Customized Threat Intelligence Engine
- Mar 01, 2017
- Guest Author
Unified VRM Analytics leverages vulnerability data from across all the modules (Internal, External and Web) the user has subscribed to and correlates that vulnerability information with external and internal threat feeds to provide the user actionable security intelligence. This enables the user to proactively protect them and take action against threats and vulnerabilities before potential severe business impact. Using our analytics the user can close the window of exposure and significantly lower risk by applying remediating controls to vulnerabilities rated by severity in context of the user’s business asset classification.

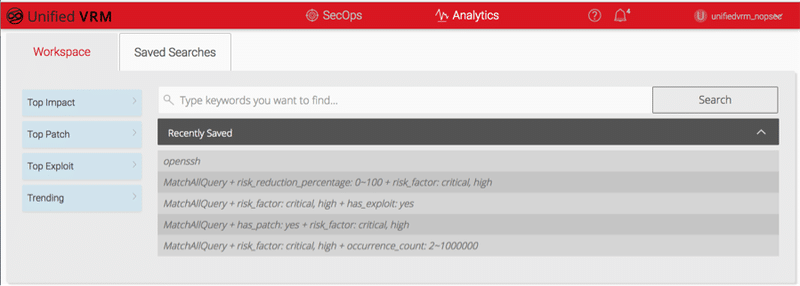
The Analytics engine powered by Elasticsearch can comb through throve of unstructured vulnerability, exploit, malware, patch, asset and ticket data to present the user with filterable lists of vulnerabilities present in their environment based on the search criteria. These lists can be filtered down even further based on several filters provided and the final search can be saved. From this saved search a report can be generated providing the user with more customizability from using UnifiedVRM.
Each vulnerability in Analytics can be viewed in Remediation of the corresponding module tickets have been opened in. For example:
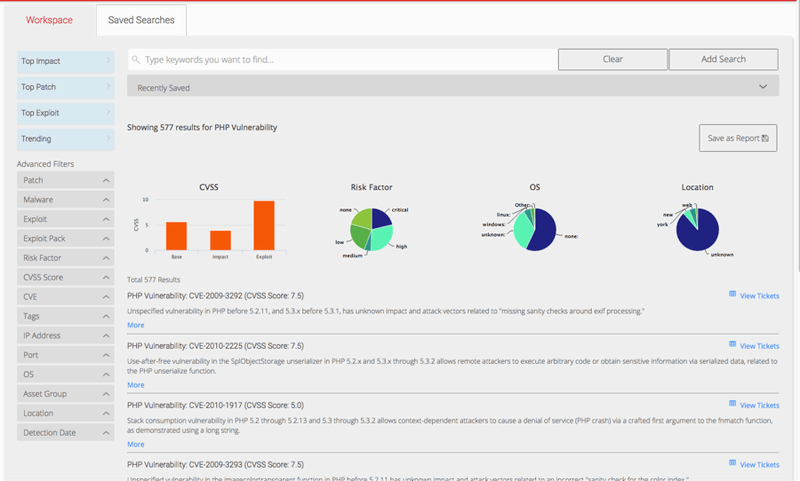
The user can click View Tickets against an entry to go to Fix page for that specific vulnerability and a list of tickets related to that vulnerability will be displayed.
The main advantage of using UnifiedVRM is to give the user a holistic view of vulnerability data and take action based on how those vulnerabilities impact their business the most. Using Unified VRM’s advanced filters the user can prioritize remediation based on the factors below and many more.
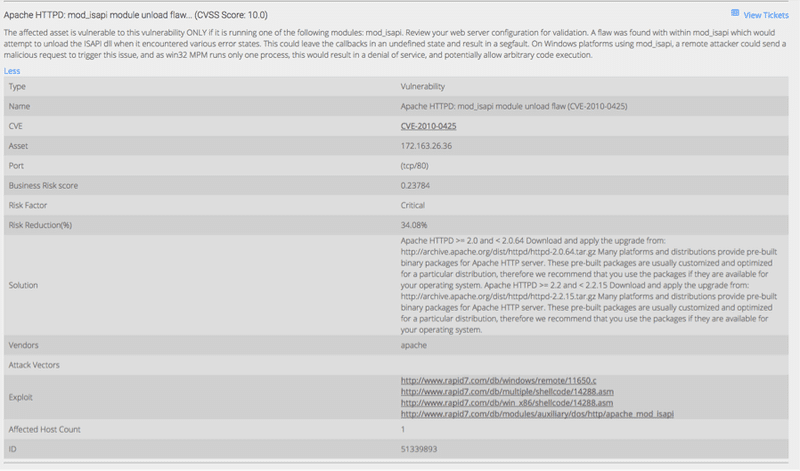
This will list vulnerabilities according to the selection criteria as seen in the figure above. Apart from viewing the corresponding ticket(s) in the Fix page, the user can also glean more details about the vulnerability by clicking the More link. The user can also click the title of the vulnerability to view more specific details about the asset if affects, the port on which it affect the asset, its risk factor, the risk reduction percentage, threat references. Detail also include the number of hosts affected by this vulnerability and most importantly, solution steps if applicable.
Each saved search will be able to generate reports (HTML, PDF format)
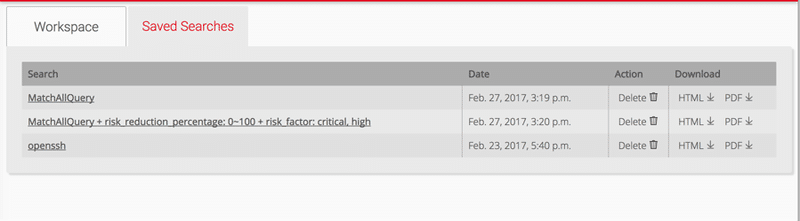
Following picture is an example of analytic report.
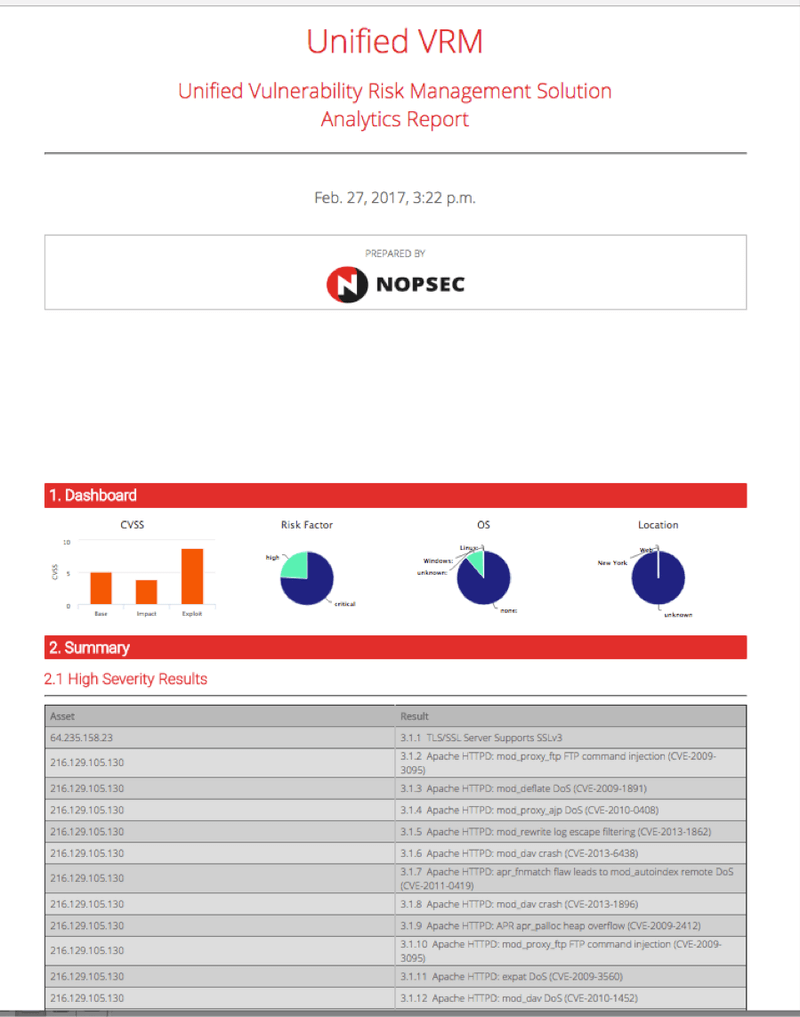
For more information on UnifiedVRM Analytics, contact us for free demo.