EXECUTIVE OVERVIEW
We live in a world where, on average, twenty-two new security vulnerabilities are identified each day. This rapid increase in vulnerabilities puts pressure on SecOps teams, keeps CISOs and CIOs up at night, and, if left unchecked, will likely result in damage, downtime, or disaster.
NopSec, a market leader in cyber vulnerability assessment and management, has a strong track record of bringing compelling advantages to high-growth companies across healthcare, finance, media, and manufacturing. Unified VRM helps Vulnerability Managers by illuminating the most critical risks to accelerate decision making and furthermore aids CISOs by giving them a tool that helps optimize the progress of their teams and demonstrates the ROI of security investments.
NopSec commissioned HighTide Advisors to perform a complete bottomline outcome assessment from the result of implementing Unified VRM for cyber exposure management. HighTide Advisors conducted an extensive review of Unified VRM, and this study offers a deep view of how Unified VRM addresses substantial challenges and delivers compelling ROI. After reading this paper, security professionals, from CISO to administrator, will have a deep understanding of the features, functionality, and financial value of Unified VRM.
TODAY’S CHALLENGES
Every organization is under pressure to deliver leading-edge services, solutions and experiences that are the foundation of business advantages, but come with the downsides of increased vulnerability and risk. In 2021, security challenges are emerging at an unprecedented rate; it’s almost impossible to keep up, and vulnerability management teams, in particular, are stretched thin.
Attack surface proliferation: Ask any CISO, and they’ll tell you that attack surfaces are increasing with every augmentation and expansion of IT infrastructure. Every application is internet-facing, spans multiple platforms and operating systems, extends from on-premise infrastructure into multiple public clouds and sometimes edge infrastructure. Every infrastructure element that processes, stores, and/or transfers data can hypothetically be breached or compromised. And every infrastructure has obscure vulnerabilities, due to our dependencies on third and fourth parties, that we’re exposed to through integrations. Vulnerability management teams need better ways to address the ever-growing, ever-evolving scale and scope of attack surfaces.
Vulnerability and threat proliferation: In case you haven’t noticed, vulnerabilities are discovered every day, threats emerge every hour, and most sources of threat intelligence and vulnerability discovery are limited. Organizations that rely on a single source or a few sources are likely to miss out on vulnerabilities and risks.
Data explosion: Our data sets are also growing each day in volume, number, and location — offering bad actors more targets and allowing them to access more records with each compromised system. Tools and processes that worked well in the terabyte world simply cannot keep up when organizations are dealing with petabytes or even exabytes scattered over many locations. Being able to localize and protect data, regardless of platform or size, is increasingly critical.
Criminal sophistication: Whether it’s traditional malware, ransomware, cryptojacking, or traditional data breaches, criminals are becoming more sophisticated, expanding and accelerating their efforts. Every legitimate organization is an attractive hunting ground for criminals, terrorists, and activists, and the technical capabilities of many criminal organizations equal those of enterprises and governments. Building security capabilities with leading-edge tools is a key component of keeping up with criminal enterprises that are able to rapidly diversify their threats and actions, build new capabilities with global talent pools, and are strongly financially motivated to escalate and extend attacks.
Shortage of experts: Unlike most criminal organizations, few enterprises have access to a global talent pool. According to a recent survey, businesses around the world lack skilled cybersecurity professionals. This survey indicates that, in 2020, there were about three million unfilled security roles, and 56% of organizations said that their efforts were substantially impacted by personnel shortages. If you look around an average SecOps team, there’s an empty chair or two that hasn’t been filled for months.
Tool proliferation: Finally, tool sprawl has become an operational complexity that many organizations simply don’t know how to solve. The ideal in any organization is a single source of information, but many organizations have tools that were once sufficient but are now lacking. Tools that provide on-premise information might not extend to the cloud, tools that cover the conventional enterprise might not extend to IoT devices at the edge, some tools for some threats and not others, and so on. And tool sprawl impacts so many aspects of managing security — it reduces visibility, opens gaps, complicates workflows, impedes prioritization, and simply makes the job harder than it should be.
Too much noise: organizations with dozens of tools have thousands of alerts. Many teams have too many alerts to deal with, no good way to rank alerts, and an endless problem of alerts for non-critical issues that come up at inappropriate times, like 2am. Cutting thousands of alerts into a manageable, prioritized collection is nearly impossible with manual intervention because there’s no way to keep up.
All these problems have synergistic effects that are disrupting today’s organizations. Today’s average security team is trying to cope with too many attack surfaces, too many data sets, too many threats, too many alerts from too many tools — but simply don’t have enough people to do the job.
Vulnerability management teams are under unprecedented pressure. Can NopSec help?
THE NOPSEC DIFFERENCE
The security experts behind Unified VRM examined these challenges and devised a single tool to help manage vulnerabilities and mitigate risks. Unified VRM delivers a singular advantage over other tools — it helps cyber defenders identify and prioritize threats using machine learning.
At the highest level, the tool gives SecOps and CISOs a view of total assets, what percentage and number of assets are vulnerable, the number of total vulnerabilities, and the percentage and number of urgent vulnerabilities.
Prioritization of urgent vulnerabilities is the key here. Risk ranking is one of the most important elements for understanding Unified VRM, giving teams a way to go beyond threat discovery to understanding which vulnerability should be addressed first.
- The tool begins with 30+ threat intelligence feeds providing data into a supervised machine learning algorithm, spanning everything from CVE to IP reputation and social media feeds.
- Then the tool helps assess the impact of vulnerabilities on an environment. Does the vulnerability impact one container or all containers? One operating system or cross-platform?
- Then it examines the existence and effectiveness of environmental controls. Do you have network segmentation or encryption? Is antivirus software up to date?
These inputs are combined to deliver a vulnerability risk score for all vulnerabilities, ranking from highest to lowest impact, with recommendations for mitigating the vulnerabilities. These recommendations are also included in overall remediation recommendations for common attack scenarios, like ransomware or preventing attackers’ lateral movement. The tool also flags “celebrity vulnerabilities,” including a recently published issue with a particular firewall or email server.
The tool also helps you build on and connect with existing tools for a clearer, more impactful set of vulnerability recommendations. Support for many integrations, including, but not limited to:
- Active Directory or CrowdStrike for asset discovery
- A wide range of scanners (including web application, cloud, and containers)
- Extra sources for threat intelligence, including penetration test findings
- Remediation and orchestration tools like Splunk Phantom
- Collaboration, including Slack and Microsoft Teams
- Bugcrowd or CrowdStrike Overwatch for validation
- Endpoint protection like Microsoft Defender ATP
- Analytics with RSA Archer, Power BI, and Tableau for reporting
- Tag Management — supports tag importing and web application tag management
In short, Unified VRM is a comprehensive vulnerability management tool that has the features, functionality, integrations, and mature capabilities that help organizations deal with the challenges of today’s threat and vulnerability environment.
BENEFITS
NopSec Unified VRM helps organizations discover, prioritize, remediate, simulate, and measure their efforts to reduce vulnerabilities. With Unified VRM, organizations can:
- Address the expanding attack surface problem with a view that identifies and grades every asset.
- Deal with increasing vulnerabilities and attacks with many source threat intelligence.
- Cut the noise and streamline action with automated, machine learning-driven prioritization.
- Choose best in breed remediation recommendations tied to vulnerability priority.
- Reduce tool sprawl by connecting many resources into the Unified VRM command and control framework.
- Make good, data-driven decisions on the use of personnel and resources
- Have a single view for mitigation as well as team management
- Track and report in real-time KPIs like MTTR and SLA policy compliance.
KEY FINDINGS – Analysis of Benefits
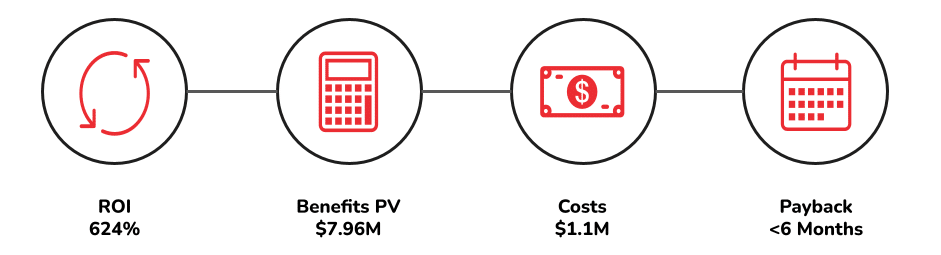
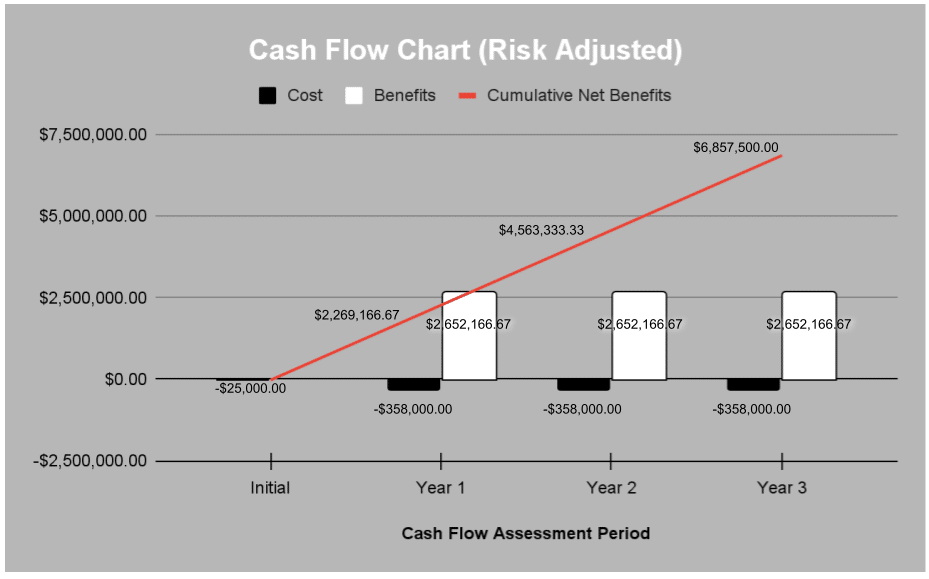
Unified VRM delivered (3-Year Assessment):
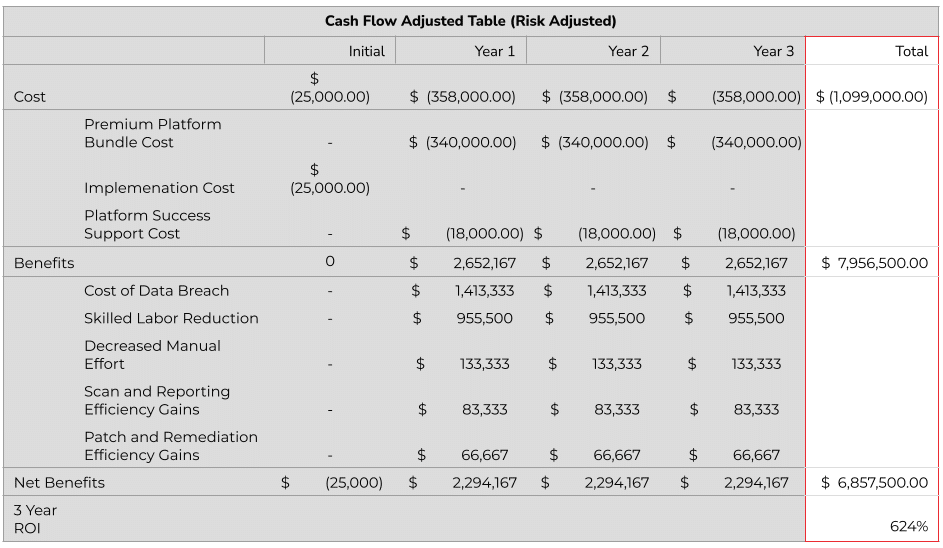
- ROI 624%
- Total Benefits (PV – Present Value) $7.96m
- Cost of a data breach – $4.24m (source: IBM Cost of a Data Breach Report, 2021)
- Skilled labor reduction by 70% – $2.87m (10.5 FTE at $130k/year – $4.1m x 70% is $2.87m)
- Decreased manual effort – $400k
- Scan and reporting efficiency gains – $250k
- Patch and remediation efficiency gains – $200k
- Costs $1.1m
- Initial implementation costs – $25k (One time Premium platform implementation)
- Unified VRM platform costs – $340k/year (Premium platform package with 20k assets at $16.99 per asset)
- Annual platform success support – $18k/year (Premium platform support)
- Payback <6 months
Additional Benefits:
- 33% less time spent in manual data triage
- Noise reduction of 40% post prioritization
- 98% efficiency in risk prioritization compared to CVSS
- 65% reduction in MTTR (Mean-Time-To-Remediate) Metrics
- 80% increased accuracy in asset prioritization
- Enhanced collaboration and communication between security and IT remediation teams
- 67% of customers improved their RBVM program Maturity Score from 2 to 4 within 6 months of product implementation
- 45% less time spent in threat intel research and vulnerability correlation
- Improved productivity via native integrations with customer’s technology ecosystem
- 45% in time savings in producing business-line reports/metrics to the remediation team and to the board/executives
Assumptions:
- Every enterprise will experience a data breach within 3 years (⅓ per year); the cost of a data breach is $4.24m (source: IBM Cost of a Data Breach Report, 2021)
- Only 44% of organizations use automation to assist with vulnerability management and patching (Ponemon Study – Costs and Consequences of Gaps in Vulnerability Response)
- On average medium-to-large enterprises only have 5 FTE (Full Time Employees) to support their vulnerability mitigation efforts
- Industry benchmarks state that over 400 hours per week (or 10.5 FTEs) are required to work on detection, remediation, documentation, reporting, coordination between teams (Ponemon Study – Costs and Consequences of Gaps in Vulnerability Response)
- Average security operations employee is $130k (salary x 1.2 benefits multiple)
- 70% time savings can be realized with full automation after a gradual implementation process taking less than 3 months to implement
- It takes an enterprise an average of over 6 months to patch 90% of devices against vulnerabilities in 12 enterprise applications and over 9 months to patch the entire server population (Symantec, 2019)
- On average server applications remain vulnerable for 7.5 months (Symantec, 2019)
- On average 6 hours are spent on non-urgent patches and 12 hours for emergency patches (HPE)
- 51% of operators highlight that manual processes are an obstacle to timely vulnerability remediation (Ponemon Report on The State of Vulnerability Management in the Cloud and On-Premise, August 2020)
- 99% of vulnerabilities exploited are known by security and IT operations professionals at the time of the incident (Gartner)
- Over half of enterprises are unable to track whether vulnerabilities are patched in a timely manner, do not prioritize the need for downtime that is required to conduct patching, do not have enough resources to keep up with the patching that is required, and do not have a common view of applications and assets across security and IT operations teams (Ponemon Report on The State of Vulnerability Management in the Cloud and On-Premise, August 2020)
The average backlog of over 55,000 identified vulnerabilities (Ponemon Report on The State of Vulnerability Management in the Cloud and On-Premise, August 2020)
CONCLUSION
NopSec prioritizes the vulnerabilities that impact one’s environment the most. They provide ML-based prioritization to enable data-driven conversations and collaboration among vulnerability management, IT, and development teams. NopSec helps security professionals simplify their work, effectively manage and prioritize vulnerabilities, and make better-informed decisions.
NopSec’s Unified VRM is an innovative threat and vulnerability management solution that addresses the need for better prioritization and remediation of security vulnerabilities in a single platform.
Learn how to maximize your return on investment and request a demo today.