Security Insights Feature Release: See Hidden Security Trends with Exception Insights
- Apr 18, 2024
- Rob Johnson

You diligently identify vulnerabilities, but fixing them all within tight deadlines isn’t always feasible. That’s where Exception Plans come in – documented decisions to delay patching specific vulnerabilities. However, these plans often sit in isolation, offering limited insight into the bigger security picture.
It goes beyond simply managing exceptions – it leverages cutting-edge data science to unlock a treasure trove of hidden intelligence buried within your Exception Plans.
Imagine this scenario: You’re a Security Analyst bombarded with daily vulnerability reports. You meticulously analyze each one, prioritizing based on severity and exploitability. But deadlines loom. Patching every vulnerability within the designated Service Level Agreement (SLA) window can be a logistical nightmare.
Here’s where Exception Plans come in. They allow you to document a conscious decision to delay patching a specific vulnerability, outlining the rationale behind the delay. This could be due to:
Exception Plans provide valuable context for individual vulnerabilities. However, the traditional approach has limitations:
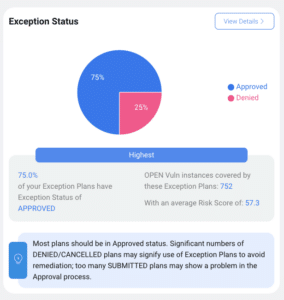
Exception Insights shatters these limitations. It transforms Exception Plans from isolated decisions into a rich source of security intelligence. Here’s how:
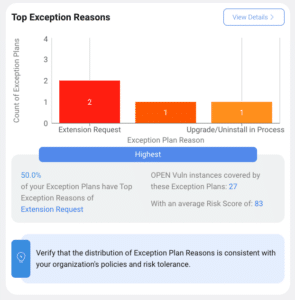
Let’s revisit the earlier scenario. With Exception Insights, you can now analyze all your Exception Plans and see the bigger picture. Perhaps you discover a surge of exceptions for unsupported operating systems. This could be a red flag – are you leaving yourself exposed because critical patches aren’t available for these outdated systems?
Exception Insights doesn’t just highlight the trend – it empowers you to take action. You can use this insight to:
This is just one example. Exception Insights can uncover a wide range of trends, each offering valuable insights to inform your security strategy. Imagine being able to identify:
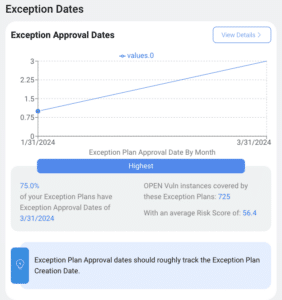
The traditional approach to vulnerability management can be time-consuming and resource-intensive. Security analysts are often forced to make difficult decisions about which vulnerabilities to patch first, with limited data to guide their choices.
Exception Insights empowers security professionals to move beyond simply reacting to individual vulnerabilities. It allows them to identify systemic security weaknesses and develop strategies to address them before they can be exploited by attackers.
Exception Insights is more than just a new feature – it’s a paradigm shift in how you manage your security posture. It empowers you to move beyond reactive vulnerability management and into a proactive approach.
Ready to level-up your security insights and make a real impact on your risk? Join our monthly recurring platform walkthrough to see this feature in action and get your questions answered! Don’t wait, the threat actors aren’t. Register for the webinar here!