Fighting the War with the Right Weapon: Countering Complexity with Automation
- Jul 19, 2017
- Michelangelo Sidagni
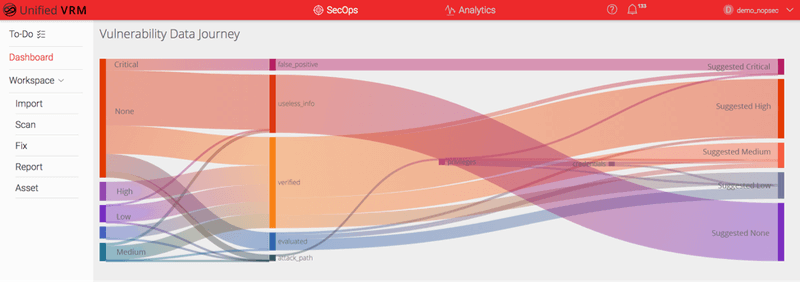
Here at NopSec, we have always been fascinated with automation. It has been a focus of ours since the beginning of our cybersecurity SaaS solution launch, Unified VRM, back in 2012. We first tackled the complexity of correlating several commercial and open-source networks and web application scanner’s results by automating the import of results via files or directly via API. The automation heavy lifting was done by our Expert Engine that allowed us to eliminate duplicates, useless, and redundant information as well as eliminating false positives by unequivocally verifying the targets’ platform and version.
The next logical step in NopSec’s automation journey was to automate and facilitate the IT team’s remediation work through connections between the Unified VRM ticketing platform and other commercial ticketing systems, including Jira, ServiceNow, and Remedy. The automation of the patching for Windows and Unix platforms was achieved through the connection with the Microsoft SSCM patching system and the verified vulnerabilities in Unified VRM so that the applied patches and vulnerabilities could be compared and verified. We enable you to remediate effectively and efficiently. That said, we do not remediate for you. We believe that there should be a separation between the two disciplines.
The next step in NopSec’s fixation for automation was the building of the attack paths. The theory behind this was that every vulnerability that sits on a certain attack path that leads to exploitation, privilege escalation, credentials extraction and ultimately to credentials “spraying” throughout the network should be re-prioritized and remediated with urgency, regardless of its CVSS score.
Unified VRM’s new “E3 Engine,” which stands for “Evaluate, Explore & Enrich,” builds on the same principle of the previous Expert Engine: it takes vulnerabilities – regardless of the scanner that generates them – eliminates duplicates, useless information and false positives. On top of that, it automatically builds attack paths trying to exploit vulnerabilities, escalate privileges, extract and spread credentials until it arrives at compromise of the network Domain Controller(s). It also functions in safe and active mode: in safe mode it does not execute exploits at all; in active mode it only executes exploits deemed safe and stable for execution.
Once the imported or generated vulnerabilities are cleansed, verified and prioritized, each one is correlated with over 40+ unique threat intelligence feeds, including emerging attacks, exploits, malware in the wild, patches, IDS signatures, patches, other vulnerabilities repositories, and social media feeds.
This additional correlation with threat and open source information intelligence helps the engine focus on vulnerabilities that have the potential to become threats if exploited. The last phase of the correlation is to compare this prioritization with your unique business context — the value of your affected asset(s) as defined (manually or automatically) by the organization in terms of Confidentiality, Integrity, and Availability of the Asset (CIA value).
All this processing and automation helps the team evaluating and prioritizing vulnerabilities in their networks and applications so that they can focus on the remedial actions that matter the most for their organization’s risk posture, compliance needs and threat landscape.
To learn more about Unified VRM and E3 Engine, please contact us through this form, email us at hello@nopsec.com or call us at 646-502-7900. Thank you!