ThreatForce: The Vulnerability and Threat Search & Correlation Engine
- Apr 24, 2015
- Guest Author
NopSec has just launched ThreatForce – a flagship security vulnerability search engine that makes it easy for security analysts to gain a consolidated view of vulnerabilities by CVE correlated with threat, exploit and other public sources.
NopSec ThreatForce offers a summary and detailed results with correlation and links to:
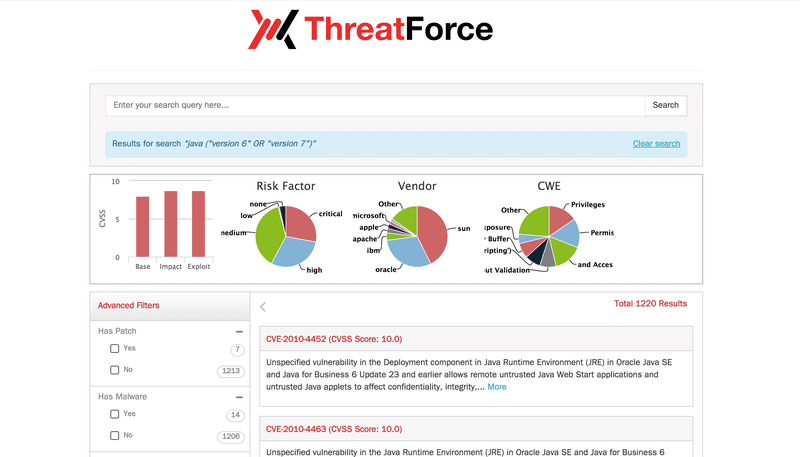
On the left-hand side of the result page you can see the advanced filters that help narrow down the orginal query results. Some of the filters that can be applied include:
As a use-case / example, you can plug in the following search string to find all the vulnerabilities in JAVA related to version 6 and 7.
The ThreatForce search engine and backend database is updated on a daily basis. More details and correlations will be added to the search engine in future releases. We welcome your ideas on additional sources you would like to see included. Send your feedback to info@nopsec.com.
We invite you to take ThreatForce for a spin. Happy vulnerability hunting!!