Instant Risk Reduction Recommendations to Align Priorities with IT
- Mar 19, 2019
- Guest Author
Snow flurries were a welcome change in New Jersey from last month’s high gust winds. I often multitask my dog walks to start my morning as productively as possible. My marketing colleague Sule joined me and picked up a greek yogurt from Panera. On our short walk back, we figured out what’s most important for today’s offsite, while stepping over recently fallen branches. Sule, and I were pumped to get started when we arrived back – my dog was ready to nap. This instant feedback loop enabled me align priorities across teams, and this holds true in Vulnerability Management with InfoSec and IT.
InfoSec teams have their own priorities often guided by overarching VM goals. Two goals in enterprise vulnerability management are:
The outcome for either of the above is a list of vulnerabilities.
IT teams prioritize by business revenue or functionality that is needed by their customers right now. This often means developers work on a subset of their application portfolio at any given time. The outcome for this is a list of applications that worked on that change from sprint to sprint.
The priorities of InfoSec and IT often do not align, requiring back and forth. This can be very expensive, especially if InfoSec brings a set of vulnerabilities that are untimely for the IT team, forcing InfoSec to identify a new set of vulnerabilities.
Let’s go through the first goal as an example. Reducing the most critical vulns or assets requires the following steps – I’m abstracting here, folks.
The combined steps above take about an hour at best to do manually. About the same amount of time applies for reducing risk by maximizing attack surface.
In a manual process, almost all these steps are repeated for each alignment. The reality can be further delays as these conversations tend to require synchronous conversations between two independently overloaded teams.
By automating the manual steps, IT and InfoSec can have instant collaboration. This means one conversation to create a joint commitment that aligns to both team’s processes. This results in:
Unified VRM provides the above benefits with its latest release by automating the manual steps to enable to reduce risk by reducing most critical vulns or assets and reduce risk by maximizing impacted attack surface.
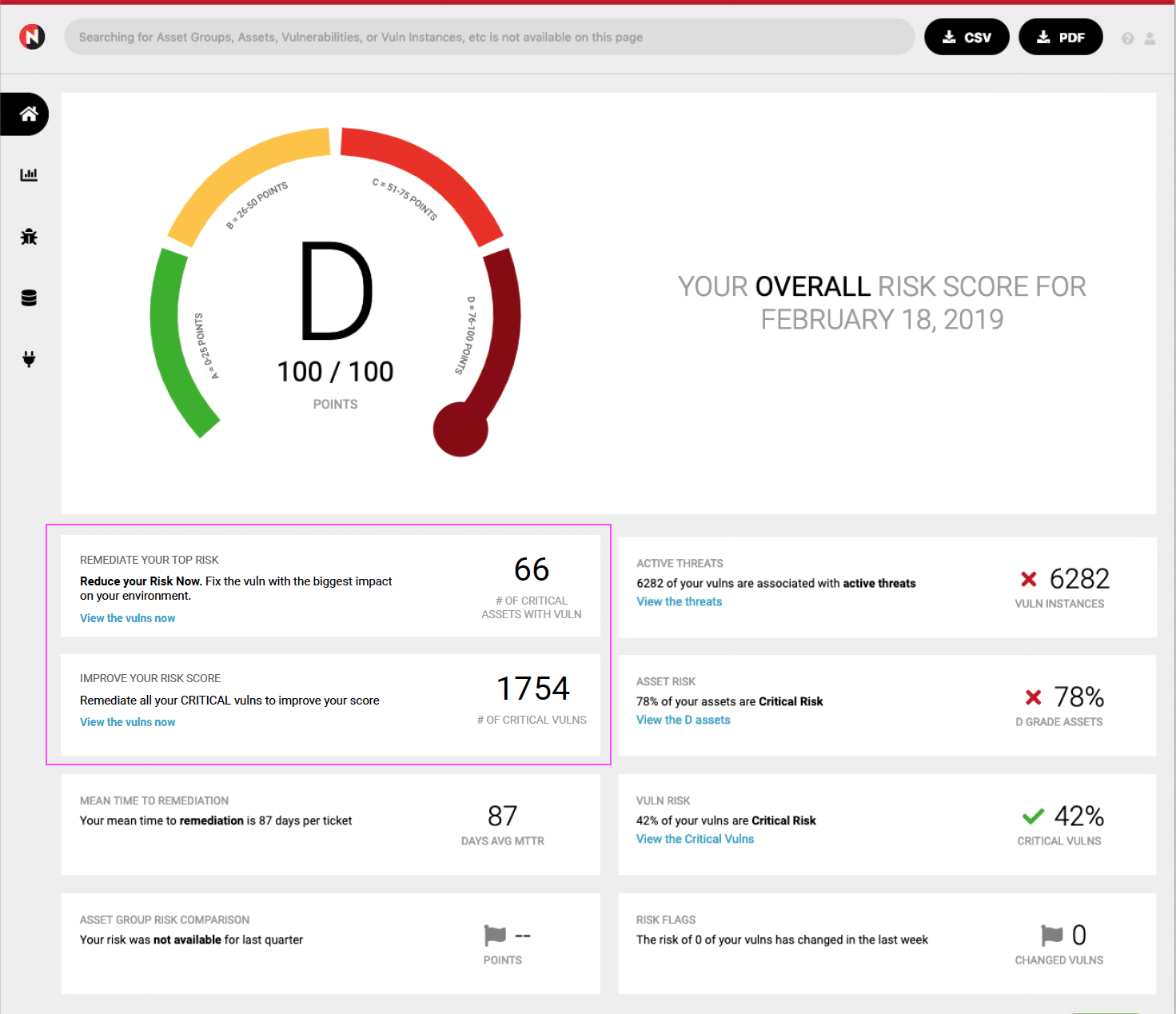
Improve My Risk Score Recommendations
The Improve My Risk Score feature will highlight the best route to improving your risk score. On the dashboard it will show the number of vulnerabilities that can be remediated to improve your score to the next letter grade. Drilling into it will lead to an exact list of those vuln instances, including the information about the assets they are on.
Reduce My Attack Surface Recommendations
NopSec’s Reduce My Attack Surface feature will allow you to identify the most important vulns to focus on. It will highlight the most critical and prevalent vulnerability in the environment. That vulnerability will be the one with the worst risk score that can be found on the highest number of critical assets
Share your thoughts in our community!