Detecting the GHOST glibc Vulnerability with Unified VRM
- Jan 29, 2015
- Michelangelo Sidagni
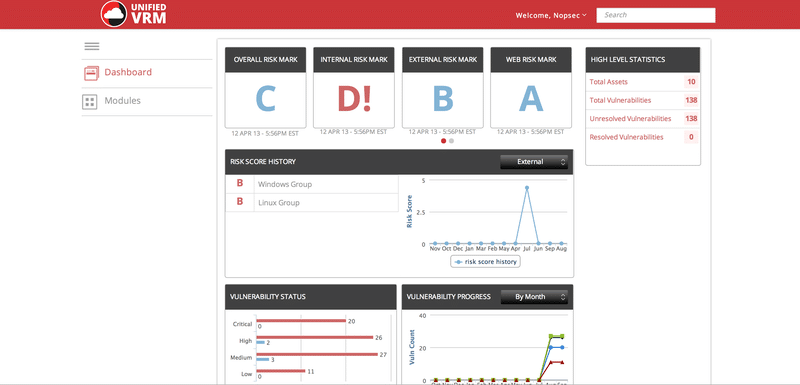
In the previous blog post here, we described the GHOST Linux glibc vulnerability in details and its repercussions to the affected systems in terms of risk.
NopSec Unified VRM helps identify the Linux GHOST glibc vulnerabilities in various flavors of Linux, performing authenticated scans. Furthermore, Linux authenticated scan can be performed using SSH through username / password and certificate as well.
The following Linux platforms have now vulnerability checks for detecting the Linux GHOST vulnerability:
All vulnerable flavors of Ubuntu;
CentOS 5,6, and 7;
RHEL;
Debian.
To better detect the vulnerability, create a custom scan template, enable SYN Scan for all the privileges TCP ports, enable SSH authenticated check and enter credentials or certificate. Then search for only the CVE-2015-0235 vulnerabilities checks. Enable silent dependencies and all other checks will be automatically selected.
Save the scan template and then use it in an authenticated scan against a range of internal IP addresses.
Happy GHOST hunting!!