Go party with the #DevOps
- Apr 09, 2015
- Michelangelo Sidagni
As part of the DevOps movement, it would be desirable to scan your web application for security vulnerability as part of the Continuous Integration loop or the minute a code change is detected. Now it’s possible with NopSec Unified VRM Web Application module linked API.
With the current release of Unified VRM – 3.4.7 – customers can call our RESTful API to automatically scan their web application assets based on a certain trigger event, such as:
These kind of functionalities are part of NopSec campaign to integrate security operations and DevOps.
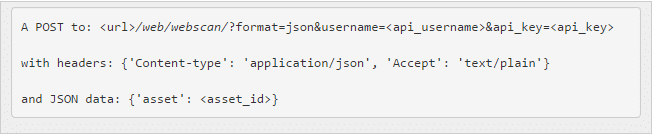
The REST API call is structured as such:
Obviously the REST API call include a special client’s username and the assigned API key and the headers above. The Asset ID can be obtained using the call referenced in Unified VRM API reference on https://nopsecvrm.docs.apiary.io/#.
An example of a python script to invoke the API could be:
As you can see the automation can be pushed by creatively using the available RESTful API calls.
Now, security professional go talk to your DevOps guy, talk about this new capability and then go have a beer with him.