NopSec Cloud Security Module
- Jul 13, 2016
- Guest Author
Most organizations are currently migrating their computing infrastructure into the public cloud (AWS, Google, Azure) usually embracing a mixed private / public cloud model.
Most SaaS solutions, including NopSec, already base their entire computing infrastructure on public clouds.
This creates a unique challenge in terms of setting up proper vulnerability management processes to address the cloud environment’s peculiarities.
Particularly in the AWS – Amazon Web Services – environment, in order to assess vulnerabilities in the public cloud each vulnerability scan and/or penetration test needs to be cleared with AWS by filling an authorization form in advance. This creates a convoluted administrative process to authorize the scan in advance. One of the situation that AWS is trying to avoid with this is to white-list legitimate traffic in advance that transverse its internal network.
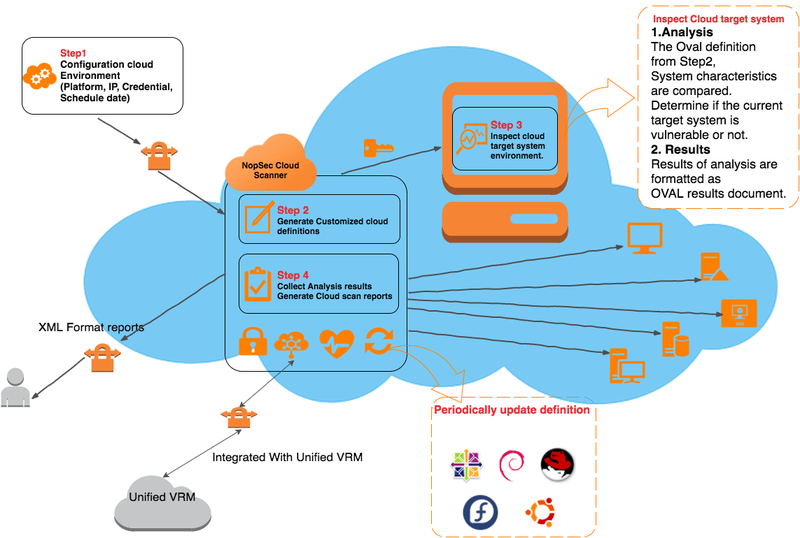
For this reason, NopSec created the Cloud Scanner so that vulnerability management could be performed on the customer’s cloud infrastructure without sending traffic through AWS’ (or other public cloud providers’) networks.
NopSec Cloud Scanner enables customers to assess their cloud environments’ security posture. Cloud agents will be launched on the target cloud instances and evaluate cloud systems against the SCAP (Security Content Automation Protocol) vulnerability content represented by OVAL (Open Vulnerability and Assessment Language) definitions without heavy network traffic that transverses the cloud providers’ network. The completed assessment will return xml-based results including software vulnerability, configuration issues, program or patch existence on any given system. This XML-based report will be then converted in an HTML / PDF human-readable report.
Figure 1. NopSec Cloud Scan workflow
Our Cloud Scan Agent uses an SCAP vulnerability engine to evaluate each component of the SCAP standard, which is based on Extensible Markup Language (XML) and consists of XCCDF, OVAL, Datastream, ARF, CPE, CVE, CWE.
OVAL Definition schema defines OVAL definitions, which contain system configuration information such as operation system parameters, installed software application settings, and other security relevant configuration values in XML.
The following table is description of elements, child elements, attributes and Type of OVAL definitions.
Table 1. OVAL Element Dictionary
The OVAL Schema is maintained by The MITRE Corporation and developed by the public OVAL Community. The official OVAL Repository is now hosted by CIS. You can download oval definitions from OVAL Website or build custom packages of content from OVALRepo.
Note.
NopSec Cloud Scanner uses customized oval definitions based on Cloud target environments. We use v5.10 including inventory, miscellaneous, patch and vulnerability and automatically update definitions on an ongoing basis.
By Family
Table 2. Statistics definition information by operating systems
By Class
Table 3. Statistics definition information by types
In Unified VRM, Select Cloud: NopSec cloud scan will need specific asset information in order to generate customized OVAL definitions.
Figure 1. Select Asset Type Form
General Information to be filled in: Cloud IP address, OS, Definition file. (Required)
Name, Location: Maintain Asset Information. NopSec Analytics module will provide specific results based on asset location, name, and Operating system.
Business Risk Factor: Set a Business Risk Factor (High/Medium/Low).
NopSec Remediation will prioritize your security vulnerabilities based on your business risk factors you assigned.
Click Create
Each created cloud asset is characterized by a “little cloud” icon near the asset name.
Figure 2. Create Cloud Asset Form
Figure 3. Cloud Asset Information in Asset Table.
—
Note.
You need to deploy a cloud scanner manager in your cloud in the form of NopSec maintained AMI. This is for now available through AWS. It will soon be available for Google Cloud. It will communicate back with Unified VRM for scheduling, progress checking, update definitions, and report gathering.
Click Schedule Scan
Select Schedule Cloud Scan
Cloud Scan Form consists of four steps and one scan form summary page. You can move back and forward each step in order to change configurations.
Provide a Scan Name, the date and time for when the scan should begin and if the user has requirements for recurring scans, set the scan recurrence period. Options for recurrence are Daily, Weekly and Monthly.
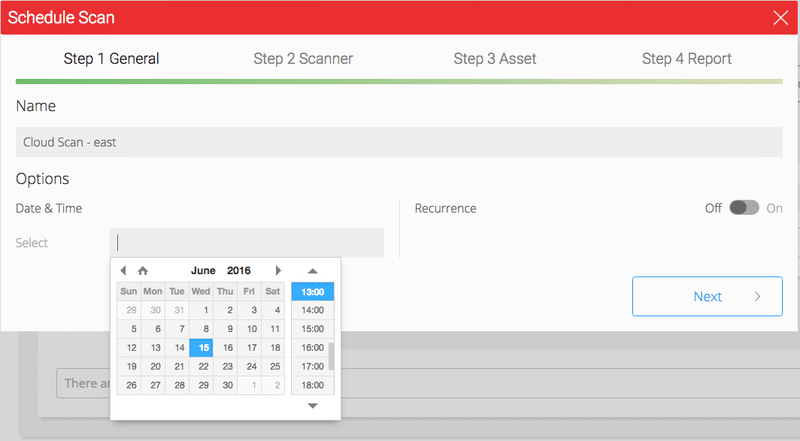
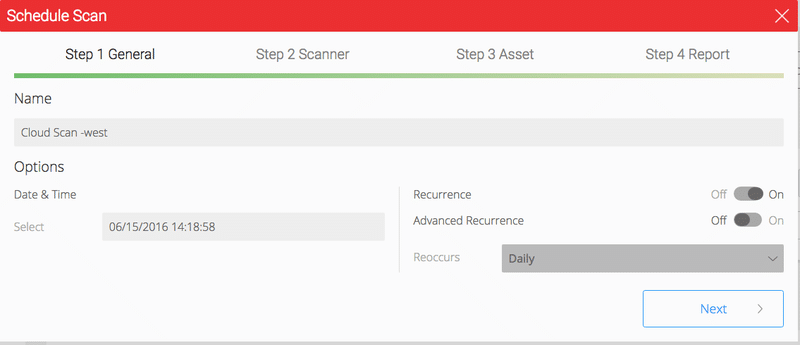
Figure 8. Schedule Scan Step 1 with Advanced Recurrence
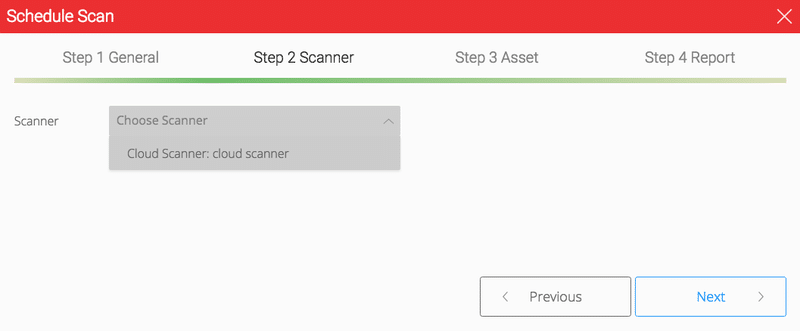
You will be able to check a scanner condition before you create a schedule scan when you select a scanner. (Depending on network condition, it will take few seconds)
After you built the Cloud scanner manager in your Cloud environment, you should get in touch with NopSec, which will register a new cloud scanner in Unified VRM database.
Select one your cloud asset
You need to provide a login credential either in ID/Password or ID/SSH private key format.
Our cloud scanner will generate a specific definition based on the asset system information you provided and will access to your cloud system and launch a cloud scan agent.
In the initial Cloud Scanner release, since most of the cloud instances operating systems are based on various Linux OS flavors, for now the cloud scanner only supports those. Going forward we will enhance the cloud scanner to support Windows systems as well.
Figure 10. Schedule Scan Step 3
The scan duration will vary but it will not be more than few minutes long.
This will automatically generate PDF Format Vulnerability Report.
Check My Report menu, when your scan is done.
Figure 11. Schedule Scan Step 4
Your schedule scan form will be verified before the scan begins.
Figure 12. Scan Summary
You will be able to check your scheduled scan status, your scan asset information, schedule date, and so on. Once you see status Audit Complete, it will automatically generate tickets, reports and update risk scores (Asset, Asset Group, Modules and overall Grade).
Figure 13. Cloud Scan Table
After Scans have been completed, tickets will automatically be opened for the vulnerabilities discovered ranked by priority.
Figure 14. Cloud Scan Ticket Management Table
By Clicking on a ticket record, you can see further details on the ticket including the details on the vulnerability, associated exploits and/or malware(if it exists for that vulnerability), patch and remediation information and references. The following pictures are an example of one such ticket:
Figure 15. Ticket Details
Note.
Automation:
You do not need to close individual tickets. For every scan on an asset, if the scanner detects that the vulnerability has been remediated, the corresponding ticket will be closed automatically.
Integration:
Using Unified VRM’s RESTful APIs, you can establish a bi-directional workflow with their existing ticketing systems. This helps reduce the learning curve in adoption without disrupting existing workflows. You can also use “Generate External Ticket” for an importable CSV format file into their ticketing system.
Documentation on the API can be found here: https://nopsecvrm.docs.apiary.io/#
This is a sample of a Report generated by the Cloud Scanner and its table of contents.
Figure 16. Cloud Scan Report Table
Figure 17. Report Content
Unified VRM Analytics module leverages vulnerability and tickets data from across all the modules the user has subscribed to and correlate that vulnerability and tickets information with external vulnerabilities, threats, malwares and patching feeds to provide the user actionable security intelligence. This enables you to proactively protect yourself and take action against threats and vulnerabilities before potential severe business impact would strike the organization. Using Analytics, you can close the window of exposure and significantly lower the risk by applying remediating controls to vulnerabilities rated by severity in context of your business asset classification.
Figure 18. Scan Vulnerability Analytics
For more information on The NopSec Cloud Scanner contact us for a free demo.