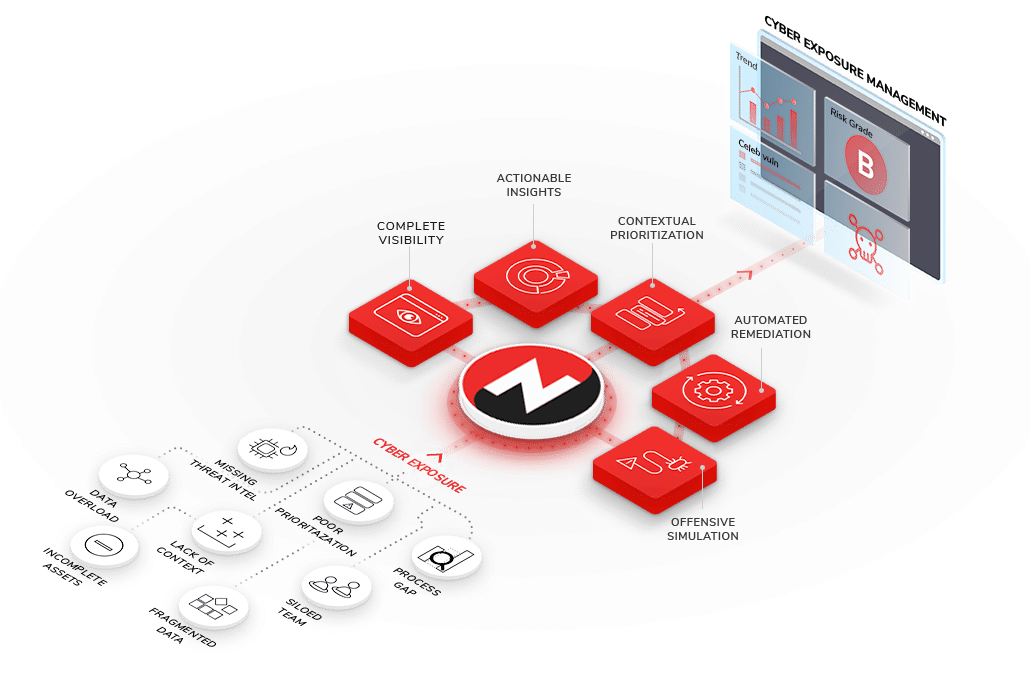
Fix Less,
Secure More
The Cyber Threat Exposure Management (CTEM) platform that SecOps and ITOps love
It's Time to Tame Vulnerability Overload

Your New and Improved Vulnerability Management Program Starts Here
CTEM Improves the Bottomline
-
67%Of customers improved their RBVM program Maturity Score in 6 months
-
45%Less time spent in manual data triage
-
40%Faster identification of critical vulnerabilities
-
75%Reduction in MTTR on highest risk vulnerabilities
Machine-Learning-Based Risk Prioritization
Infrastructure and AppSec Full-Stack Consolidation
Security Program Metrics and ROI Reporting
Remediation Workflow Collaboration and Automation
Machine-Learning-Based Risk Prioritization
Infrastructure and AppSec Full-Stack Consolidation
Security Program Metrics and ROI Reporting
Remediation Workflow Collaboration and Automation
Benefits
-
Make a Real Impact on your Risk Exposure
Leverage machine learning and business context to make better security decisions, faster -
Proactively Reduce your Cyber Risk
Shift your VM team from being reactive to proactive by remediating vulnerabilities before weaponization -
Streamline Security Operations
Optimize Security and IT Operations workflows with automation, not more wasteful meetings -
Aggregate the CTEM Process into a Single Console
Organize all of your security platform data, vulnerabilities, and asset context into one centralized console
Testimonials





-
ResourcesNopSec Unified VRM Security and Governance
-
NewsAWS Risk Management: Unified VRM Available on AWS Marketplace
Leading Vulnerability Risk Management solution delivers enterprise cyber risk visibility that is measurable and actionable through AWS Marketplace. New York,…
-
ResourcesJust in Time Bulletin: CVE-2021-1675