Say Hello to WappSnap
- Aug 05, 2025
- Shawn Evans
From time to time we find ourselves in a situation where the tools we rely on fail to serve our needs. This may be a deficiency of the tool itself or environmental circumstances that limit your ability to install dependencies. In these situations one of your most utilitarian options is to get your hands dirty and start coding.
I recently found myself in this exact situation. For years I relied on the web page screen shot utility Peeping Tom. Peeping Tom was great, but it was coded in Python 2.7 and relied on the external tools cURL and PhantomJS. cURL is on every Linux distro, so that dependency is easy to check off. However, PhantomJS has long been abandoned and not readily available out of the box on many (any?) distros, even Kali. Compounding my issues, I was unable to install dependencies due to some aggressive egress filtering rules. So what do you do?
You create a new tool, of course! I’m happy to introduce WappSnap, a handy web application screen shot utility. WappSnap shifts away from PhantomJS by embracing Selenium. Yes, Selenium is still a dependency, however Selenium is supported by a robust community of dedicated developers, making it a better foundation to build upon.
WappSnap allows you to grab a PNG screen shot of a single URL, a group of URLs in a text file, or import HTTP servers from Nmap XML results. The integration with Nmap makes this a great way to quickly visualize the composition of the network without relying on server banners.
Installing WappSnap is pretty straightforward. Simply clone the repo from GitHub and install the dependencies in the requirements.txt file.
$ git clone https://github.com/ShawnDEvans/wappsnap
$ cd wappsnap
$ python3 -m pip install -r requirements.txt
$ ./wappsnap.py -h
If you’re familiar with Peeping Tom (high five!), then you’re already familiar with the syntax for WappSnap. For everyone else, it’s easy!
At its most basic level, all you need to do is feed it a URL (-u).
$ ./wappsnap.py -u https://www.nopsec.com
[*] Analyzing 1 targets.
[*] Storing data in ‘250804_103910_6705/’
[*] Starting a capture with 1 processes to complete 1 tasks.
[========================================] 100%
[*] Finished 1 of 1 with 0 errors in 6.00s
[*] Done.
This results in the creation of three files: a screen shot of the web page, the HTML source of the page, and an HTML report for easy viewing. The HTML report also contains HTTP response headers, making it suitable for basic grepping.

When combined with Nmap (-x) this simple utility becomes a much more powerful asset. Visualizing the HTTP attack surface and reducing the need to visit each page manually drastically reduces testing time, which is critical on a time-boxed engagement.
I have relied on Peeping Tom for quite a long while. It’s been a component of my testing methodology on nearly every assessment for many years. Fast forward to the present and I have accumulated thousands of screen shots of countless web applications. These screen-shots weren’t really serving any purpose. They collected digital dust. So we decided to grant them a second lease on life.
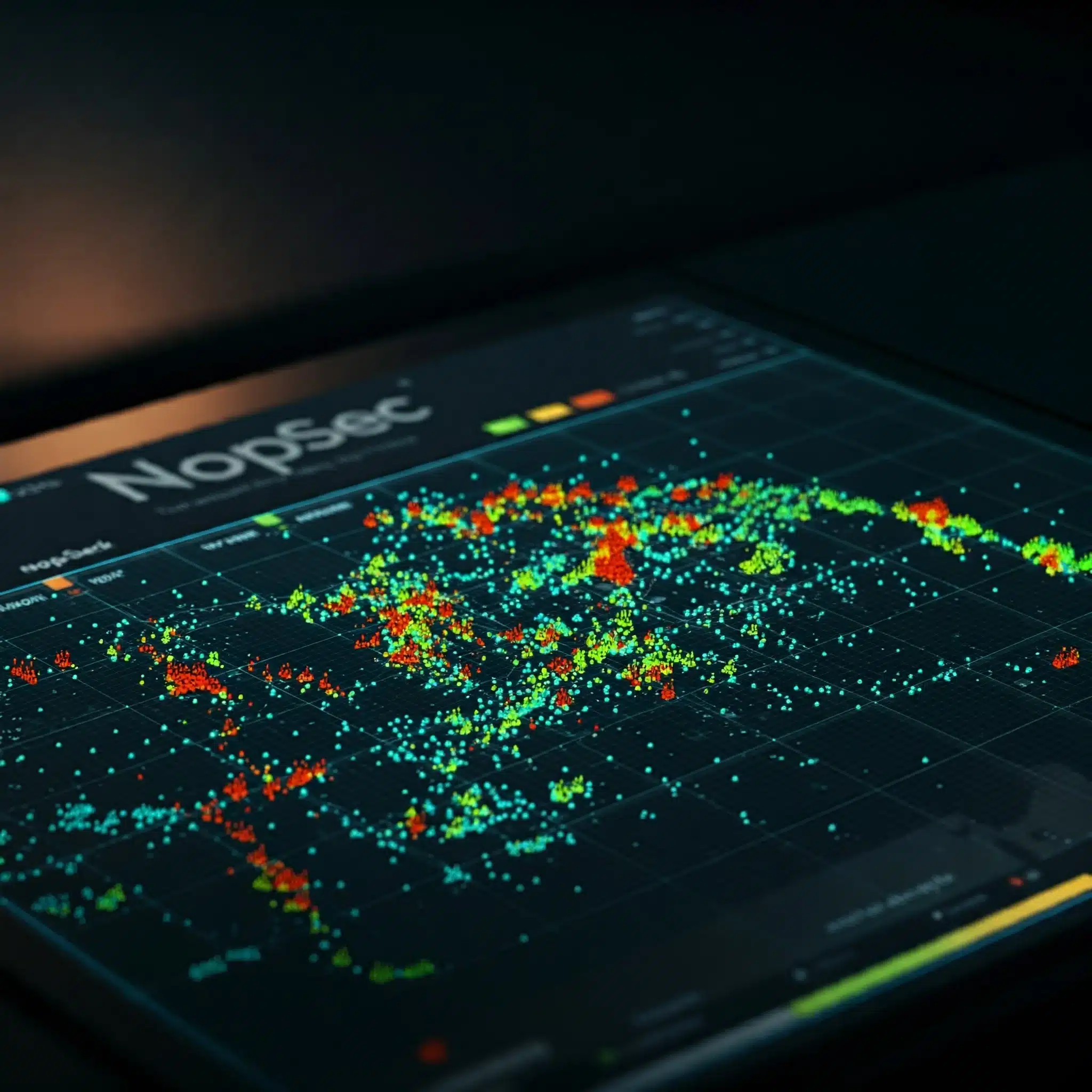
I sat down and began tirelessly indexing all of the screen shots we accumulated as accurately as possible to enrich them with meta-data. Thousands of screen shots were categorized, their versions identified, and a meta-data database was created. This database provided the backbone to introduce large language models (LLM) into our testing methods.
We use open source LLMs to vectorize our screen shots and meta-data database into embeddings. These embeddings can then be used as a means to calculate the cosine similarity of any URL we want. It basically takes the human analyst out of the loop. This test harness allows us to not only visualize the attack surface, but simultaneously categorize it, down to the version/build level.
Using our proprietary solution we can now identify, with a shocking degree of accuracy, the exact version of a webpage. Neat! Lets say you encountered a huge density of Cisco IP phone configuration portals, but you’re only interested in the older instances. By combining WappSnap with the power of an LLM we can quickly isolate vulnerable resources such as Cisco IP phones, prone to known exploitable vulnerabilities, with no vuln scan required. What would have required a significant investment in forensic analysis can now be carved through in minutes instead of hours. This results in fewer packets and a packet saved is a penny earned or something like that.
We’re working on publishing an open source version of WappSnap packaged up with AutoCat, but it’s not quite ready for prime time. As soon as we have something to share, we’ll be sure to let you know! NopSec is committed to the infosec community and sharing innovative solutions with our clients, colleagues, and like minded infosec explorers. Be sure to check back soon!