CVE to KB: How to Correlate CVE Vulnerabilities to KB Patches via Automation
- Feb 18, 2019
- Guest Author
Here at NopSec our goal is to provide the most intelligent, automated way of managing cybersecurity risk in enterprise environments. One of the biggest challenges we face in automating vulnerability prioritization and remediation is finding and applying the right data at the right time. Our integration with Microsoft System Center Configuration Manager (SCCM) is a perfect example of how having the right data can enable the automation of everyday cybersecurity tasks.
Microsoft SCCM is a tool used by system administrators for software distribution and patch management in large enterprise IT environments. By integrating with SCCM, we automated the process of identifying and deploying the patches necessary to resolve existing vulnerabilities in an enterprise environment. In this blog post, I will explain how we used publicly available Microsoft patch data to automatically identify the patches necessary to resolve existing vulnerabilities detected by our various supported vulnerability scanners.
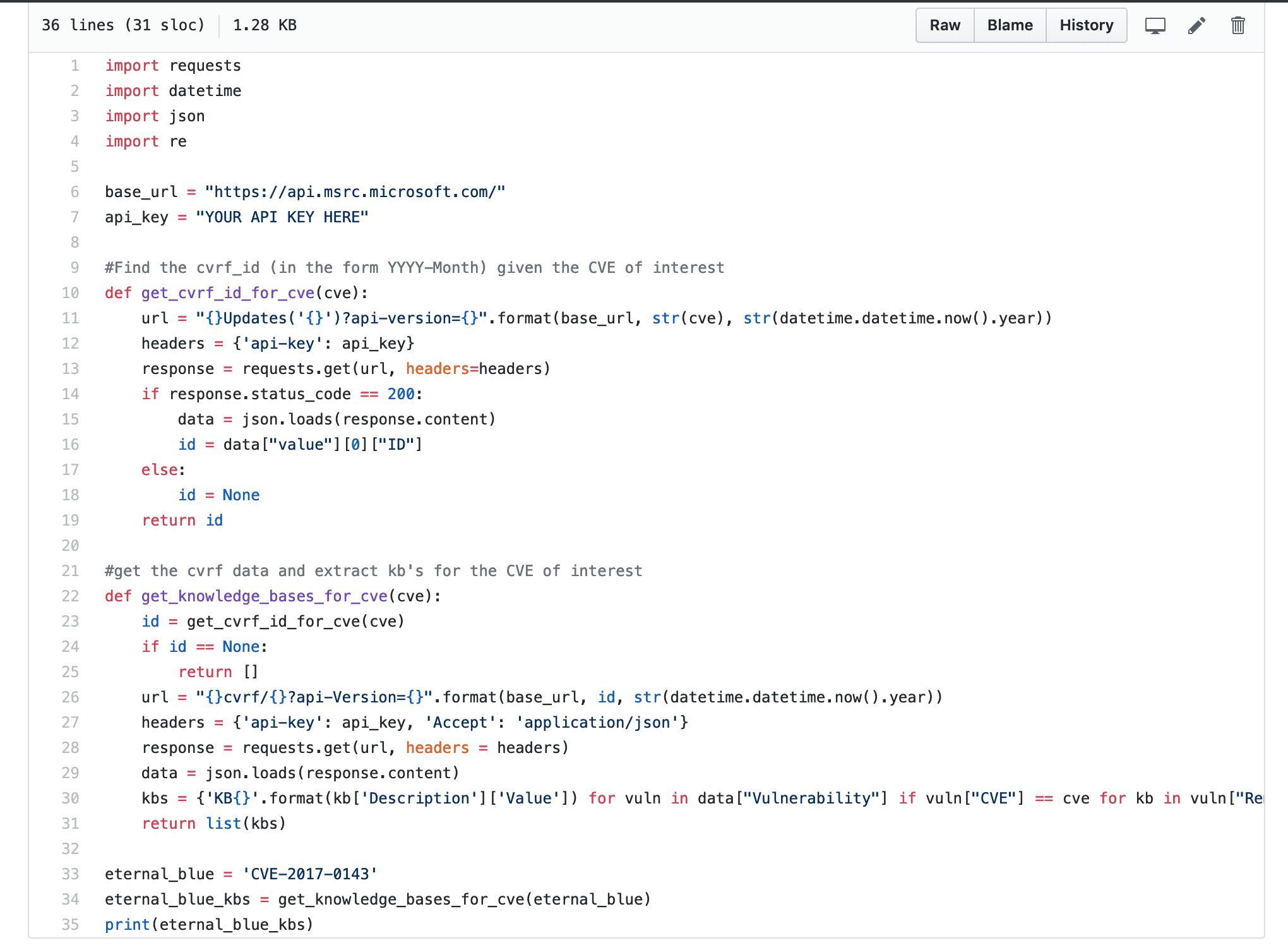
Cyber Security Vulnerabilities are usually identified using its unique CVE (Common Vulnerabilities and Exposures) number, and this is what vulnerability scanners use when specifying detected vulnerabilities. Microsoft provides patch information in the form of Knowledge Base (KB) Articles that are associated to one or more CVEs. Given a CVE number from a vulnerability, we need to be able to identify all the knowledge base articles ID’s associated with that CVE. We will later use those Knowledge Base Article IDs to find and build a patch package in Microsoft SCCM. Luckily, the Microsoft Security Update Guide provides patch information in CVRF (Common Vulnerabilities Reporting Framework) format, which makes it easy to build a lookup table of knowledge base articles given a unique CVE number.
Below is a simple Python script to retrieve patch data from the Microsoft Security Update API for Eternal Blue (CVE-2017-0143) in CVRF format and extract all Knowledge Base Article ID’s associated with it. You will need your own API key which you can get by signing up for the Developer API here.
*You can find the code here.
After correlating vulnerabilities to patches (MS to KB), the next step is downloading the patches to your patch management solution. This automation will save time from the manual correlation and downloading, which enables you to reduce your mean time to remediation (MTTR).
Gain better insight into your organization’s risk and prioritize vulnerability remediation based on the unique content of your environment with NopSec Unified VRM. Schedule a demo today.