Threat Exposure Management: The Hacker’s Approach to Vulnerability Risk Management
- Sep 28, 2018
- Guest Author
IT Security Teams spend most of their time putting out fires, and just plain dreading and waiting for the next zero-day attack to happen. They’re also busy applying patches or updating systems — pretty much random tasks they see on their to-do list — probably wondering it it’s even worth spending their time doing tasks X, Y, Z when there are more urgent issue to focus on.
Contrast that to most unethical hackers who lazily send batch email phishing attacks or use bots to poke and prod for vulnerable systems anywhere with just a click of a button, all the while playing video games until they get notifications that an opening’s been found. These malicious hackers have a tried and true playbook that they follow religiously: find an exploit, rely on people’s laziness (system hasn’t been updated in one year!), and send out an attack.
There’s no shortage of data on these attacks: the exploits used, the methods of attack, the vulnerabilities found, etc., and yet instead of being able to use this data to better anticipate and prepare for future attacks, security teams usually just drown in them. All that information and yet no actionable results are found. Or worse yet, a better, more proactive way to manage cyber risks is found, but it’s not sexy enough (and admittedly a little dry and boring) to be worth anyone’s time.
The reality is, 99% of all attacks are due to existing and known vulnerabilities being exploited. Zero-days take the measles 1%, and yet it gets all the attention because it’s the “sexier” of the two. There are three vulnerability management problems that IT Security Teams face, and once it is acknowledged, proper vulnerability risk management can be started. These problems are: Too Much Data, Manual Processes, and Severe Shortage of Talent.
We’ve lightly touched on Too Much Data earlier. The data overload overwhelms teams, not help them. Scanner data is excessive and no actionable information can be gained from it. Threat intelligence data and exploit data rely being correlated to the scanner data, and that takes an enormous amount of time to perform. Add to that the manual processes that need to be performed in order to get something out of the data. Talented security engineers are stuck working on Excel sheets, and even then human error has to be factored in. And that is if you have a security engineer to do just that — unfortunately there’s a severe shortage of cybersecurity talent to begin with.
Now that we’ve pointed out the problems, what then is our proposed solution? Why the hacker’s way, of course! There’s a playbook to follow for an effective to way to defend your data and manager your vulnerability risks — the NopSec way!
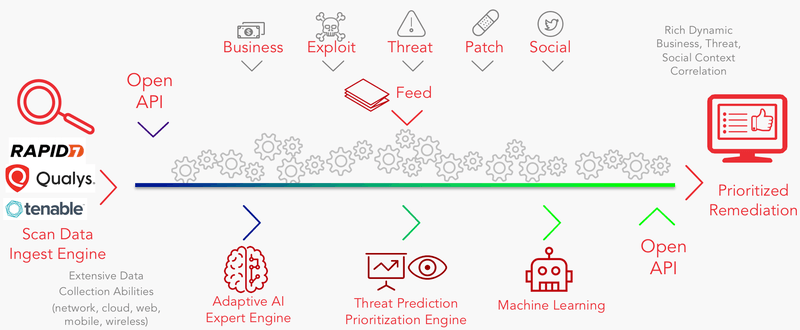
NopSec’s Unified VRM is a platform that helps you manage and prioritize your risks in three steps: 1) Feed your scan data to the platform via the ingest engine; 2) the platform processes your data using its Adaptive AI Expert Engine, Threat Prediction Prioritization Engine, and Machine Learning powers, and 3) You get a prioritized list of your vulnerabilities, so you know which vulnerabilities to remediate first. And done!
Our customers have reported 73% reduction in vulnerabilities within 6 months of using Unified VRM. Not only are they enjoying a harder security posture, but their team is also more productive and more proactive, not to mention a better allocation of resources.
Gone are the days of putting out fires and throwing Hail Marys, hoping that the patch applied is the one that could fix everything. With Unified VRM, you are sure that you’re fixing the right stuff at the right time, and you’re doing it without the stress — you’re doing it with a push of a button with Unified VRM!
To learn more about Unified VRM and all our service offerings, you can contact us here.