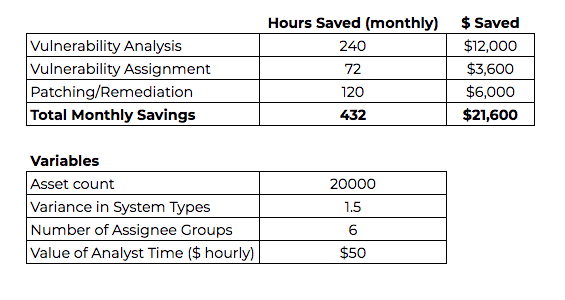
In the vulnerability analysis stage, a vast number of opportunities exist to reduce time and effort. Eliminating false positives. Deduplicating, prioritizing and summarizing vulnerabilities. Enriching vulnerability details and providing quick links for additional research. Providing actionable advice. Performing all this work manually can easily create 8 hours of analysis work per 1000 assets per month. There are many factors that determine the effort – for example, more homogeneous networks have more similarly-configured systems, which would reduce this 8-hour estimate. More heterogeneous networks would increase the estimate.
This level of complexity will similarly affect each following stage – a 1.5 modifier for complex, 1.0 for normal and 0.5 for simple. More types of systems and/or versions of software potentially result in additional patching processes and additional confusion around who to assign issues to.
(asset count / 1000) * 8hrs * complexity modifier * $50/hr = ROI
In the vulnerability assignment stage, analyzed data is typically exported (spreadsheets are the most popular format) and then shared (email is most common). This task is rarely assign-and-forget and involves varying levels of pestering to reach the next stage. Let’s assume 8 hours per month, per assignee.
assignee group count * 8hrs * $50/hr = ROI
In the patching stage, an additional layer of research and analysis may be necessary to determine if a vulnerability is truly applicable to the environment in question and/or which specific patch will address the issues in question. A ‘patch everything’ policy avoids these sort of issues, but in larger environments, especially those with fragile or mission-critical systems, applying unnecessary patches can often be considered an unnecessary risk. In these environments, it’s worth determining which patches are absolutely necessary and which aren’t.
Time savings are possible here, but more challenging in organizations with complex change management approval policies, restrictive/fragile systems or a requirement to first release updates to test groups before releasing to the entire organization. Still, savings in research, analysis, obtaining the patch (i.e. downloading it) and creating deployment packages can result in 4 hours of time savings per month, per 1000 assets.
(asset count / 1000) * 4hrs * complexity modifier * $50/hr = ROI
Thank you for reading through this series – we hope it has been enlightening and will remain a useful reference for our readers.